Agents are advancing fast Security Needs to Keep Pace – TechRadar
Published on: 2025-07-18
Intelligence Report: Agents are advancing fast Security Needs to Keep Pace – TechRadar
1. BLUF (Bottom Line Up Front)
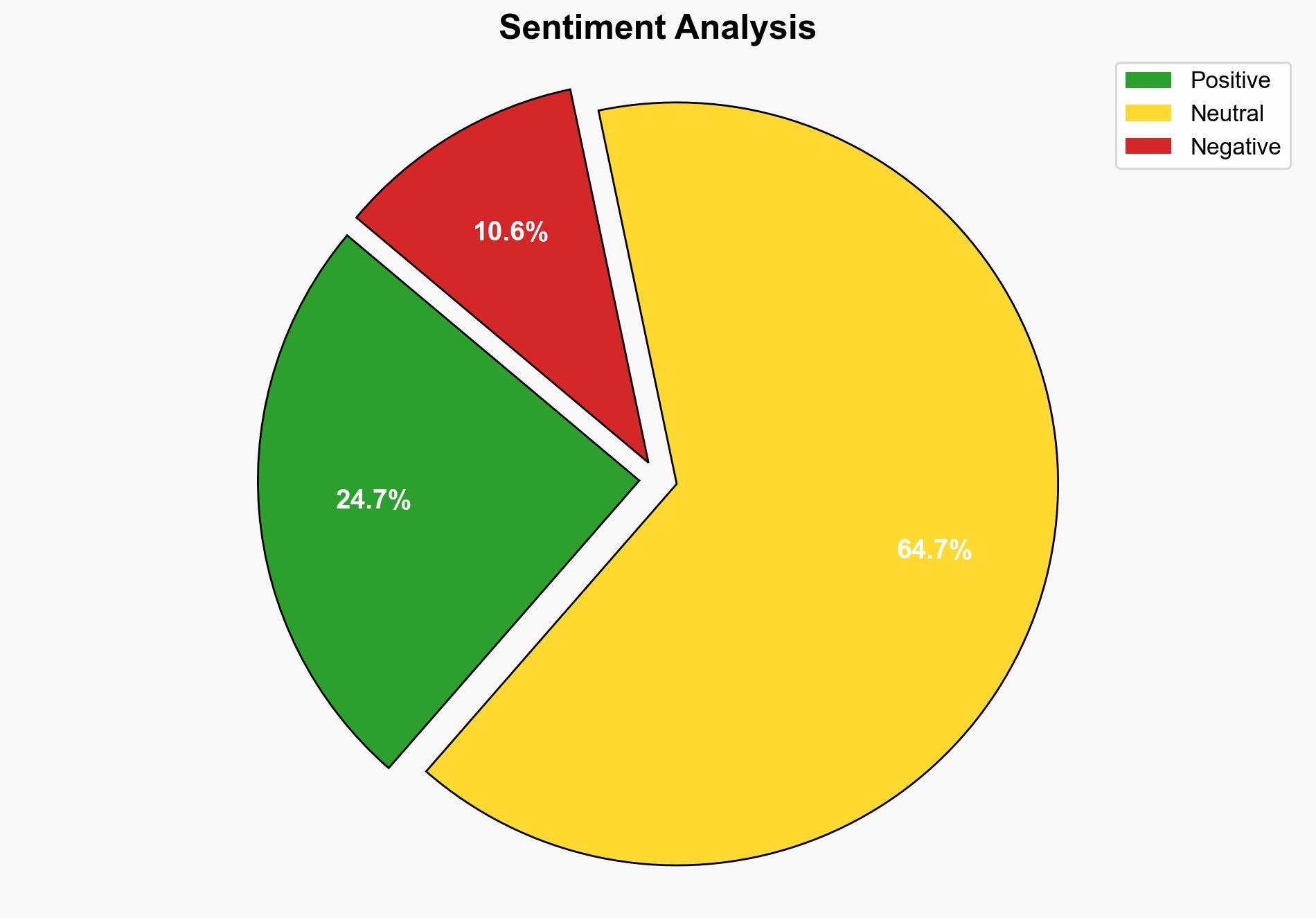
The rapid integration of autonomous agents in enterprise environments presents both significant productivity gains and substantial security risks. As these agents become more embedded in business operations, they introduce vulnerabilities that could lead to ethical and operational failures if not properly managed. Immediate action is required to ensure security measures evolve in tandem with technological advancements to prevent potential data breaches and operational disruptions.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations indicate that autonomous agents, if compromised, could be manipulated to perform unauthorized actions, potentially leading to significant data breaches or operational disruptions.
Indicators Development
Monitoring systems for anomalies in agent behavior is crucial for early detection of potential threats, particularly those arising from poor training data or unauthorized access.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of increased cyberattack attempts on systems utilizing autonomous agents, necessitating robust security protocols and continuous monitoring.
3. Implications and Strategic Risks
The integration of autonomous agents without adequate security measures poses systemic vulnerabilities across multiple domains. These include potential data breaches, unauthorized decision-making, and ethical concerns. The cascading effects could impact national security, economic stability, and organizational integrity.
4. Recommendations and Outlook
- Implement comprehensive security frameworks that include data discovery, classification, encryption, and identity management to protect against unauthorized access and data breaches.
- Develop and enforce policies for regular credential rotation and auditing to prevent misuse and ensure accountability.
- Scenario-based projections suggest that in the best case, proactive security measures will mitigate risks, while the worst case involves significant operational disruptions due to security lapses.
5. Key Individuals and Entities
Notable mention: DJ Vu, involved in security software development at IBM Cloud.
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus