Akira ransomware affiliates continue breaching organizations via SonicWall firewalls – Help Net Security
Published on: 2025-09-11
Intelligence Report: Akira ransomware affiliates continue breaching organizations via SonicWall firewalls – Help Net Security
1. BLUF (Bottom Line Up Front)
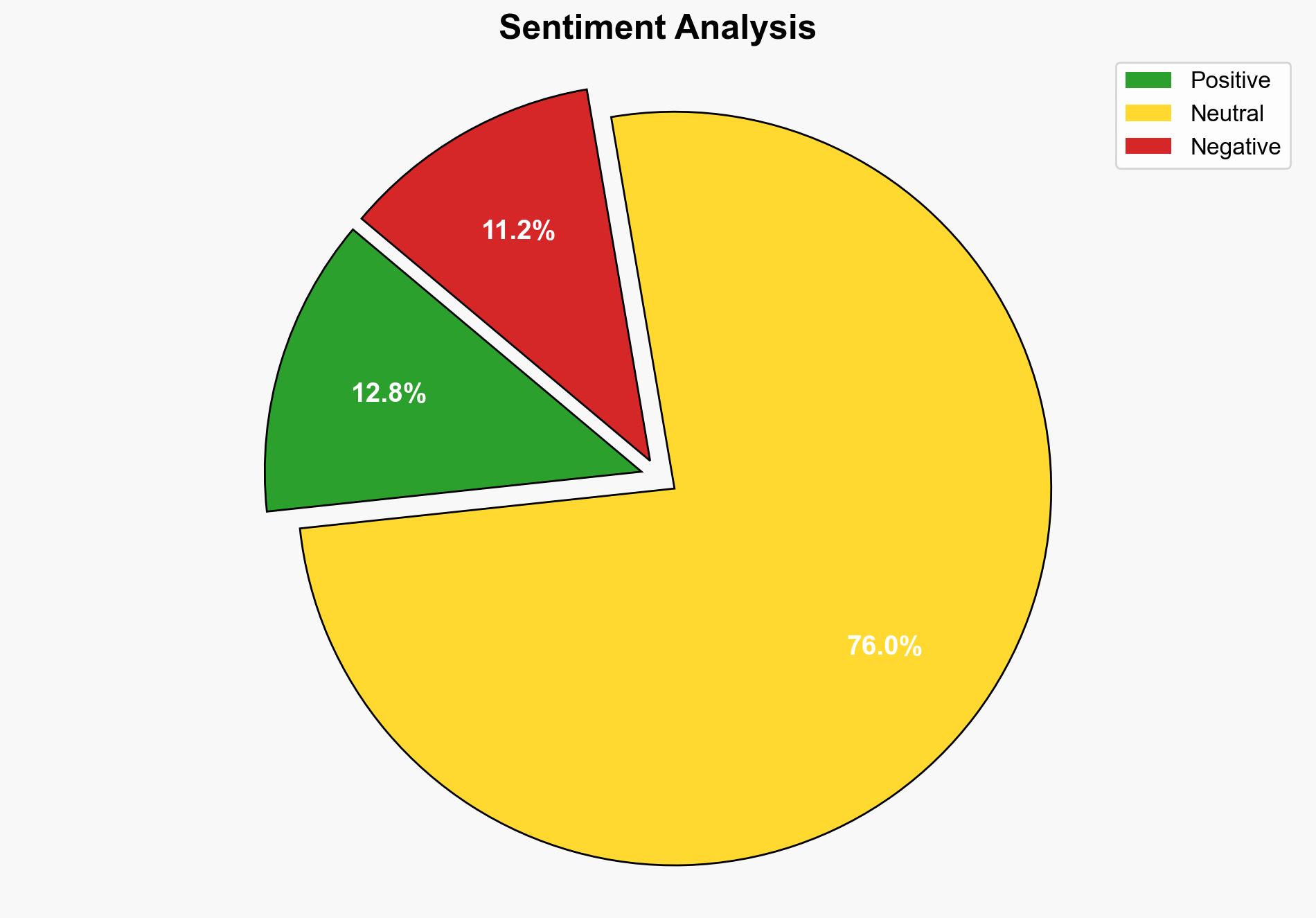
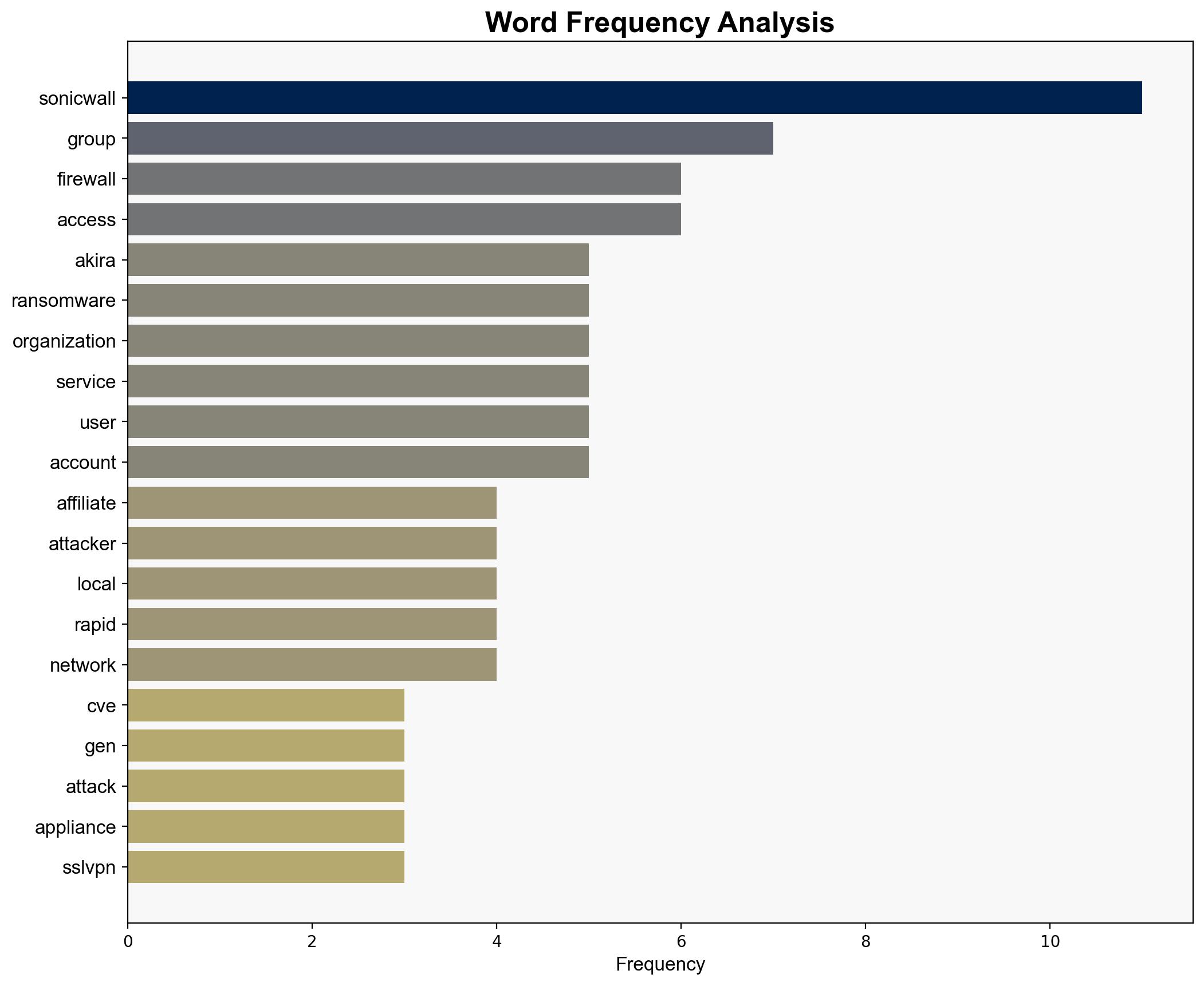
The Akira ransomware group continues exploiting vulnerabilities in SonicWall firewalls, leveraging both unpatched systems and misconfigurations. The most supported hypothesis is that these breaches are primarily due to organizations failing to implement timely patches and secure configurations. Confidence level: Moderate. Recommended action: Immediate patching of SonicWall systems, enhanced monitoring, and configuration audits.
2. Competing Hypotheses
Hypothesis 1: The primary cause of breaches is the exploitation of unpatched vulnerabilities in SonicWall firewalls by Akira affiliates.
Hypothesis 2: Misconfigurations within SonicWall firewalls, such as default user group settings, are the main enablers for Akira ransomware attacks.
Using ACH 2.0, Hypothesis 1 is better supported as the report highlights a critical flaw (CVE) that remains unpatched in many systems, providing a direct attack vector. Hypothesis 2 is plausible but secondary, as it requires additional conditions (e.g., misconfiguration) to be exploited.
3. Key Assumptions and Red Flags
Assumptions include the belief that organizations are aware of and have access to the necessary patches and configuration guidelines. A red flag is the lack of specific data on the proportion of breaches attributed to each cause (unpatched vs. misconfigured systems). There is a potential cognitive bias towards assuming technical flaws are the primary issue without considering organizational policy failures.
4. Implications and Strategic Risks
The continued exploitation of SonicWall vulnerabilities poses significant risks, including data breaches, financial losses, and reputational damage. If unaddressed, this could lead to increased ransomware activity across other sectors, potentially escalating to critical infrastructure. Economically, this could increase costs for cybersecurity insurance and incident response.
5. Recommendations and Outlook
- Immediate action: Patch all SonicWall systems to the latest version and review configurations to ensure security best practices.
- Medium-term: Implement robust monitoring and incident response capabilities to detect and mitigate breaches quickly.
- Long-term: Develop a comprehensive cybersecurity training program for IT staff to prevent misconfigurations.
- Scenario-based projections:
- Best case: Rapid patching and configuration updates significantly reduce breach incidents.
- Worst case: Continued negligence leads to widespread ransomware attacks, affecting critical sectors.
- Most likely: A gradual decrease in breaches as organizations slowly implement recommended security measures.
6. Key Individuals and Entities
No specific individuals are mentioned. Entities involved include Akira ransomware affiliates and SonicWall.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus