Microsoft Copilot’s own default configuration exposed users to the first-ever zero-click AI attack but there was no data breach – Windows Central
Published on: 2025-06-13
Intelligence Report: Microsoft Copilot’s Default Configuration Exposed Users to Zero-Click AI Attack – No Data Breach Occurred
1. BLUF (Bottom Line Up Front)
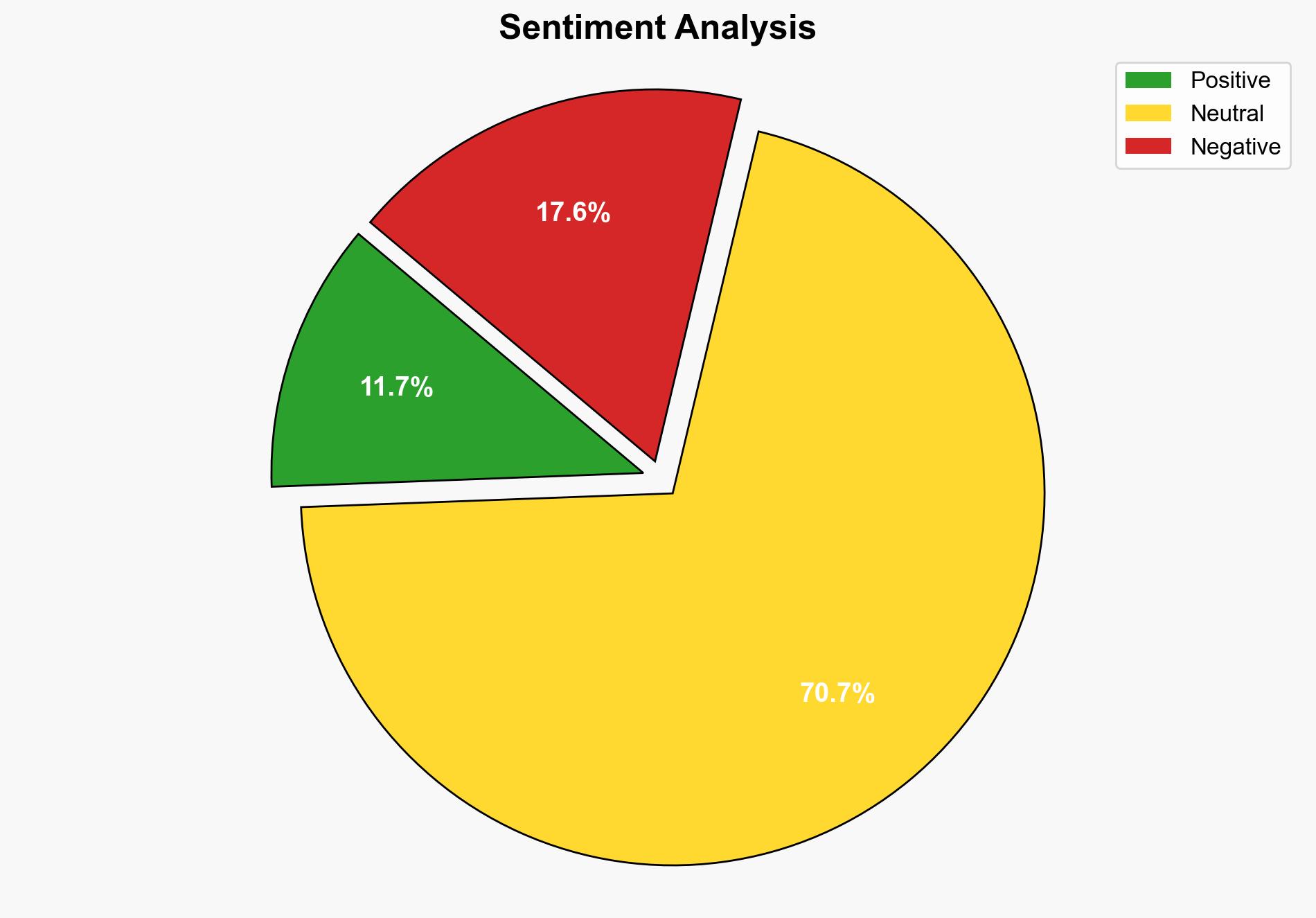
Recent findings revealed a critical vulnerability in Microsoft Copilot’s default configuration, allowing for a zero-click AI attack. Despite the potential for unauthorized access to sensitive data, no data breach was reported. Microsoft has since addressed the vulnerability, mitigating risks through updates and enhanced security measures.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations indicate that cyber adversaries could exploit the vulnerability to access sensitive data without user interaction. This underscores the need for robust security protocols.
Indicators Development
Monitoring systems for anomalies related to AI behavior and unauthorized data access is crucial for early threat detection and response.
Bayesian Scenario Modeling
Probabilistic models suggest a low likelihood of widespread exploitation due to rapid mitigation efforts by Microsoft.
3. Implications and Strategic Risks
The exposure highlights systemic vulnerabilities in AI-driven platforms, emphasizing the need for continuous security assessments. The incident underscores the potential for cross-domain risks, particularly in sectors reliant on AI for data management.
4. Recommendations and Outlook
- Enhance AI security frameworks to prevent similar vulnerabilities in the future.
- Conduct regular security audits and simulations to anticipate and mitigate emerging threats.
- Scenario Projections:
- Best Case: Strengthened security protocols prevent future incidents.
- Worst Case: Similar vulnerabilities emerge, leading to data breaches.
- Most Likely: Ongoing vigilance and updates maintain security integrity.
5. Key Individuals and Entities
Michael Bargury, Kevin Okemwa
6. Thematic Tags
cybersecurity, AI vulnerabilities, data protection, risk management