AIPentestKit AI-Augmented Red Team Toolkit for Recon Fuzzing and Payload Generation – Darknet.org.uk
Published on: 2025-09-29
Intelligence Report: AIPentestKit AI-Augmented Red Team Toolkit for Recon Fuzzing and Payload Generation – Darknet.org.uk
1. BLUF (Bottom Line Up Front)
The AIPentestKit appears to be a sophisticated, AI-augmented toolkit designed to enhance red team operations through automation and advanced payload generation. The most supported hypothesis suggests that this toolkit primarily aims to streamline and enhance the efficiency of penetration testing tasks. Confidence level: Moderate. Recommended action: Monitor the development and distribution of this toolkit to assess its potential impact on cybersecurity defenses.
2. Competing Hypotheses
Hypothesis 1: AIPentestKit is primarily intended to enhance legitimate cybersecurity testing by automating repetitive tasks and improving payload generation through AI, thereby increasing efficiency and accuracy in identifying vulnerabilities.
Hypothesis 2: AIPentestKit could be exploited by malicious actors to facilitate unauthorized access and attacks, given its capabilities in payload generation and webshell evasion techniques.
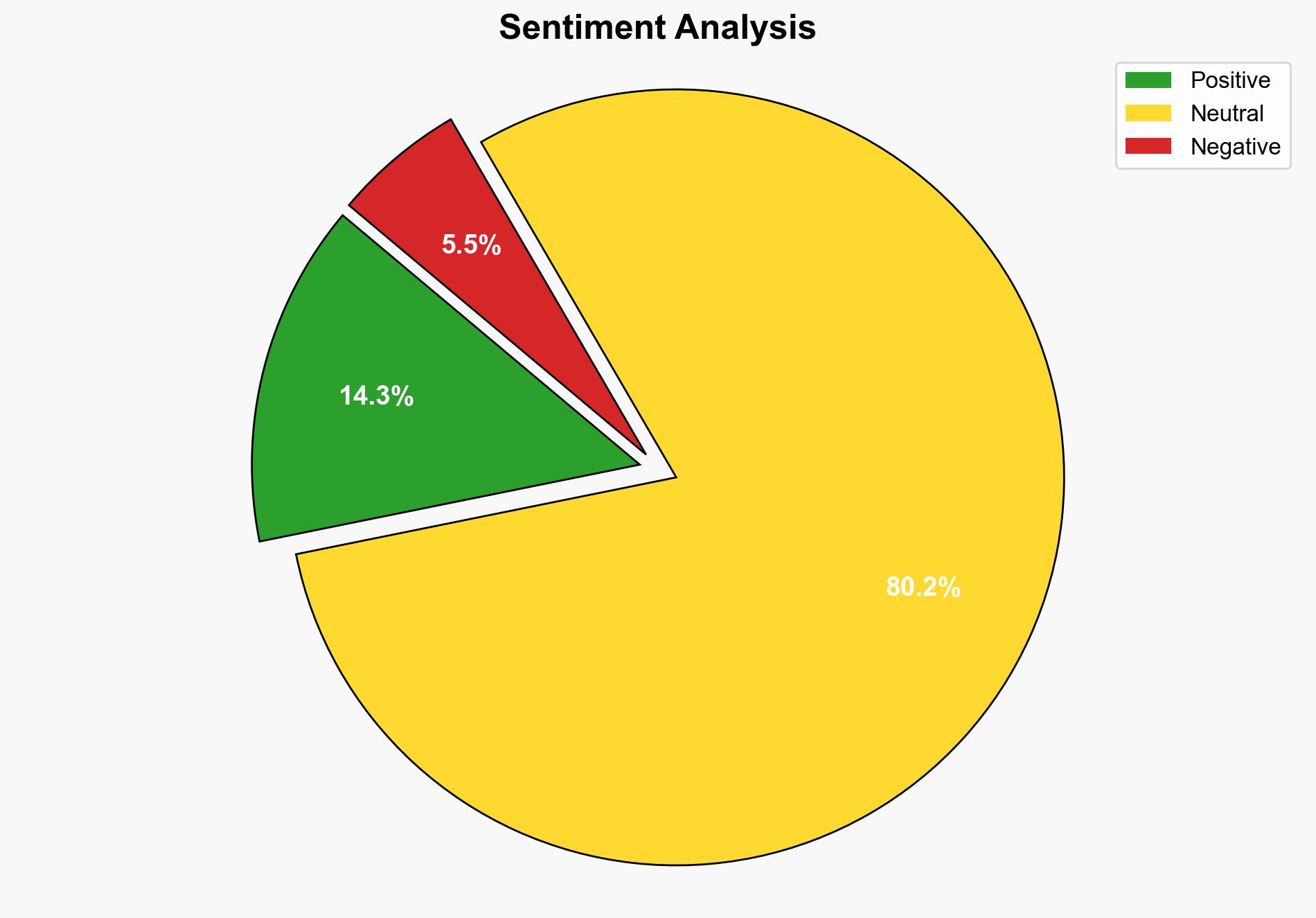
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis 1 is better supported due to the toolkit’s emphasis on documentation, integration with legitimate tools like Burp Suite, and its open-source nature, which suggests a focus on transparency and community-driven improvement.
3. Key Assumptions and Red Flags
Assumptions include the belief that the toolkit will primarily be used by ethical hackers and security professionals. A red flag is the potential for dual-use, where the same capabilities could be leveraged for malicious purposes. The lack of explicit security measures to prevent misuse is a notable blind spot.
4. Implications and Strategic Risks
The toolkit’s capabilities could lead to a shift in the cybersecurity landscape by lowering the barrier to entry for conducting sophisticated penetration tests. This could result in both improved security postures for organizations and increased risks if exploited by threat actors. The potential for cascading threats exists if the toolkit is widely adopted by malicious entities, leading to more frequent and sophisticated cyber attacks.
5. Recommendations and Outlook
- Monitor forums and platforms for discussions or mentions of AIPentestKit to assess its adoption and potential misuse.
- Encourage the development of security features within the toolkit to prevent unauthorized use.
- Scenario-based projections:
- Best Case: The toolkit is predominantly used by ethical hackers, leading to enhanced cybersecurity defenses.
- Worst Case: Malicious actors exploit the toolkit, leading to a surge in sophisticated cyber attacks.
- Most Likely: A mixed usage scenario where both ethical and malicious actors utilize the toolkit, necessitating enhanced monitoring and response strategies.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. The focus is on the toolkit and its integration with existing cybersecurity tools.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus