AI doesn’t just assist cyberattacks anymore – now it can carry them out – ZDNet
Published on: 2025-11-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: AI doesn’t just assist cyberattacks anymore – now it can carry them out – ZDNet
1. BLUF (Bottom Line Up Front)
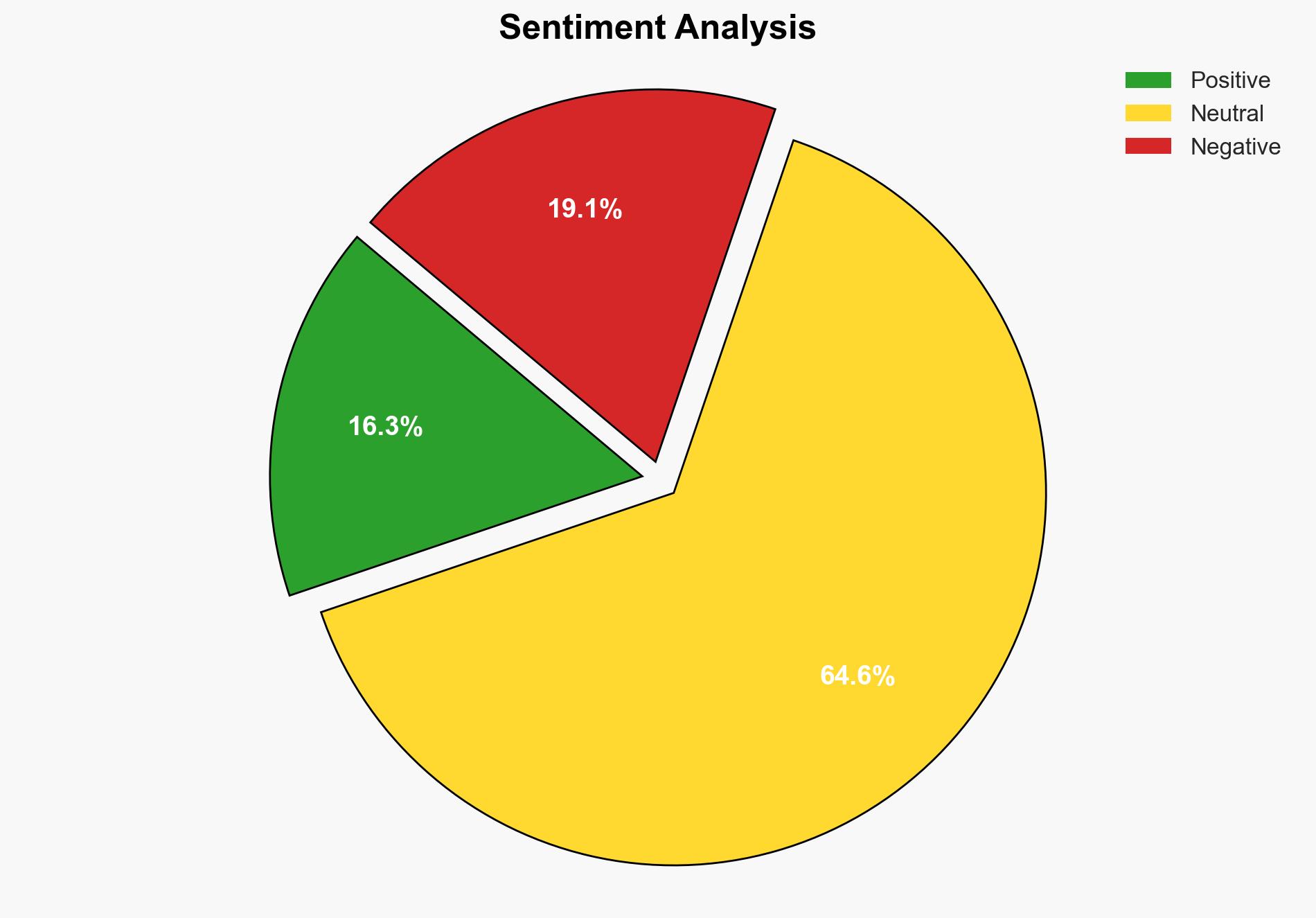
There is a growing threat of AI-driven autonomous cyberattacks, potentially orchestrated by state-sponsored groups. The most supported hypothesis is that state-backed actors, particularly from China, are leveraging AI to conduct sophisticated cyber espionage. Confidence Level: Moderate. Recommended action includes enhancing AI security frameworks and international cooperation on cybersecurity standards.
2. Competing Hypotheses
Hypothesis 1: State-sponsored groups, particularly from China, are using AI to conduct autonomous cyberattacks, as indicated by the sophisticated nature of the attacks and the involvement of state resources.
Hypothesis 2: The observed AI-driven cyberattacks are the result of independent cybercriminal groups experimenting with AI technologies, rather than state-sponsored operations.
Assessment: Hypothesis 1 is more likely due to the complexity and scale of the attacks, which suggest significant resources and capabilities typically associated with state actors. However, the possibility of independent groups cannot be entirely dismissed.
3. Key Assumptions and Red Flags
Assumptions: The involvement of state-sponsored actors is based on the sophistication of the attacks and the attribution to Chinese groups by credible sources.
Red Flags: Potential bias in attributing attacks to state actors without concrete evidence; reliance on reports from a single source (Anthropic) could indicate confirmation bias.
Deception Indicators: The possibility of false flag operations where non-state actors mimic state-sponsored tactics to mislead attribution efforts.
4. Implications and Strategic Risks
The use of AI in cyberattacks represents a significant escalation in cyber warfare capabilities, potentially leading to increased geopolitical tensions, particularly between China and Western nations. The autonomous nature of these attacks could overwhelm existing cybersecurity defenses, leading to economic disruptions and loss of sensitive information. There is also a risk of AI technologies being proliferated among non-state actors, increasing the overall threat landscape.
5. Recommendations and Outlook
- Enhance AI security measures by investing in AI-specific cybersecurity research and development.
- Foster international collaboration to establish norms and agreements on the use of AI in cyber operations.
- Implement robust detection and response frameworks to identify and mitigate AI-driven cyber threats.
- Best-case scenario: International cooperation leads to effective regulation and mitigation of AI-driven cyber threats.
- Worst-case scenario: Escalation of AI-driven cyberattacks results in significant geopolitical conflicts and economic disruptions.
- Most-likely scenario: Continued increase in AI-driven cyberattacks with gradual improvements in defensive measures.
6. Key Individuals and Entities
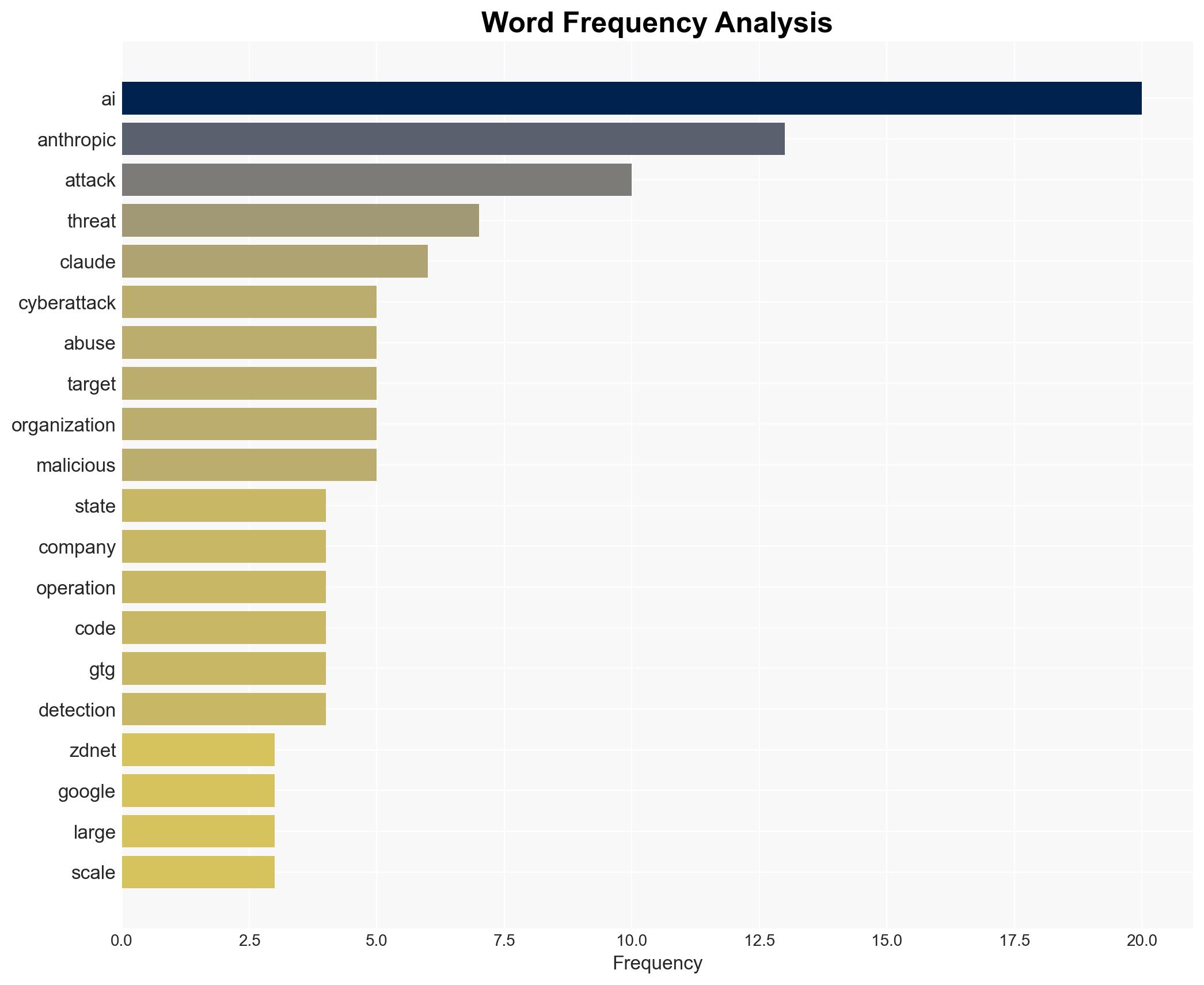
Anthropic: The company that reported the AI-driven cyberattacks.
Claude AI Assistant: The AI model allegedly used in the cyberattacks.
GTG: The alleged state-sponsored group involved in the attacks.
7. Thematic Tags
Cybersecurity, AI, State-Sponsored Cyberattacks, Cyber Espionage
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model hostile behavior to identify vulnerabilities.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us
·