Amazon Rebuilt Alexa Using a Staggering Amount of AI Tools – Wired
Published on: 2025-06-18
Intelligence Report: Amazon Rebuilt Alexa Using a Staggering Amount of AI Tools – Wired
1. BLUF (Bottom Line Up Front)
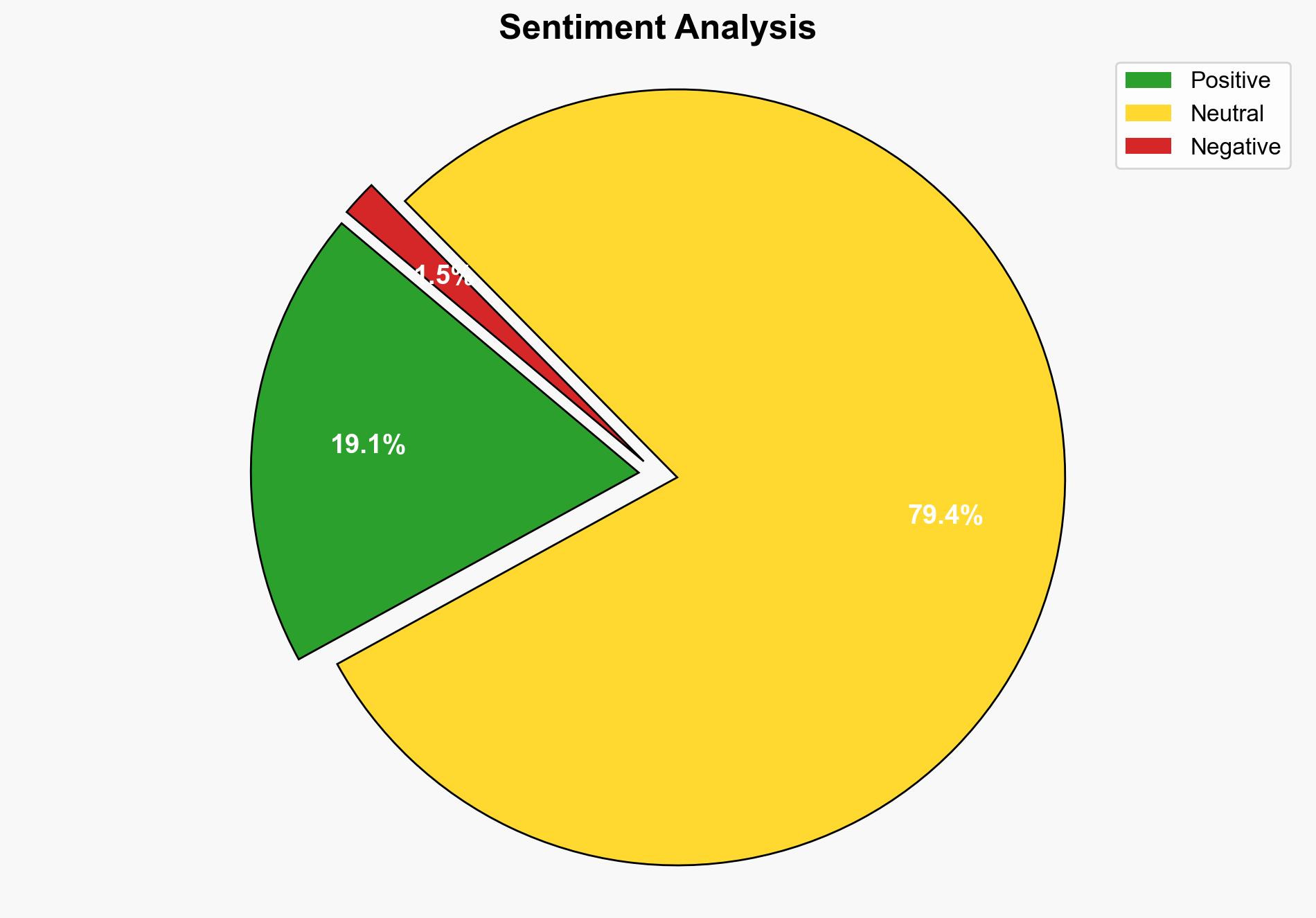
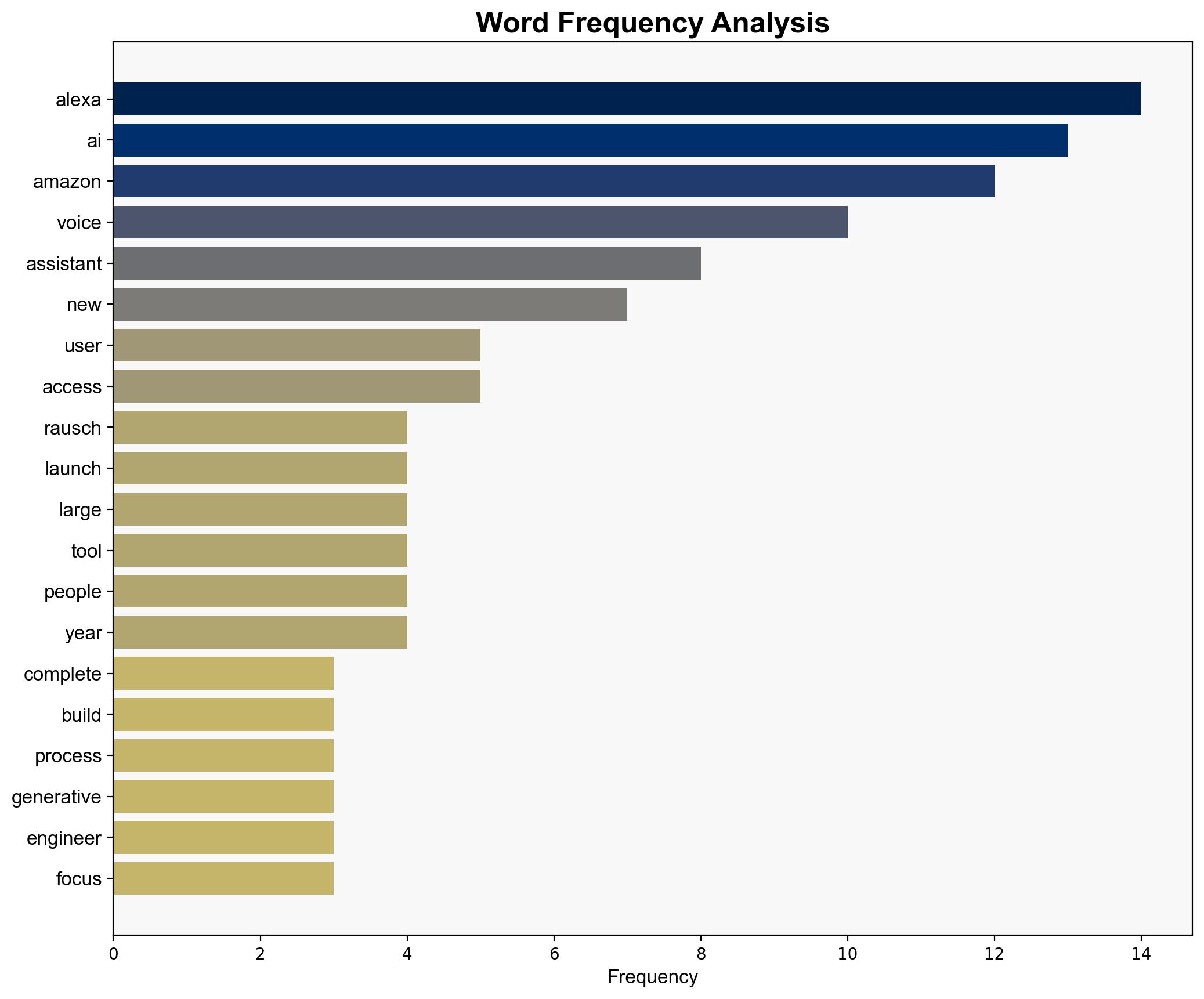
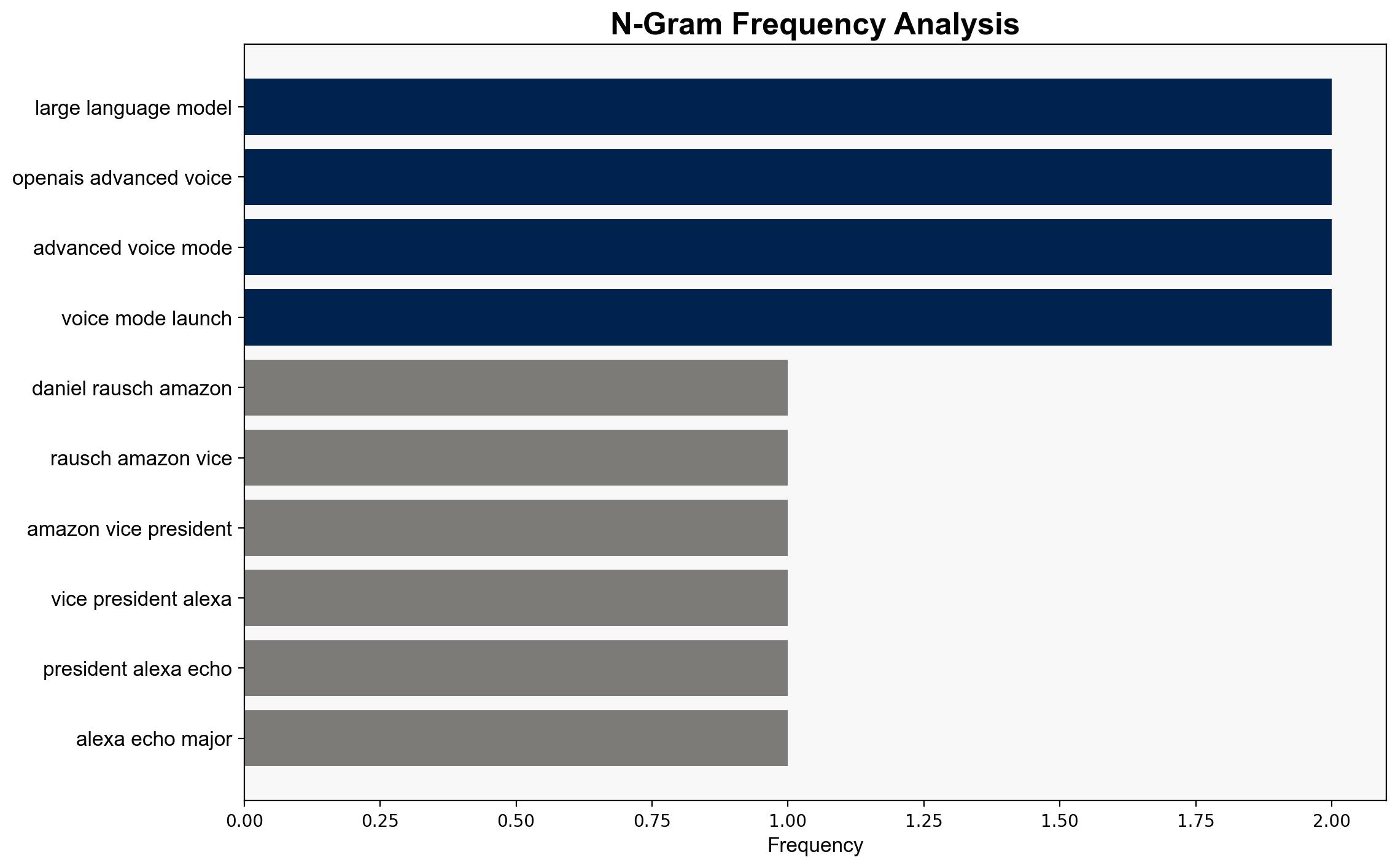
Amazon has undertaken a comprehensive overhaul of its Alexa voice assistant, leveraging a significant array of AI tools, particularly generative AI and large language models. This transformation aims to enhance user interaction through personalized experiences and improved functionality. The strategic implications for Amazon include potential workforce restructuring and increased competition in the AI-driven voice assistant market.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Amazon’s integration of advanced AI tools in Alexa could attract cyber adversaries aiming to exploit vulnerabilities in AI systems. Simulating potential attack vectors can help preemptively address these risks.
Indicators Development
Monitoring AI system performance and user interaction patterns can help detect anomalies that may indicate security threats or system malfunctions.
Bayesian Scenario Modeling
Utilizing probabilistic models to assess the likelihood of cyberattacks on Alexa’s new architecture can guide strategic security enhancements.
3. Implications and Strategic Risks
The deployment of AI-enhanced Alexa poses several strategic risks, including potential job displacement due to increased efficiency and the need for continuous cybersecurity vigilance. The competitive landscape is intensifying, with Apple and OpenAI also advancing their voice assistant technologies. This could lead to market share shifts and necessitate rapid innovation cycles.
4. Recommendations and Outlook
- Enhance cybersecurity measures to protect against potential AI system vulnerabilities.
- Develop workforce transition plans to address potential job displacement due to AI integration.
- Scenario-based projections:
- Best Case: Successful integration leads to increased market share and user satisfaction.
- Worst Case: Security breaches and workforce disruptions lead to reputational damage and market loss.
- Most Likely: Gradual market adaptation with moderate workforce adjustments and competitive pressures.
5. Key Individuals and Entities
Daniel Rausch, Andy Jassy
6. Thematic Tags
artificial intelligence, cybersecurity, workforce transformation, competitive strategy