A Russian Hacking Group Is Using Fake Versions of MetaMask to Steal 1M in Crypto – Decrypt
Published on: 2025-08-10
Intelligence Report: A Russian Hacking Group Is Using Fake Versions of MetaMask to Steal 1M in Crypto – Decrypt
1. BLUF (Bottom Line Up Front)
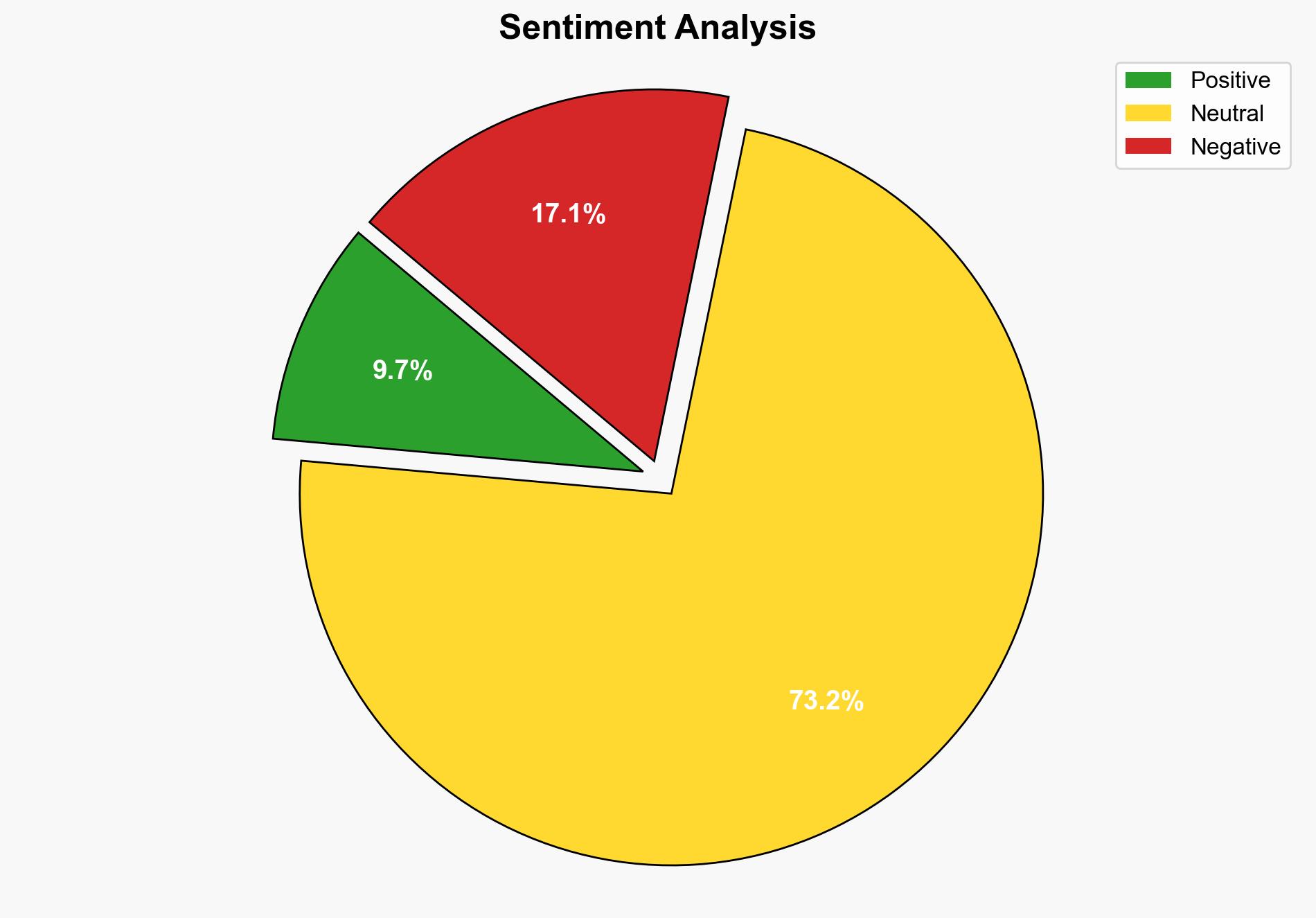
The Russian hacking group “GreedyBear” is executing a sophisticated cybercrime operation using fake crypto wallet extensions to steal significant cryptocurrency amounts. The most supported hypothesis is that GreedyBear operates as an independent criminal organization with potential state-tolerated activities. Confidence level: Moderate. Recommended action: Enhance cybersecurity measures for crypto wallet users and increase international cooperation to track and dismantle GreedyBear’s infrastructure.
2. Competing Hypotheses
1. **Hypothesis A**: GreedyBear is an independent criminal organization exploiting vulnerabilities in crypto wallet extensions for financial gain.
2. **Hypothesis B**: GreedyBear is a state-sponsored group using crypto theft as a means to fund operations or destabilize international financial systems.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the centralized control indicated by a single IP address, suggesting a profit-driven motive rather than state-level operational complexity.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the centralized IP address indicates a profit-driven motive. Another assumption is that the use of fake reviews and non-malicious initial uploads are purely for deception.
– **Red Flags**: The centralized IP could be a deliberate misdirection. The absence of direct evidence linking GreedyBear to state sponsorship is a significant gap.
– **Blind Spots**: Potential state involvement or tacit approval is not conclusively ruled out.
4. Implications and Strategic Risks
The operation suggests a growing trend of industrial-scale cyber theft targeting crypto assets, posing economic risks and undermining trust in digital financial systems. If state-sponsored, it could indicate a broader geopolitical strategy to destabilize financial markets. The operation’s success may inspire similar groups, increasing the frequency and scale of such attacks.
5. Recommendations and Outlook
- **Mitigation**: Strengthen security protocols for crypto wallet extensions and educate users on verifying software authenticity.
- **International Cooperation**: Foster collaboration among cybersecurity agencies to track and dismantle GreedyBear’s network.
- **Scenario Projections**:
– **Best Case**: Successful international crackdown on GreedyBear, leading to reduced cybercrime incidents.
– **Worst Case**: Escalation in attacks, with GreedyBear expanding operations and inspiring copycat groups.
– **Most Likely**: Continued operations by GreedyBear with periodic disruptions by law enforcement.
6. Key Individuals and Entities
– Idan Dardikman (CTO, Koi Security)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus