Advancements in counter-drone technology face challenges as incidents raise safety concerns for airspace mana…
Published on: 2026-02-13
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Counter-drone technologies are evolving but there’s no surefire way to defend against drone attacks
1. BLUF (Bottom Line Up Front)
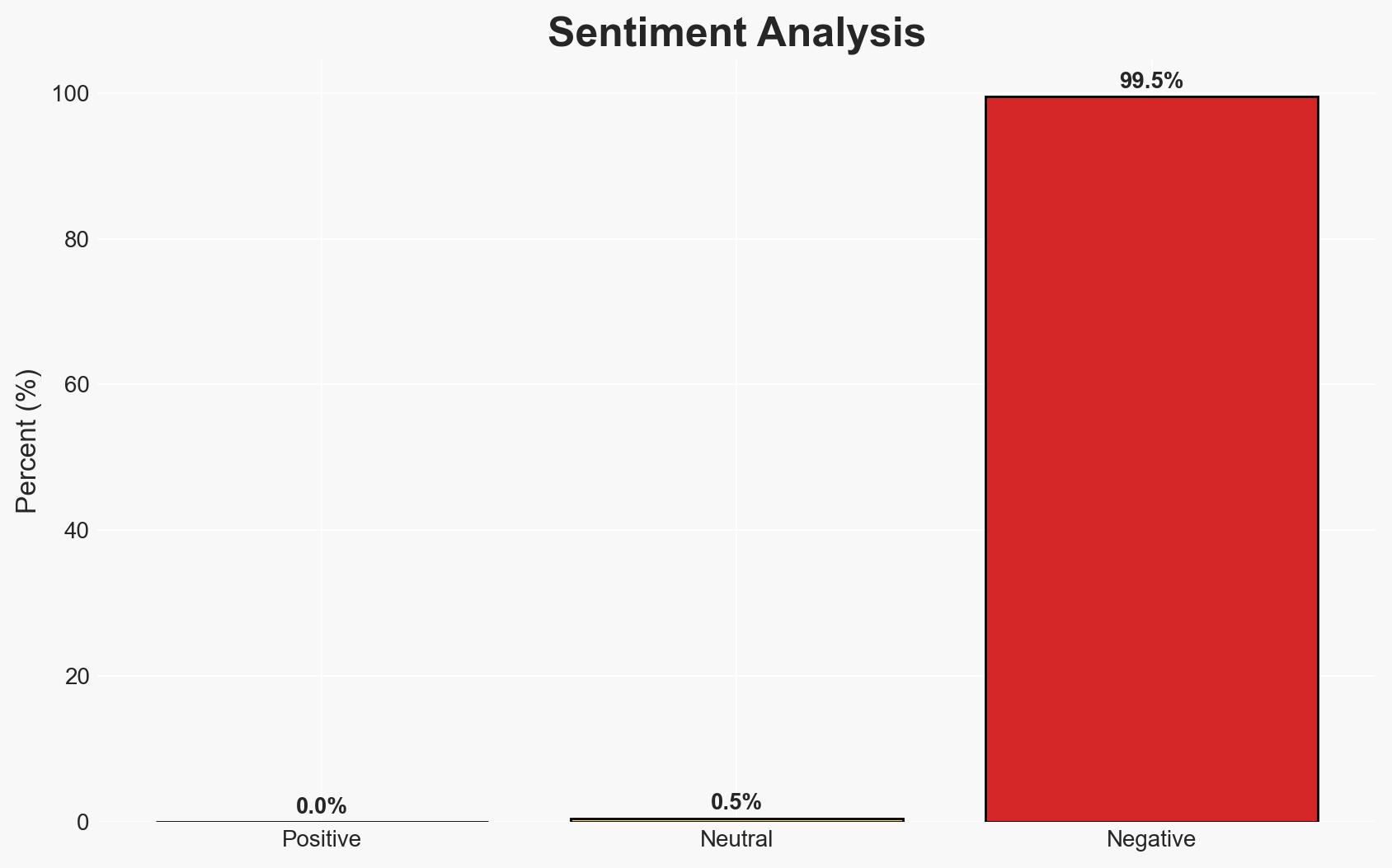
The current state of counter-drone technologies is insufficient to guarantee protection against drone threats, particularly in civilian infrastructure contexts. The incident at El Paso airport underscores vulnerabilities in using advanced counter-drone measures near populated areas. The most likely hypothesis is that the integration of counter-drone systems will continue to face significant operational challenges. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
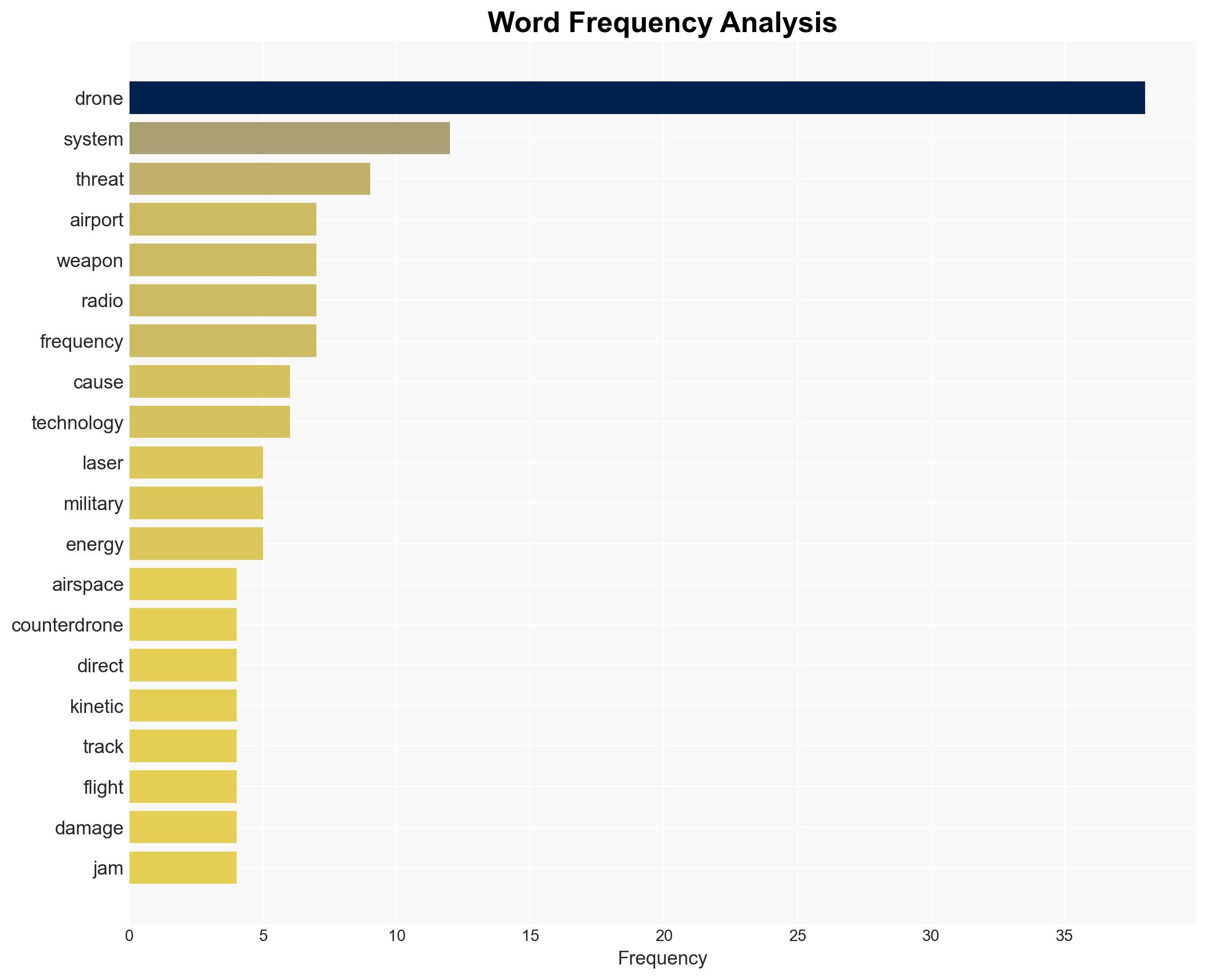
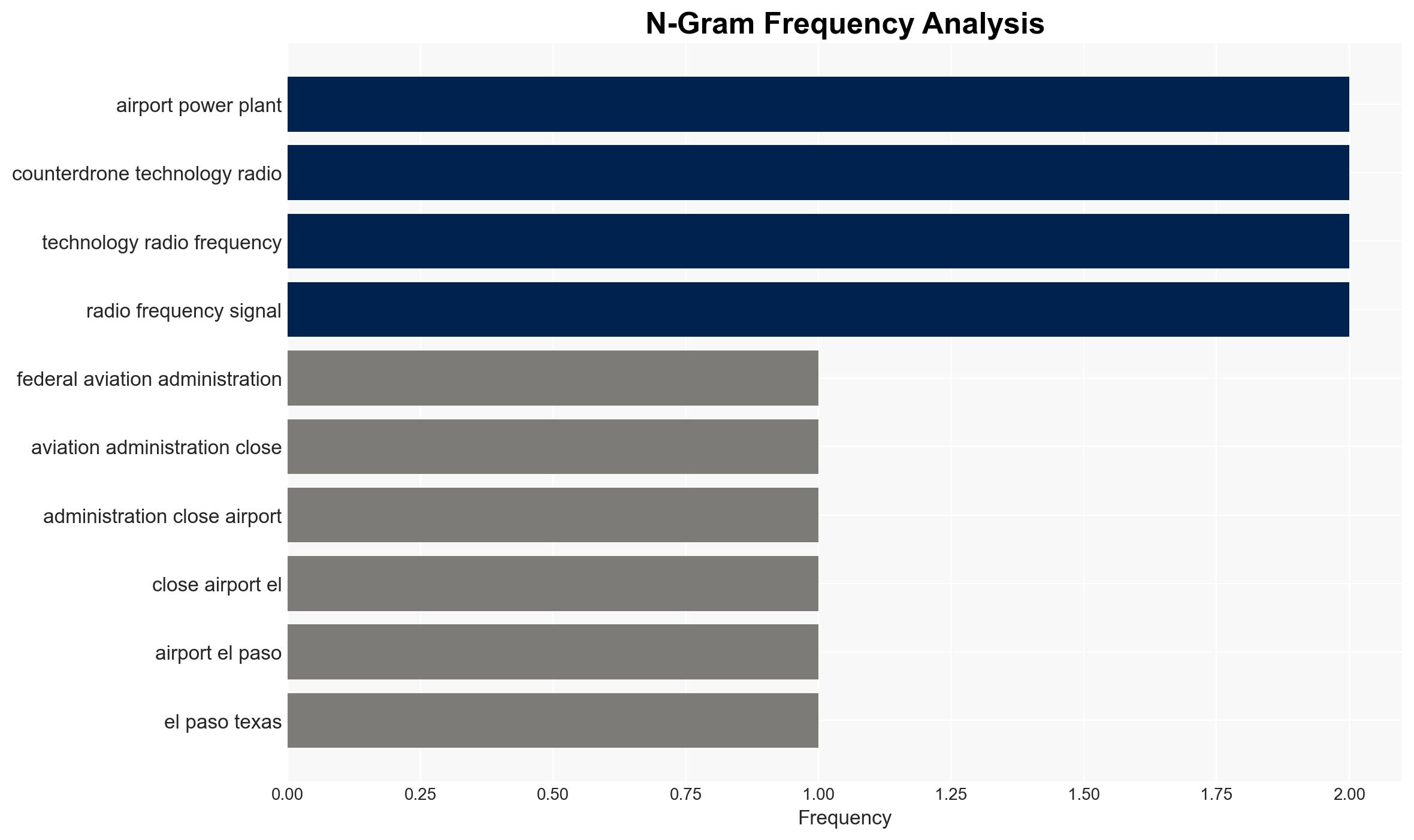
- Hypothesis A: The use of advanced counter-drone technologies, such as directed energy weapons, is effective in mitigating drone threats but poses risks to civilian airspace safety. This is supported by the El Paso incident where a laser weapon was used, but contradicted by the unintended consequence of airspace closure.
- Hypothesis B: Current counter-drone technologies are inadequate for effectively managing drone threats without causing collateral disruptions. This is supported by the El Paso incident and historical precedents like the Gatwick airport shutdown.
- Assessment: Hypothesis B is currently better supported due to the operational disruptions observed when counter-drone technologies are deployed in civilian contexts. Key indicators that could shift this judgment include successful integration of these technologies without collateral effects.
3. Key Assumptions and Red Flags
- Assumptions: Counter-drone technologies will continue to evolve; civilian infrastructure remains a primary target for drone threats; regulatory frameworks will adapt to new technologies.
- Information Gaps: Detailed technical specifications and operational protocols of deployed counter-drone systems; comprehensive threat assessments of drone capabilities at the U.S.-Mexico border.
- Bias & Deception Risks: Potential over-reliance on military-grade solutions for civilian problems; underestimation of non-state actors’ capabilities to adapt drone technologies.
4. Implications and Strategic Risks
The evolution of counter-drone technologies will likely lead to increased regulatory scrutiny and operational challenges, particularly in civilian airspace. The potential for misidentification and collateral disruptions remains high.
- Political / Geopolitical: Increased tensions with neighboring countries over cross-border drone incidents; potential for international regulatory collaboration or conflict.
- Security / Counter-Terrorism: Enhanced threat from non-state actors using drones for asymmetrical warfare; increased demand for counter-drone capabilities in critical infrastructure protection.
- Cyber / Information Space: Potential for cyber vulnerabilities in counter-drone systems; misinformation campaigns exploiting drone incidents.
- Economic / Social: Economic impacts from airspace closures; public concern over safety and privacy implications of counter-drone measures.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive review of counter-drone protocols; enhance coordination between FAA and security agencies.
- Medium-Term Posture (1–12 months): Develop integrated counter-drone strategies for critical infrastructure; invest in research and development of non-disruptive counter-drone technologies.
- Scenario Outlook:
- Best: Successful integration of counter-drone systems with minimal disruptions.
- Worst: Increased frequency of airspace closures due to counter-drone operations.
- Most-Likely: Gradual improvement in counter-drone effectiveness with ongoing operational challenges.
6. Key Individuals and Entities
- Federal Aviation Administration (FAA)
- Customs and Border Protection (CBP)
- Department of Defense (DoD)
- Counter-UAS Center of Excellence, Oklahoma State University
- ISIS terrorist group
7. Thematic Tags
Counter-Terrorism, counter-drone technologies, airspace security, critical infrastructure, non-state actors, regulatory challenges, military technology
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us