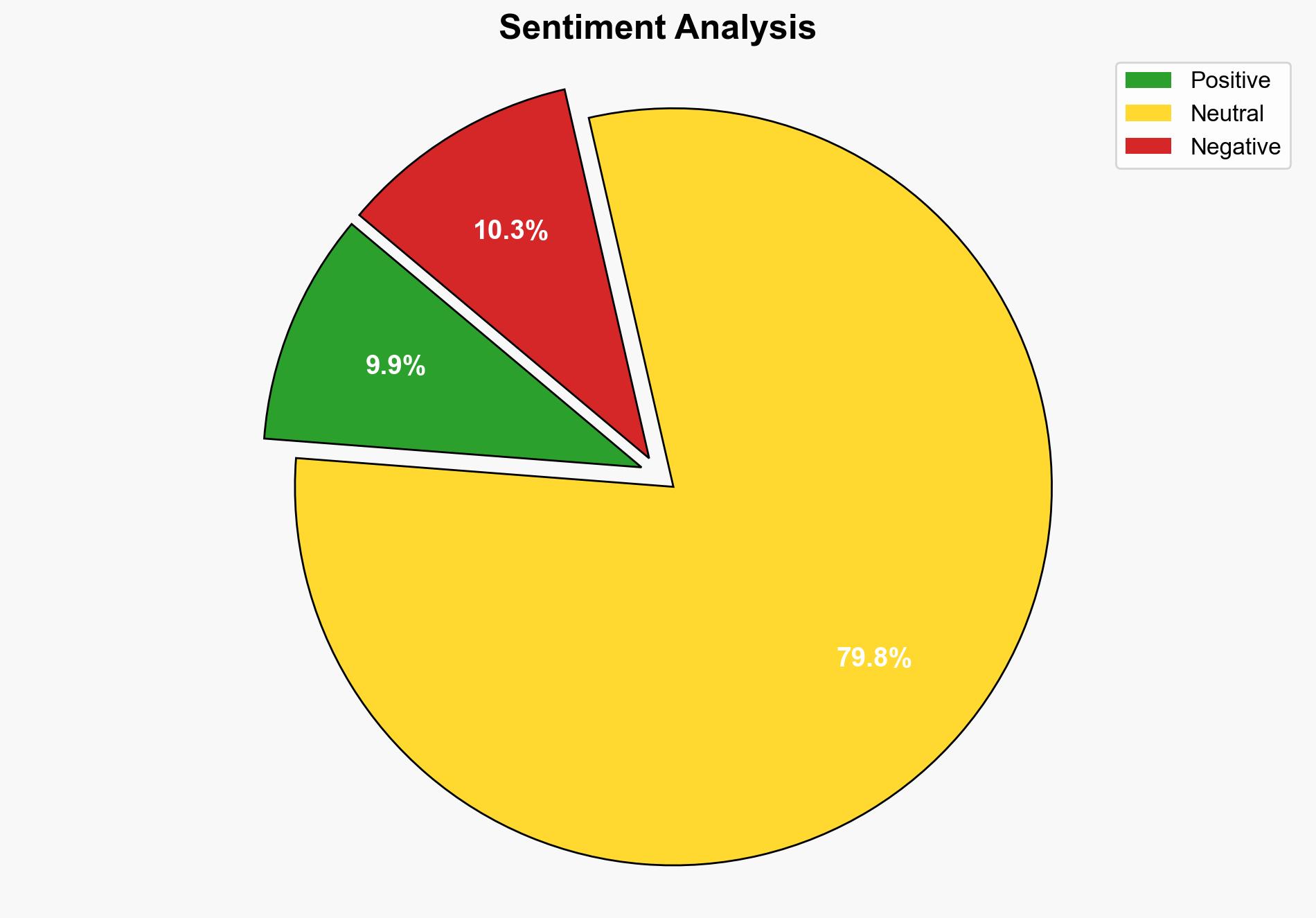
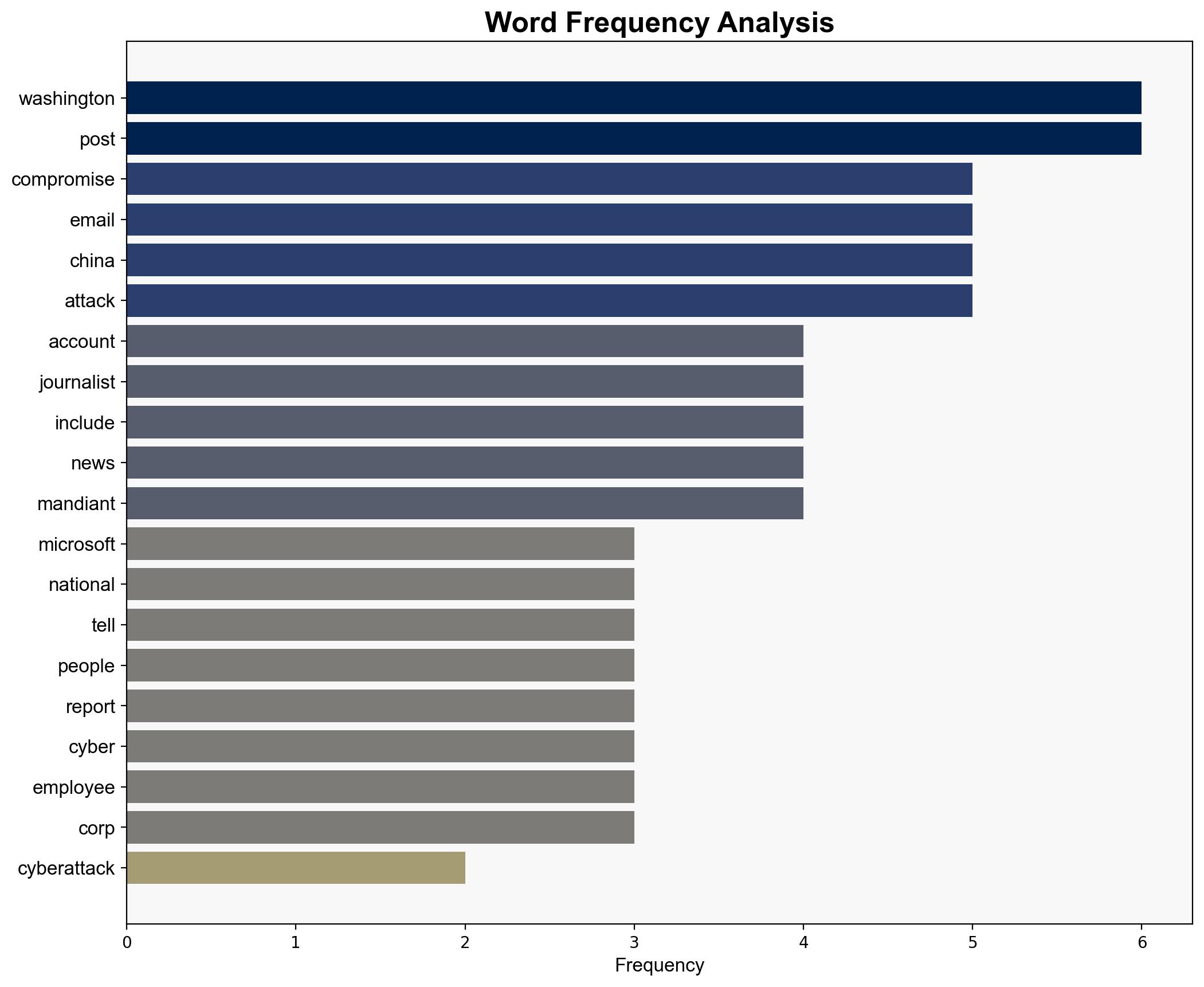
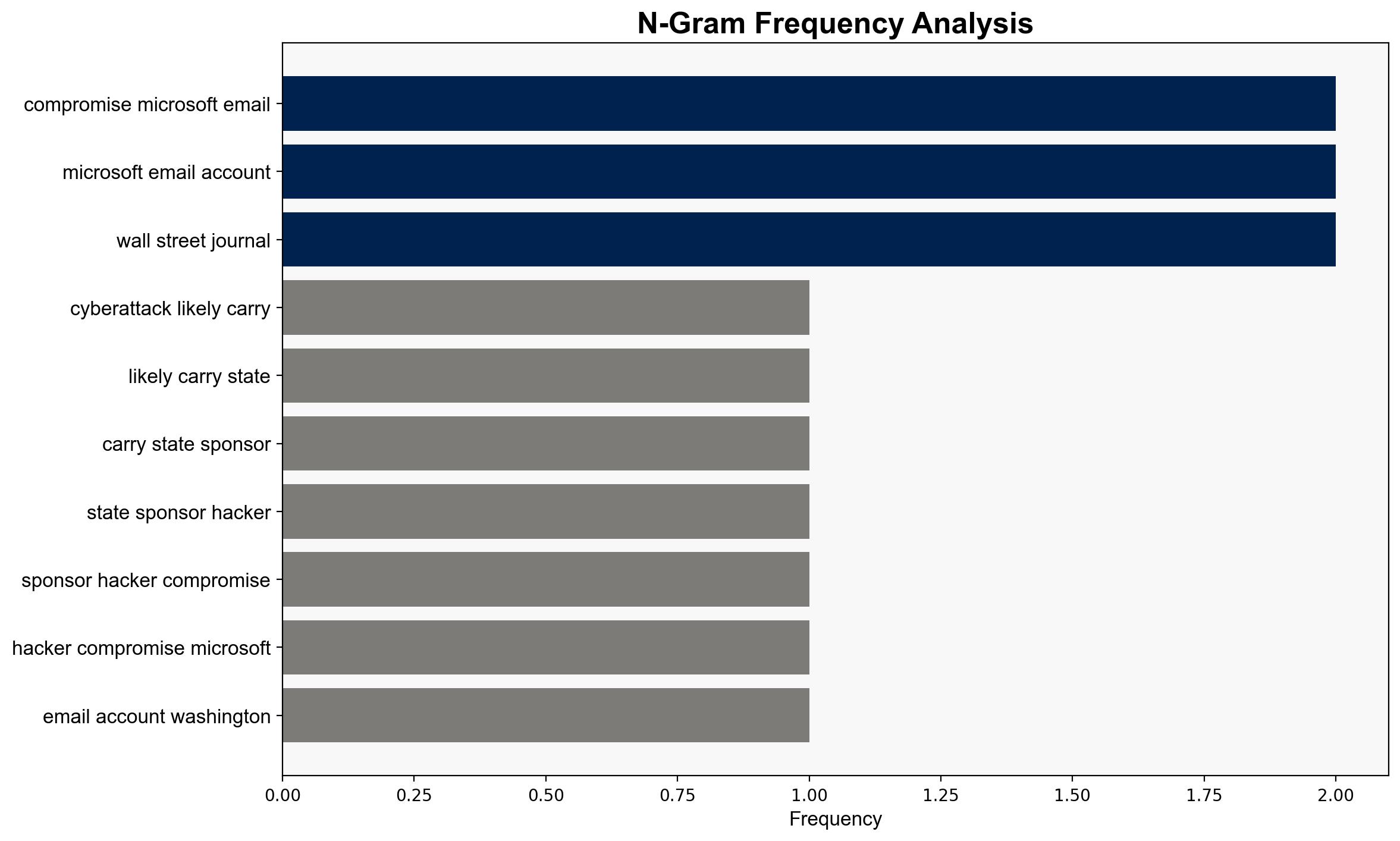
State-sponsored hackers compromised the email accounts of several Washington Post journalists – Securityaffairs.com
Published on: 2025-06-17
Intelligence Report: State-sponsored hackers compromised the email accounts of several Washington Post journalists – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
State-sponsored hackers have compromised the email accounts of several journalists at the Washington Post, likely as part of a cyber espionage campaign. The attack appears to be linked to a nation-state actor, potentially with ties to China, targeting journalists covering national security and economic policy. Immediate measures are recommended to enhance cybersecurity protocols and protect sensitive information.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations indicate that the adversaries likely exploited vulnerabilities in email systems to gain unauthorized access, emphasizing the need for robust security measures.
Indicators Development
Monitoring for anomalies in email access patterns and unusual data exfiltration activities is crucial for early detection of similar threats.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of continued cyber espionage activities targeting media outlets, with potential implications for national security.
3. Implications and Strategic Risks
The breach highlights vulnerabilities in media organizations that could be exploited for intelligence gathering. This incident underscores the strategic risk of state-sponsored cyber activities aimed at influencing public perception and accessing sensitive information. There is a potential for cascading effects on media credibility and national security.
4. Recommendations and Outlook
- Enhance cybersecurity training for journalists and staff to recognize and respond to phishing attempts.
- Implement multi-factor authentication across all communication platforms to reduce unauthorized access risks.
- Conduct regular security audits and penetration testing to identify and mitigate vulnerabilities.
- Scenario-based projections suggest that without intervention, similar attacks may increase, potentially affecting other critical sectors.
5. Key Individuals and Entities
Jeff Bezos, David Wong
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus