New Anubis RaaS includes a wiper module – Securityaffairs.com
Published on: 2025-06-16
Intelligence Report: New Anubis RaaS includes a wiper module – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
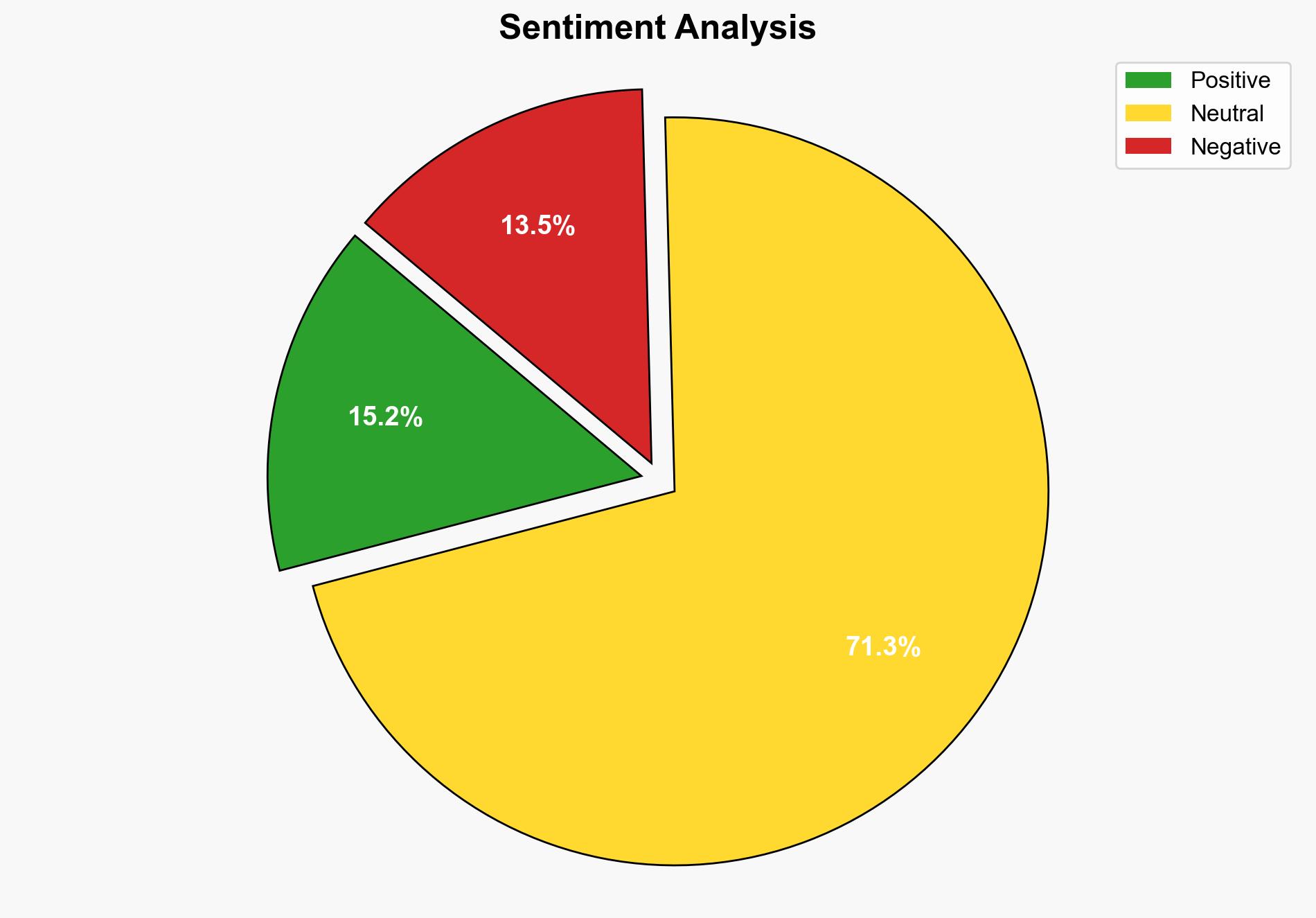
The Anubis Ransomware-as-a-Service (RaaS) has evolved to include a destructive wiper module, significantly increasing the threat level to targeted organizations. This dual capability of encryption and data destruction amplifies pressure on victims to comply with ransom demands. Immediate attention is required to enhance cybersecurity measures and develop strategies to counteract this threat.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
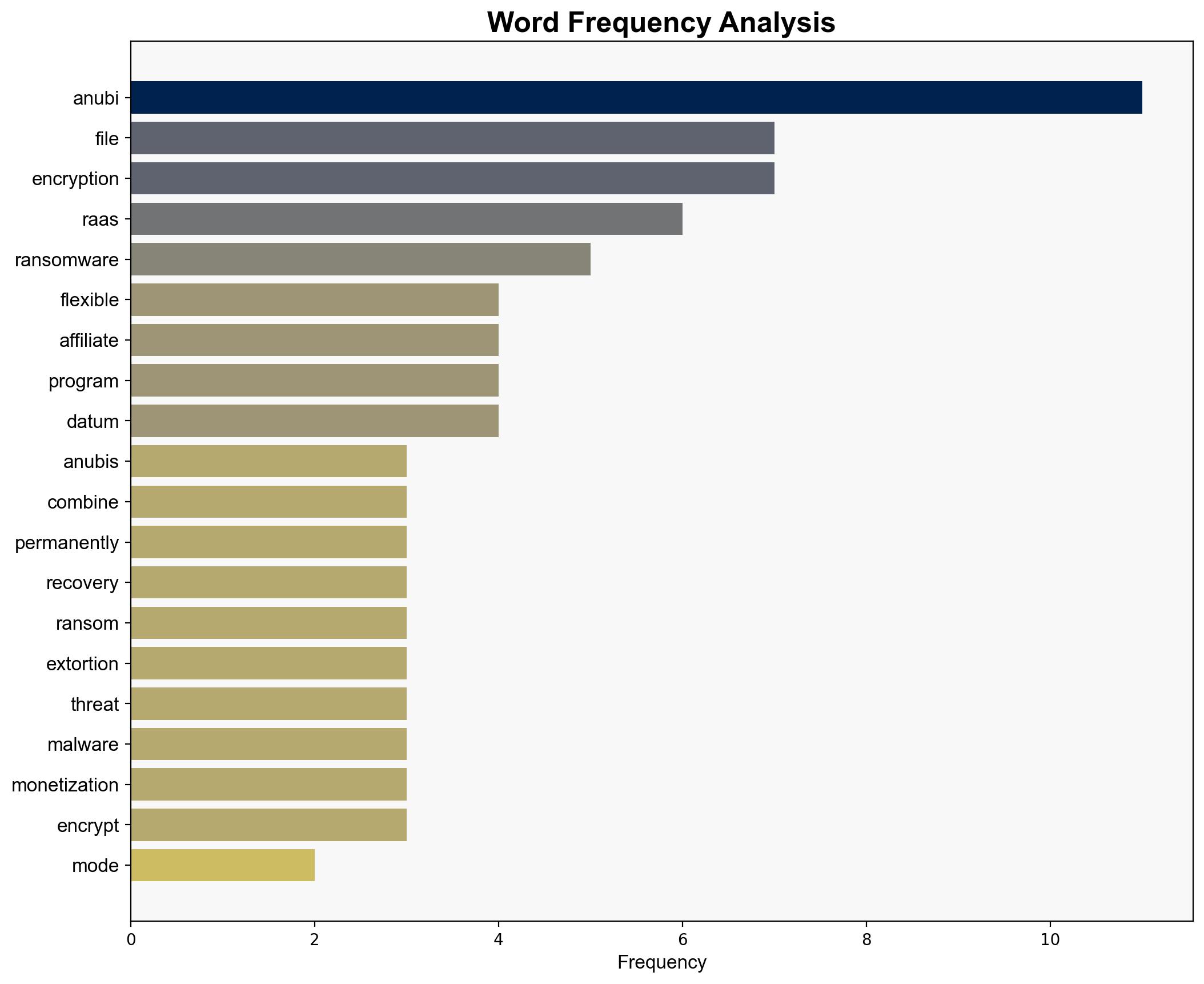
Anubis operates a flexible affiliate program, allowing widespread distribution and adaptation of its ransomware. By simulating potential attack vectors, organizations can better anticipate vulnerabilities and enhance their defensive strategies.
Indicators Development
Key indicators of compromise (IoCs) include the use of elliptic curve encryption and the presence of the Anubis logo on encrypted files. Monitoring these indicators can facilitate early detection and response to potential breaches.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of increased attacks across multiple sectors, including healthcare and construction. This modeling helps predict potential attack pathways and prioritize resource allocation for defense.
3. Implications and Strategic Risks
The integration of a wiper module in Anubis RaaS represents a significant escalation in ransomware tactics, posing systemic risks to critical infrastructure and economic stability. The potential for data destruction increases the urgency for robust cybersecurity frameworks and cross-sector collaboration to mitigate cascading effects.
4. Recommendations and Outlook
- Enhance network monitoring and incident response capabilities to detect and neutralize threats early.
- Implement comprehensive backup and recovery solutions to mitigate data loss from wiper attacks.
- Engage in public-private partnerships to share threat intelligence and strengthen collective defenses.
- Scenario-based projections:
- Best Case: Successful mitigation strategies reduce the impact of Anubis attacks.
- Worst Case: Widespread data destruction leads to significant operational disruptions.
- Most Likely: Continued evolution of Anubis tactics necessitates ongoing vigilance and adaptation.
5. Key Individuals and Entities
Specific individuals associated with Anubis operations remain unidentified. Monitoring cybercrime forums such as Ramp and XSS may yield further insights into key actors.
6. Thematic Tags
national security threats, cybersecurity, ransomware, data destruction, cybercrime