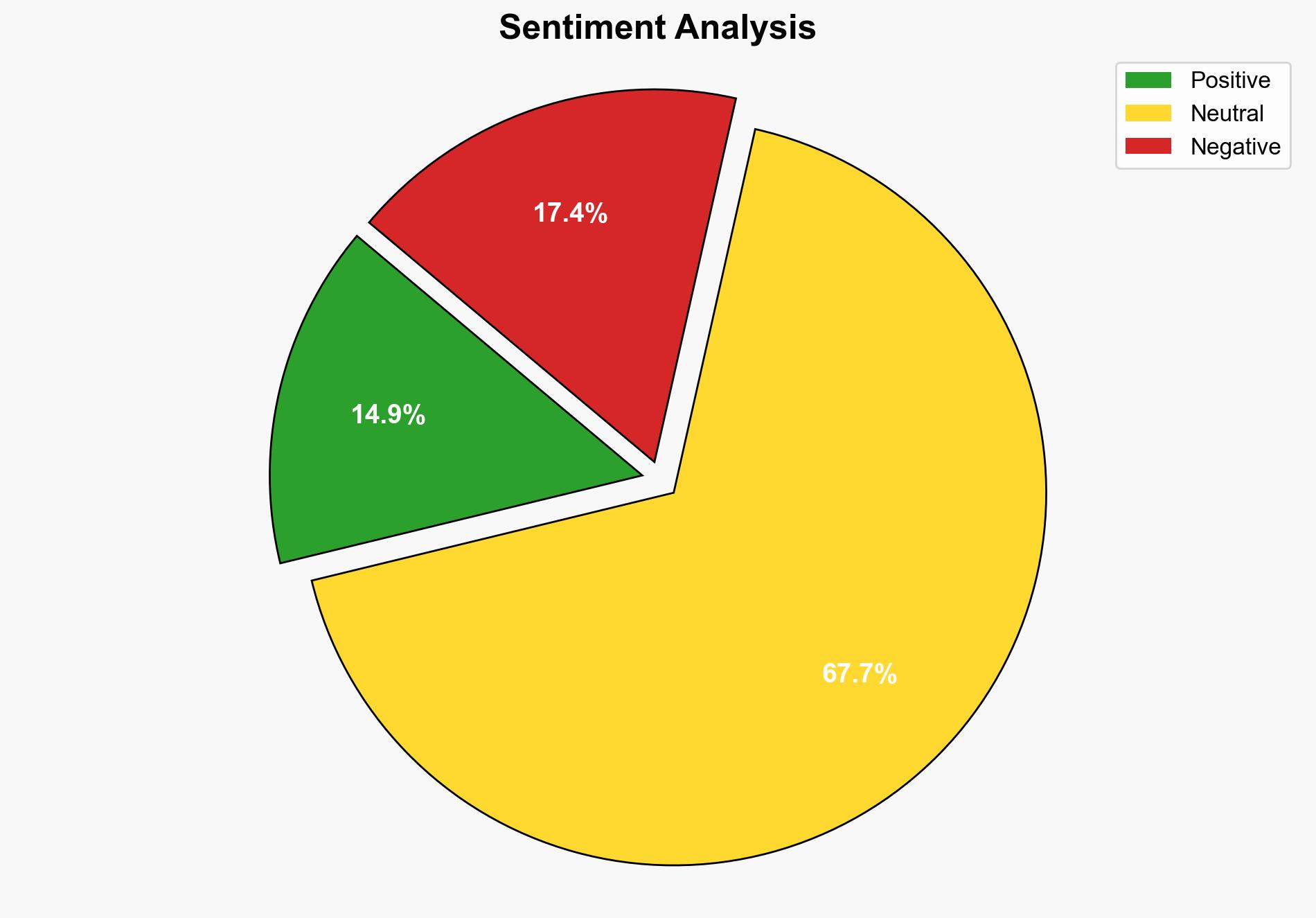
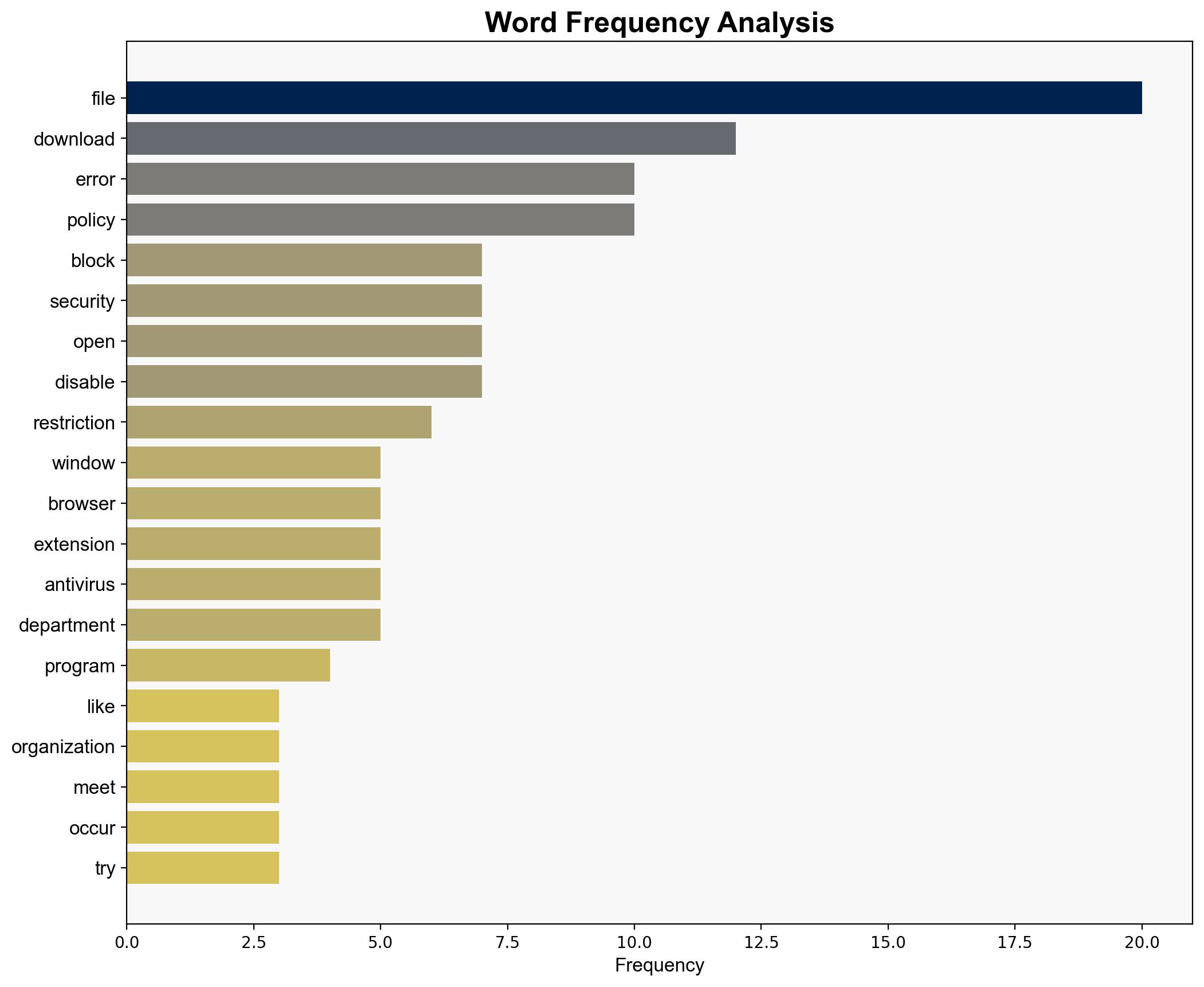
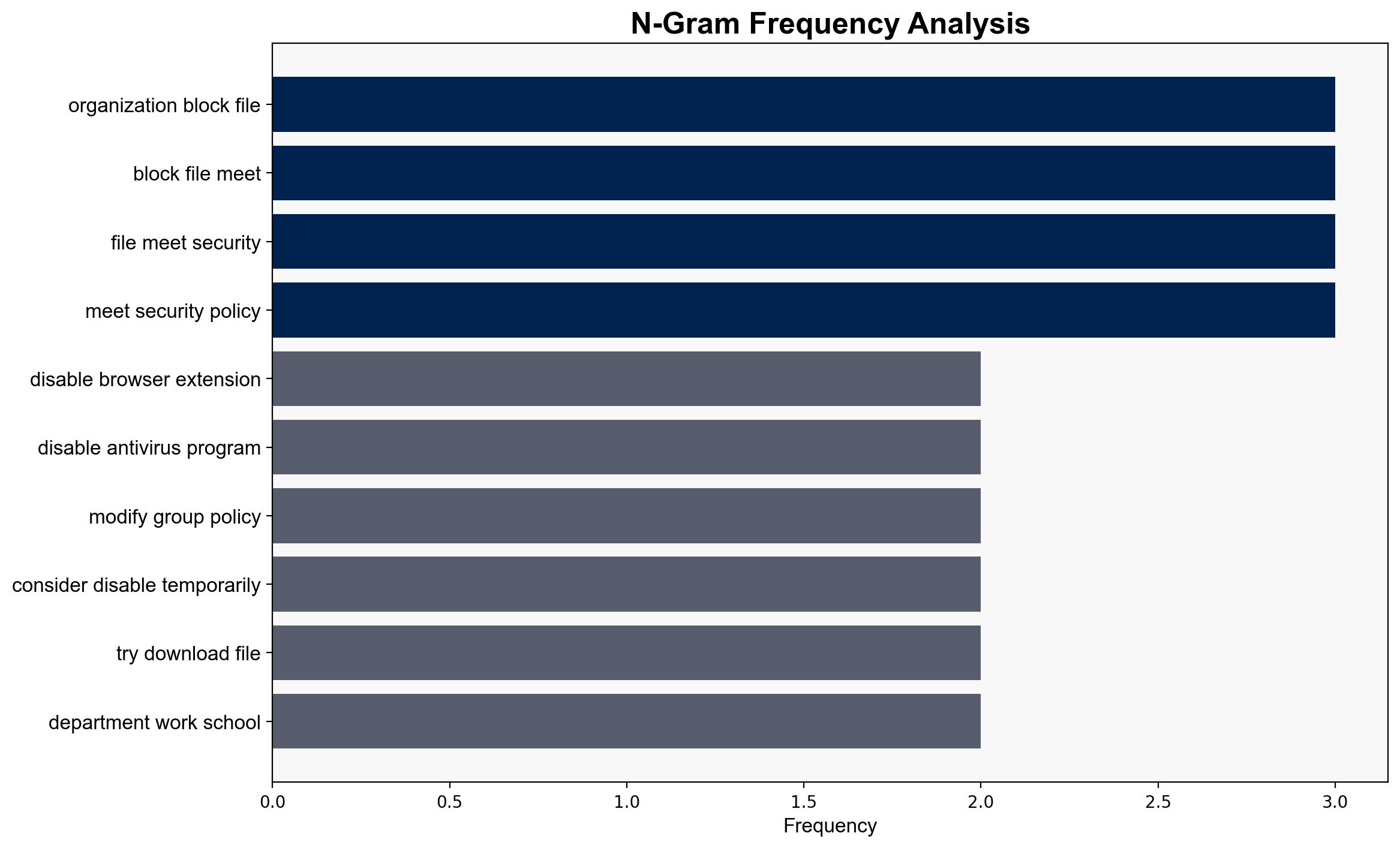
Your organization blocked this file because it didnt meet a security policy – Thewindowsclub.com
Published on: 2025-06-15
Intelligence Report: Your organization blocked this file because it didn’t meet a security policy – Thewindowsclub.com
1. BLUF (Bottom Line Up Front)
The report addresses a common security error encountered on Windows PCs, where files are blocked due to not meeting organizational security policies. This issue often arises from overly strict security settings. Key recommendations include temporarily disabling certain browser extensions, antivirus programs, and modifying group policy settings to facilitate file access. These measures aim to balance security with usability while maintaining network integrity.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulated actions of potential cyber adversaries to identify vulnerabilities in current security policies, suggesting that overly restrictive settings may inadvertently hinder productivity without significantly enhancing security.
Indicators Development
Monitored for anomalies in file access patterns, indicating potential over-blocking by security tools that could be adjusted for improved efficiency.
Bayesian Scenario Modeling
Used probabilistic models to predict the likelihood of future security breaches under current policy settings, highlighting the need for balanced security measures.
Network Influence Mapping
Assessed the impact of security policies on user behavior and network efficiency, identifying key areas for policy adjustment.
3. Implications and Strategic Risks
The current security settings may lead to decreased operational efficiency and user frustration. Overly strict policies could result in users seeking unauthorized workarounds, increasing the risk of security breaches. The balance between security and usability is crucial to prevent potential vulnerabilities while maintaining productivity.
4. Recommendations and Outlook
- Temporarily disable browser extensions and antivirus programs when necessary, ensuring they are re-enabled after file access.
- Modify group policy settings to allow necessary file downloads without compromising security.
- Implement a tiered security approach, adjusting restrictions based on file source and user role.
- Scenario-based projections suggest that a balanced approach will likely enhance both security and operational efficiency.
5. Key Individuals and Entities
No specific individuals are mentioned in the source text. The focus remains on organizational policies and their implications.
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus