Afghan data leak how selective state secrecy and cover-ups can harm civilians – The Conversation Africa
Published on: 2025-07-18
Intelligence Report: Afghan Data Leak – Impact of State Secrecy and Cover-Ups on Civilians
1. BLUF (Bottom Line Up Front)
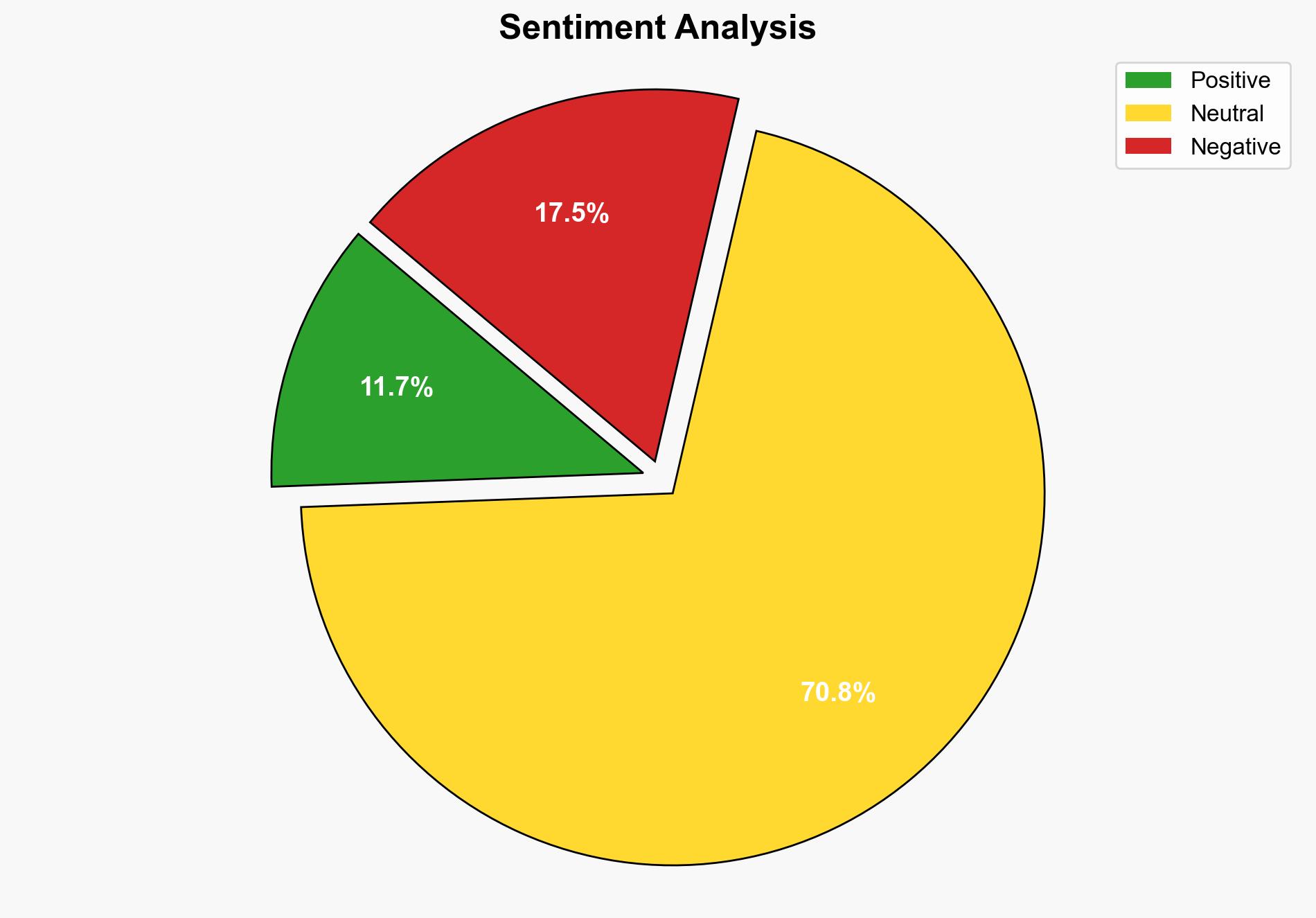
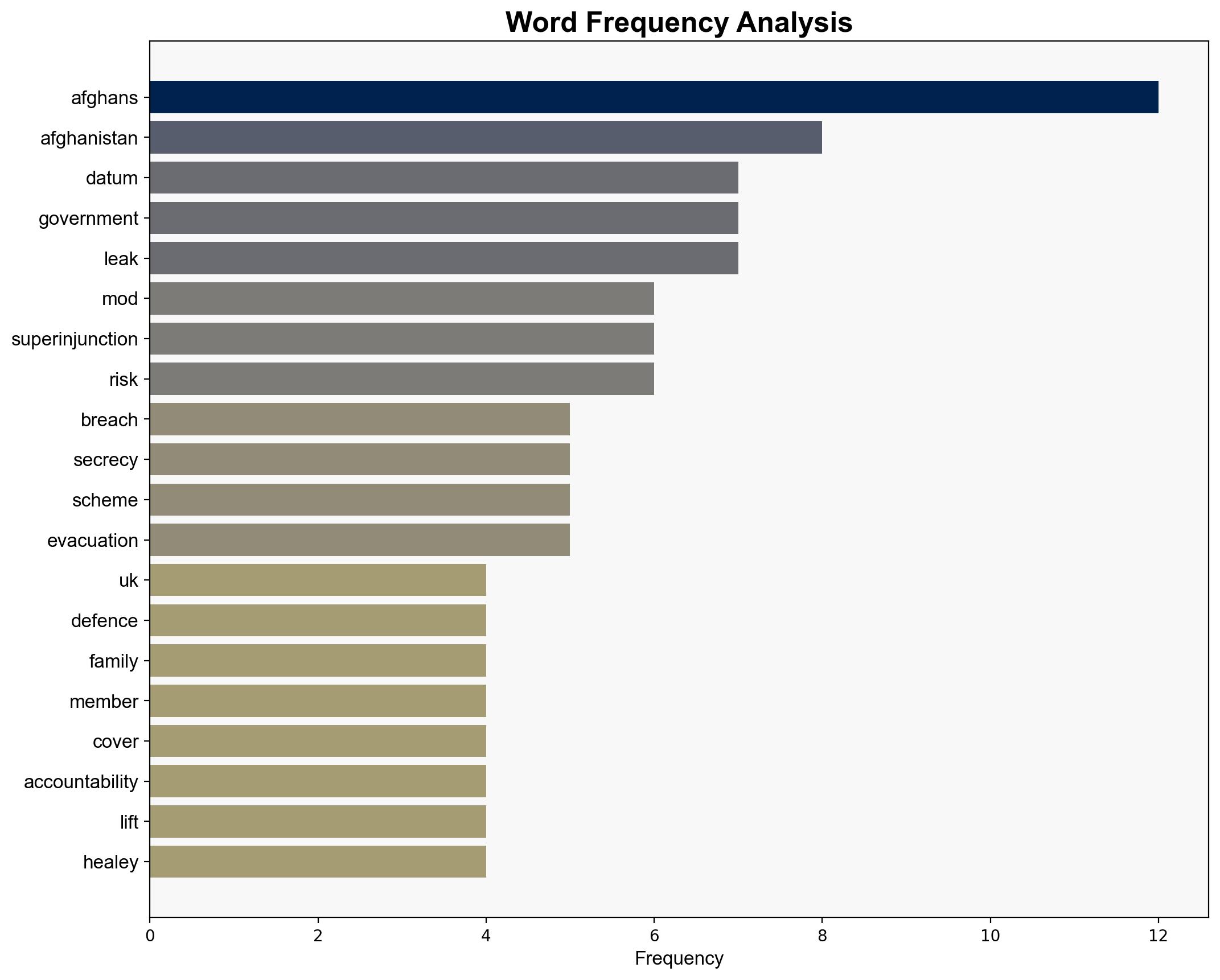
The Afghan data leak, involving the inadvertent exposure of personal information of Afghan associates and their families by the UK Ministry of Defence, underscores significant risks associated with state secrecy and accountability failures. The incident, followed by attempts to cover up the breach, highlights vulnerabilities in data handling and the potential harm to civilians, especially those at risk from the Taliban. Strategic recommendations include enhancing transparency, improving data security protocols, and ensuring accountability to prevent future occurrences.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulated potential actions by cyber adversaries exploiting the data breach to anticipate vulnerabilities and improve resilience strategies.
Indicators Development
Developed indicators to detect and monitor anomalies in data handling and communication processes for early threat detection.
Bayesian Scenario Modeling
Utilized probabilistic inference to quantify uncertainties and predict potential pathways for further data breaches or misuse.
Network Influence Mapping
Mapped influence relationships to assess the impact of involved actors and the potential spread of leaked information.
3. Implications and Strategic Risks
The data leak presents significant risks, including potential targeting of exposed individuals by hostile entities, undermining of public trust in government transparency, and challenges in international relations. The incident reveals systemic vulnerabilities in data management and accountability mechanisms, with potential cascading effects on national security and diplomatic efforts.
4. Recommendations and Outlook
- Enhance data security protocols and training to prevent future breaches.
- Increase transparency and accountability in government operations to rebuild trust.
- Implement scenario-based planning to prepare for best case, worst case, and most likely outcomes of similar incidents.
5. Key Individuals and Entities
John Healey, Sara de Jong, Tom Tugendhat
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus