Address Poisoning: A Tactic Exploiting User Behavior Instead of Private Key Theft
Published on: 2026-02-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Why address poisoning works without stealing private keys
1. BLUF (Bottom Line Up Front)
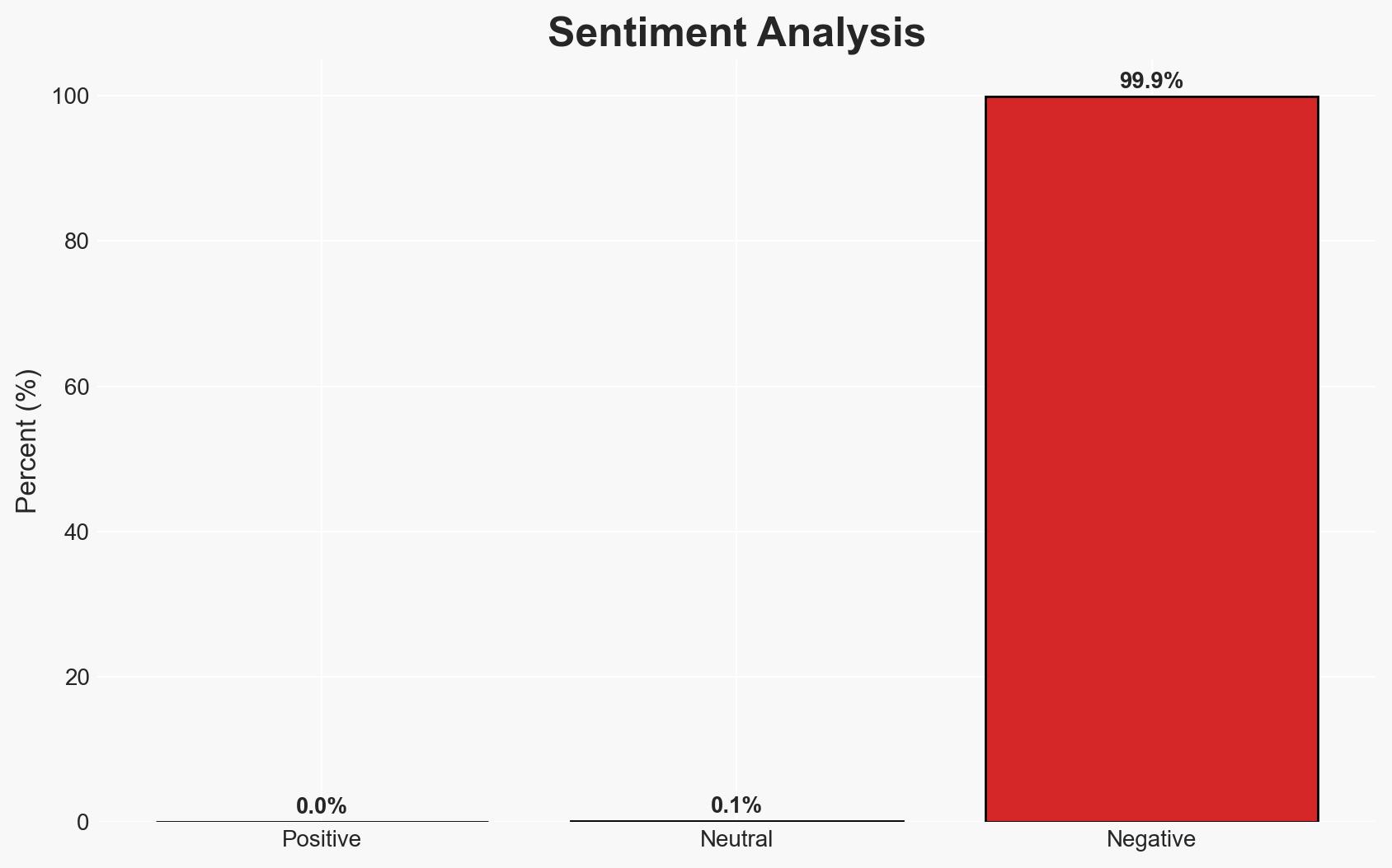
Address poisoning is an effective scam technique that exploits user behavior and interface design flaws, leading to significant financial losses without compromising private keys. The tactic is particularly effective on transparent blockchains and is expected to increase with the rise of Ethereum layer-2 networks. This assessment is made with moderate confidence.
2. Competing Hypotheses
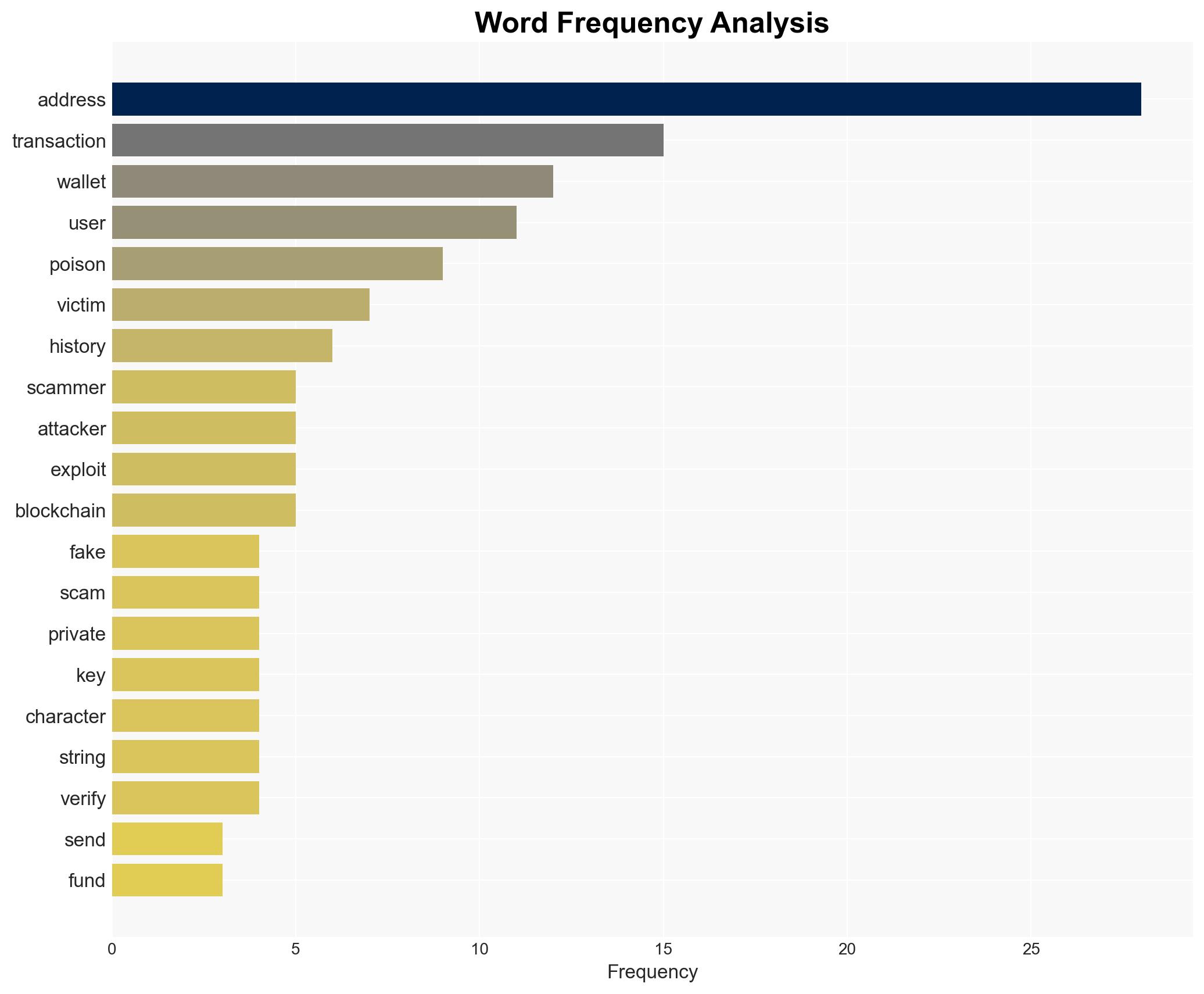
- Hypothesis A: Address poisoning is primarily successful due to human error and poor interface design, which scammers exploit by creating visually similar addresses. Supporting evidence includes the reliance on users’ habitual copying of addresses and the lack of full address verification. Key uncertainties involve the extent to which interface improvements could mitigate this risk.
- Hypothesis B: The success of address poisoning is mainly due to systemic vulnerabilities in blockchain technology itself, such as the transparency of transaction histories. This hypothesis is less supported as the scam does not exploit blockchain protocols but rather user interaction with them.
- Assessment: Hypothesis A is currently better supported, as the scam exploits human factors rather than technical vulnerabilities. Indicators such as increased user education or interface redesign could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Users will continue to rely on visual address verification; blockchain transaction transparency remains unchanged; scammers have access to vanity address generators.
- Information Gaps: Detailed data on the frequency and distribution of address poisoning incidents; effectiveness of current user education efforts.
- Bias & Deception Risks: Potential bias in assuming all users are equally susceptible to scams; risk of deception in self-reported losses by victims.
4. Implications and Strategic Risks
The persistence of address poisoning scams could undermine trust in blockchain technologies and lead to regulatory scrutiny. Over time, this may influence user behavior and the development of more secure interfaces.
- Political / Geopolitical: Potential for increased regulatory intervention in the cryptocurrency sector.
- Security / Counter-Terrorism: Minimal direct impact, but could be exploited for funding illicit activities.
- Cyber / Information Space: Increased focus on cybersecurity measures within blockchain applications.
- Economic / Social: Potential loss of confidence in cryptocurrencies, affecting market stability and adoption rates.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Encourage wallet providers to implement stronger address verification features; launch awareness campaigns targeting common user errors.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms to enhance blockchain security; invest in user education and interface improvements.
- Scenario Outlook:
- Best: Adoption of enhanced security measures reduces scam incidents.
- Worst: Continued scams lead to significant financial losses and regulatory crackdowns.
- Most-Likely: Gradual improvements in user behavior and interface design reduce the effectiveness of address poisoning.
6. Key Individuals and Entities
- Changpeng “CZ” Zhao – Binance co-founder
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cryptocurrency, blockchain security, cybercrime, user behavior, financial scams, regulatory impact, interface design
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us