Hackers Using Fake IT Support Calls to Breach Corporate Systems Google – HackRead
Published on: 2025-06-08
Intelligence Report: Hackers Using Fake IT Support Calls to Breach Corporate Systems Google – HackRead
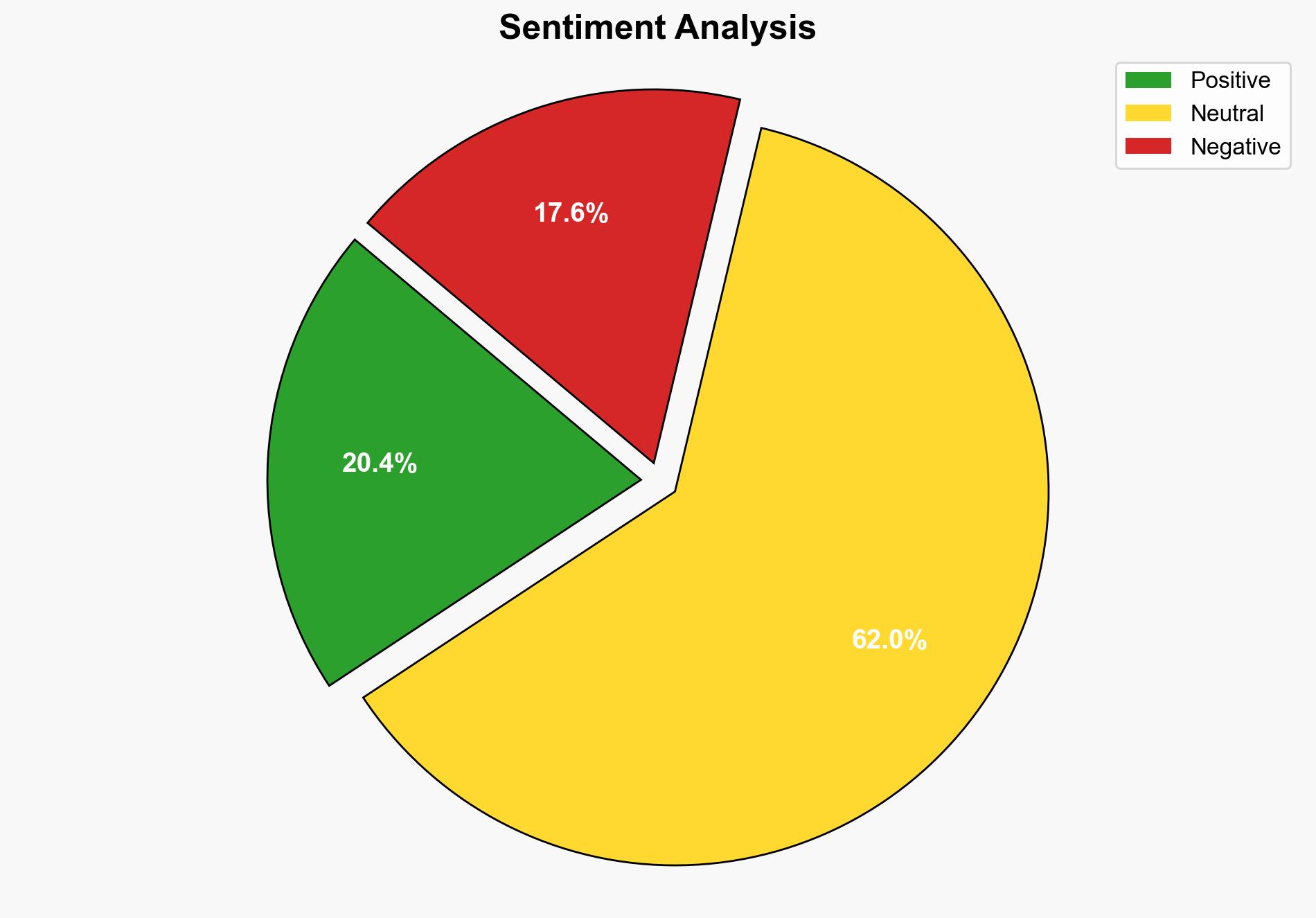
1. BLUF (Bottom Line Up Front)
A financially motivated hacker group is employing voice phishing (vishing) tactics to breach corporate systems by impersonating internal IT support staff. The primary target is Salesforce, a widely used CRM platform. The attackers exploit human error rather than technical vulnerabilities, leading to unauthorized data access and potential extortion. Immediate implementation of enhanced security measures is recommended to mitigate this threat.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulating the tactics of the hacker group reveals vulnerabilities in employee verification processes during IT support calls. This highlights the need for robust authentication protocols.
Indicators Development
Monitoring for unusual access patterns and unauthorized application connections can serve as early indicators of a breach attempt.
Bayesian Scenario Modeling
Probabilistic modeling suggests a high likelihood of data exfiltration attempts following initial access, with potential for subsequent extortion efforts.
3. Implications and Strategic Risks
The attack method underscores a significant vulnerability in corporate IT security reliant on human factors. The potential for widespread data breaches and extortion poses economic risks and could damage corporate reputations. The evolving tactics may inspire similar attacks across other sectors, increasing systemic cyber risk.
4. Recommendations and Outlook
- Enhance employee training to recognize and report phishing attempts, particularly those involving phone calls.
- Implement multi-factor authentication (MFA) across all systems, especially for sensitive platforms like Salesforce.
- Regularly review and restrict access to critical tools and applications, ensuring only necessary personnel have permissions.
- Establish a formal approval process for new application connections to prevent unauthorized access.
- Scenario Projections:
- Best Case: Rapid implementation of security measures prevents further breaches.
- Worst Case: Failure to address vulnerabilities leads to significant data loss and financial extortion.
- Most Likely: Increased awareness and security enhancements reduce successful breach attempts over time.
5. Key Individuals and Entities
No specific individuals are named in the report. The hacker group is associated with the alias “ShinyHunter.”
6. Thematic Tags
national security threats, cybersecurity, corporate espionage, data protection