Amazon uncovers North Korean infiltration through keystroke lag in US-based IT hire’s remote work setup
Published on: 2025-12-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Keystroke lag alerts Amazon security staff that recent US-based IT hire was actually in North Korea
1. BLUF (Bottom Line Up Front)
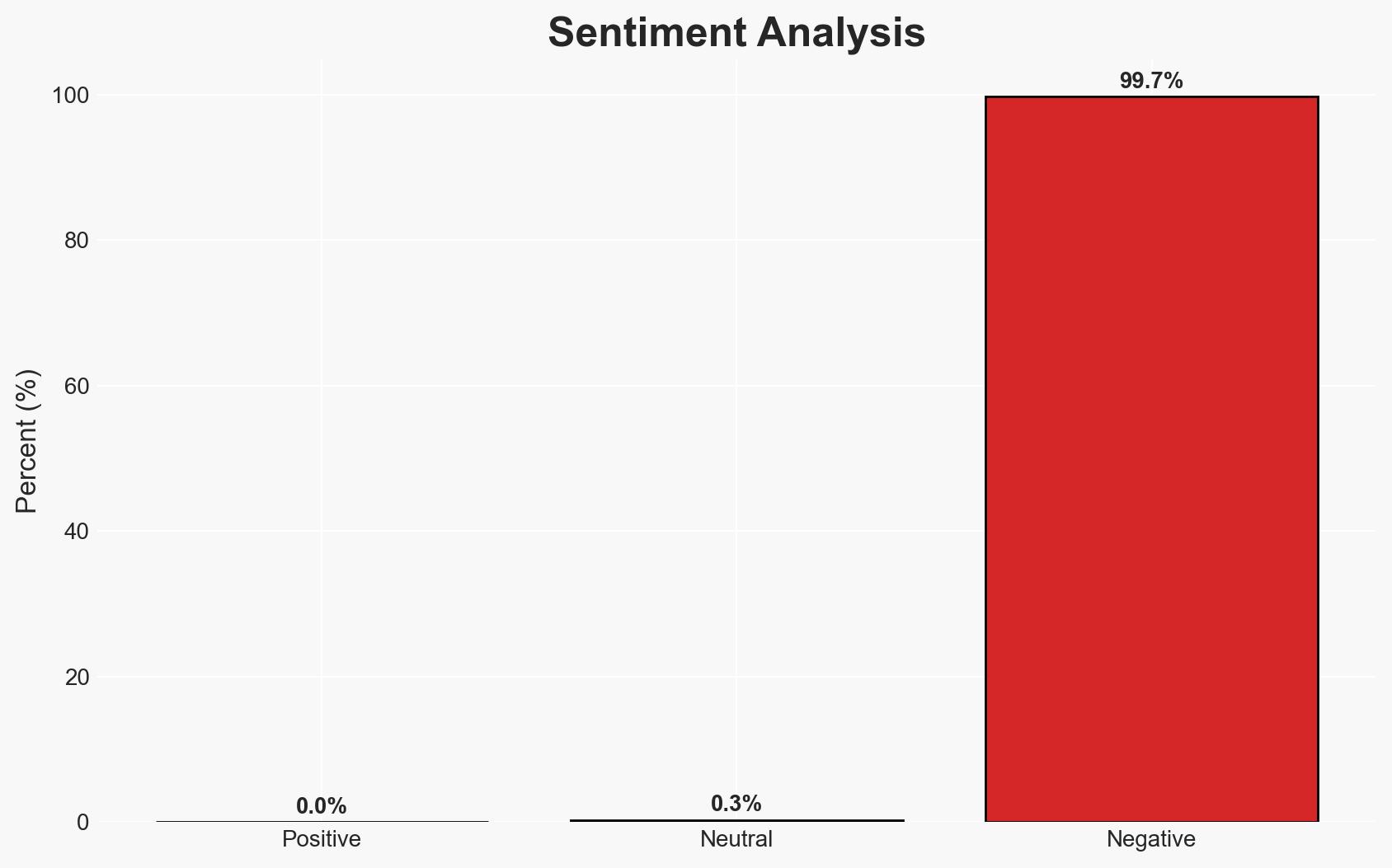
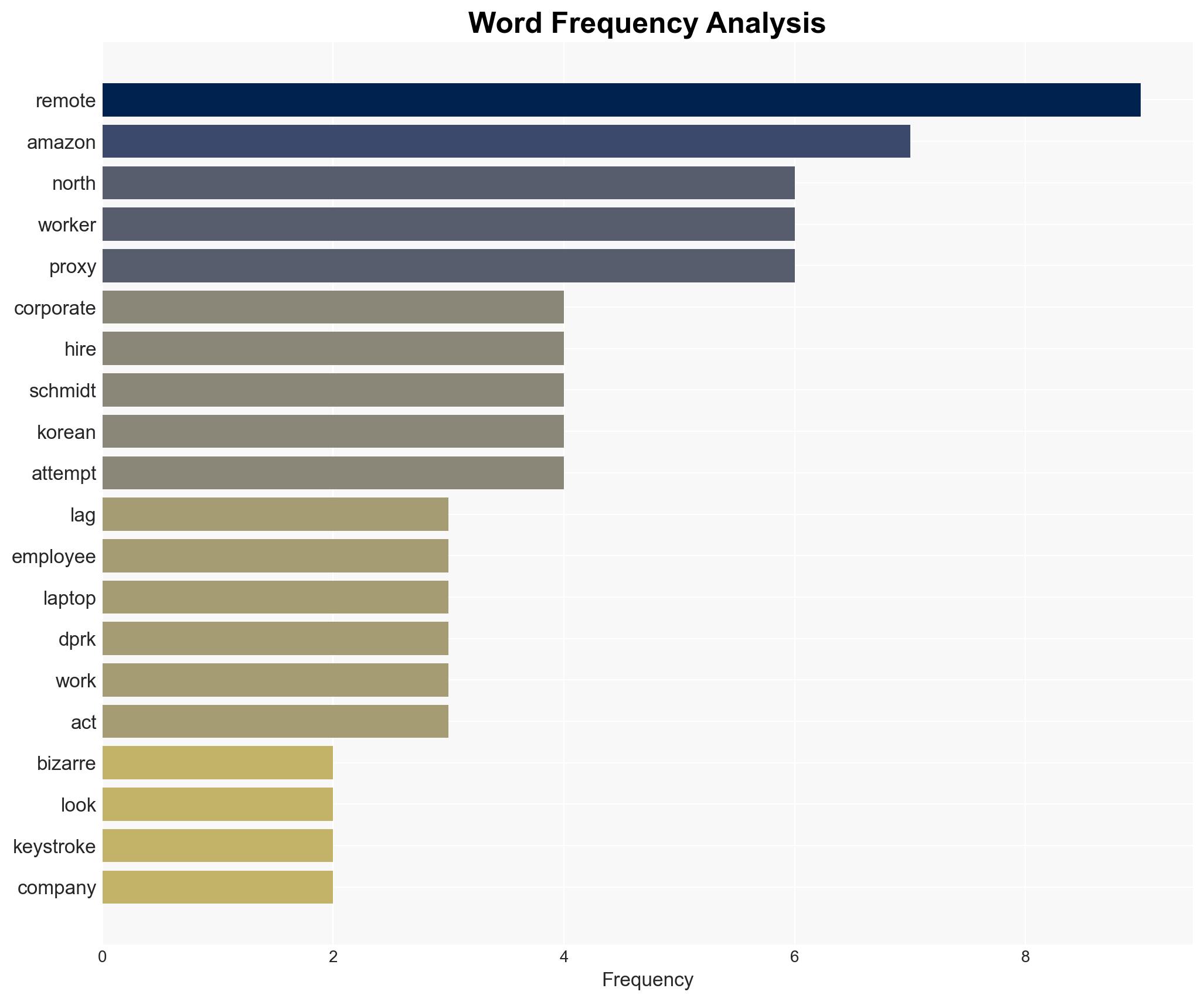
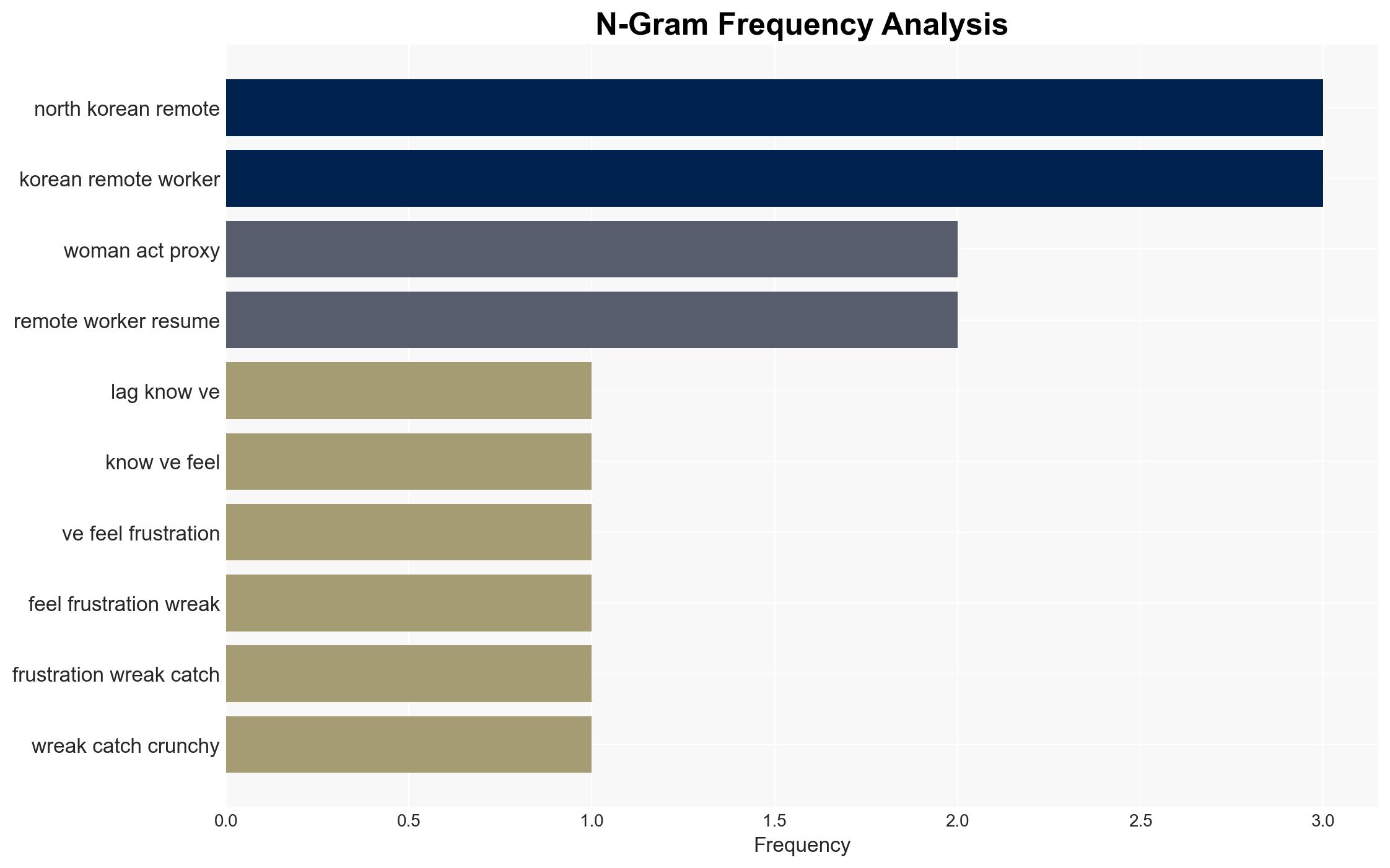
Amazon’s detection of keystroke lag led to the discovery of a North Korean operative posing as a US-based IT hire, highlighting a sophisticated DPRK strategy to circumvent sanctions and generate illicit revenue. This incident underscores the increasing trend of North Korean cyber operations targeting Western corporations. Overall confidence in this assessment is moderate, given the limited scope of available data and potential for deception.
2. Competing Hypotheses
- Hypothesis A: North Korean operatives are systematically infiltrating Western companies through remote work to generate revenue for the DPRK’s weapons program. This is supported by the detection of keystroke lag and the historical pattern of similar incidents. However, the exact scale and organizational structure of these operations remain uncertain.
- Hypothesis B: The incident is an isolated case of individual opportunism rather than a coordinated state-sponsored effort. While plausible, this is contradicted by the reported increase in similar attempts and the structured use of proxies, suggesting a broader strategy.
- Assessment: Hypothesis A is currently better supported due to the pattern of repeated incidents and the strategic use of proxies to bypass sanctions. Indicators such as a decrease in similar attempts or changes in proxy methodologies could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: North Korean operatives have the technical capability to mask their true locations; Amazon’s detection methods are reliable; the DPRK is actively seeking revenue through cyber means.
- Information Gaps: The full extent of North Korean infiltration across other companies and sectors; detailed organizational structure of the DPRK’s cyber operations.
- Bias & Deception Risks: Potential bias in Amazon’s reporting due to reputational concerns; possible DPRK deception tactics to obscure true operational scale.
4. Implications and Strategic Risks
This development could lead to increased scrutiny and regulatory measures on remote work arrangements, impacting global hiring practices and cybersecurity protocols.
- Political / Geopolitical: Potential escalation in diplomatic tensions between the US and DPRK, with increased sanctions or cyber countermeasures.
- Security / Counter-Terrorism: Heightened threat environment for corporations, necessitating enhanced security measures and inter-agency cooperation.
- Cyber / Information Space: Increased focus on cybersecurity infrastructure and monitoring capabilities to detect similar infiltration attempts.
- Economic / Social: Potential economic impact on companies reliant on remote work, with increased costs for compliance and security.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of remote work connections for anomalies; collaborate with law enforcement to investigate and mitigate ongoing threats.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms and government agencies to share intelligence; invest in advanced detection technologies.
- Scenario Outlook: Best: Reduction in DPRK cyber activities due to increased detection. Worst: Escalation in cyber attacks and geopolitical tensions. Most-Likely: Continued attempts with improved detection and mitigation strategies.
6. Key Individuals and Entities
- Stephen Schmidt, Amazon Chief Security Officer
- US Department of Justice
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, sanctions, North Korea, corporate security, remote work, international relations
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us