Biden admin evacuated 55 Afghans on terror watchlist to US during botched withdrawal DOJ watchdog – New York Post
Published on: 2025-06-11
Intelligence Report: Biden Admin Evacuated 55 Afghans on Terror Watchlist to US During Botched Withdrawal – DOJ Watchdog
1. BLUF (Bottom Line Up Front)
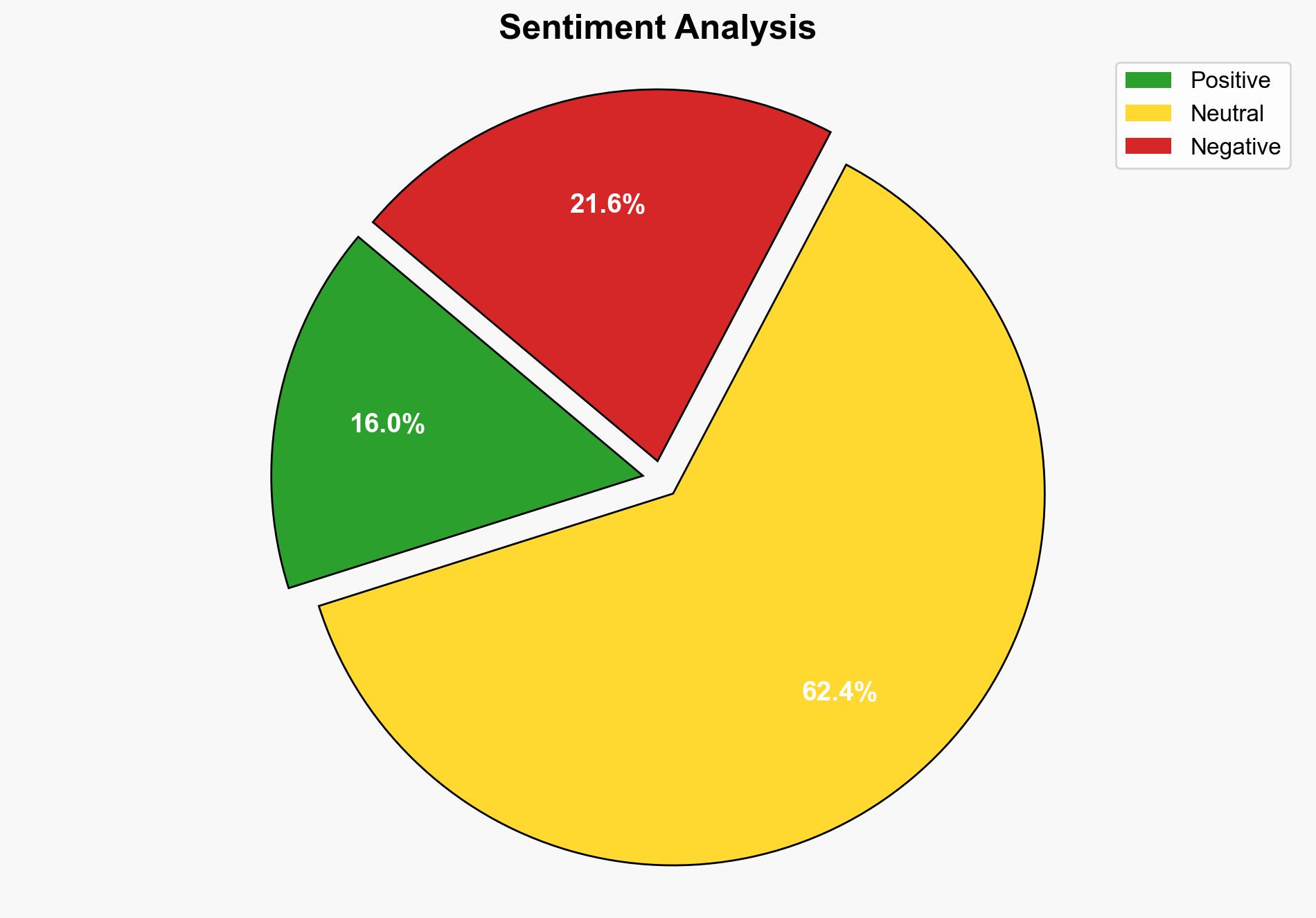
The Biden administration’s evacuation of 55 Afghans on the terror watchlist during the chaotic withdrawal from Afghanistan has raised significant national security concerns. The Department of Justice Inspector General’s report highlights failures in vetting processes, posing potential risks to homeland security. Immediate action is required to enhance vetting protocols and address systemic vulnerabilities.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
ACH 2.0
Utilizing machine-assisted hypothesis testing, the analysis suggests that the oversight in vetting was likely due to the expedited nature of the evacuation process, rather than intentional negligence.
Indicators Development
Monitoring digital radicalization and travel patterns is crucial to preemptively identify potential threats. The integration of these indicators into existing security frameworks is recommended.
Narrative Pattern Analysis
There is a need to analyze ideological narratives that may have influenced evacuees, particularly those linked to extremist groups, to better understand recruitment and incitement dynamics.
3. Implications and Strategic Risks
The entry of individuals on the terror watchlist into the US presents a multifaceted threat, potentially impacting national security, public safety, and international relations. The situation underscores vulnerabilities in current vetting processes and highlights the risk of exploitation by hostile entities during crisis-driven evacuations.
4. Recommendations and Outlook
- Enhance vetting processes by integrating advanced biometric and data analytics technologies to quickly identify potential threats.
- Develop a robust inter-agency communication protocol to ensure timely information sharing and threat assessment.
- Scenario-based projections:
- Best Case: Improved vetting and monitoring systems prevent future security breaches.
- Worst Case: Failure to address vulnerabilities leads to a successful terrorist attack on US soil.
- Most Likely: Incremental improvements in vetting reduce but do not eliminate risks.
5. Key Individuals and Entities
Chuck Grassley, Nasir Ahmad Tawhedi
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus