An exploit involving Spotlight plugins could let attackers steal private metadata – Idownloadblog.com
Published on: 2025-07-28
Intelligence Report: An exploit involving Spotlight plugins could let attackers steal private metadata – Idownloadblog.com
1. BLUF (Bottom Line Up Front)
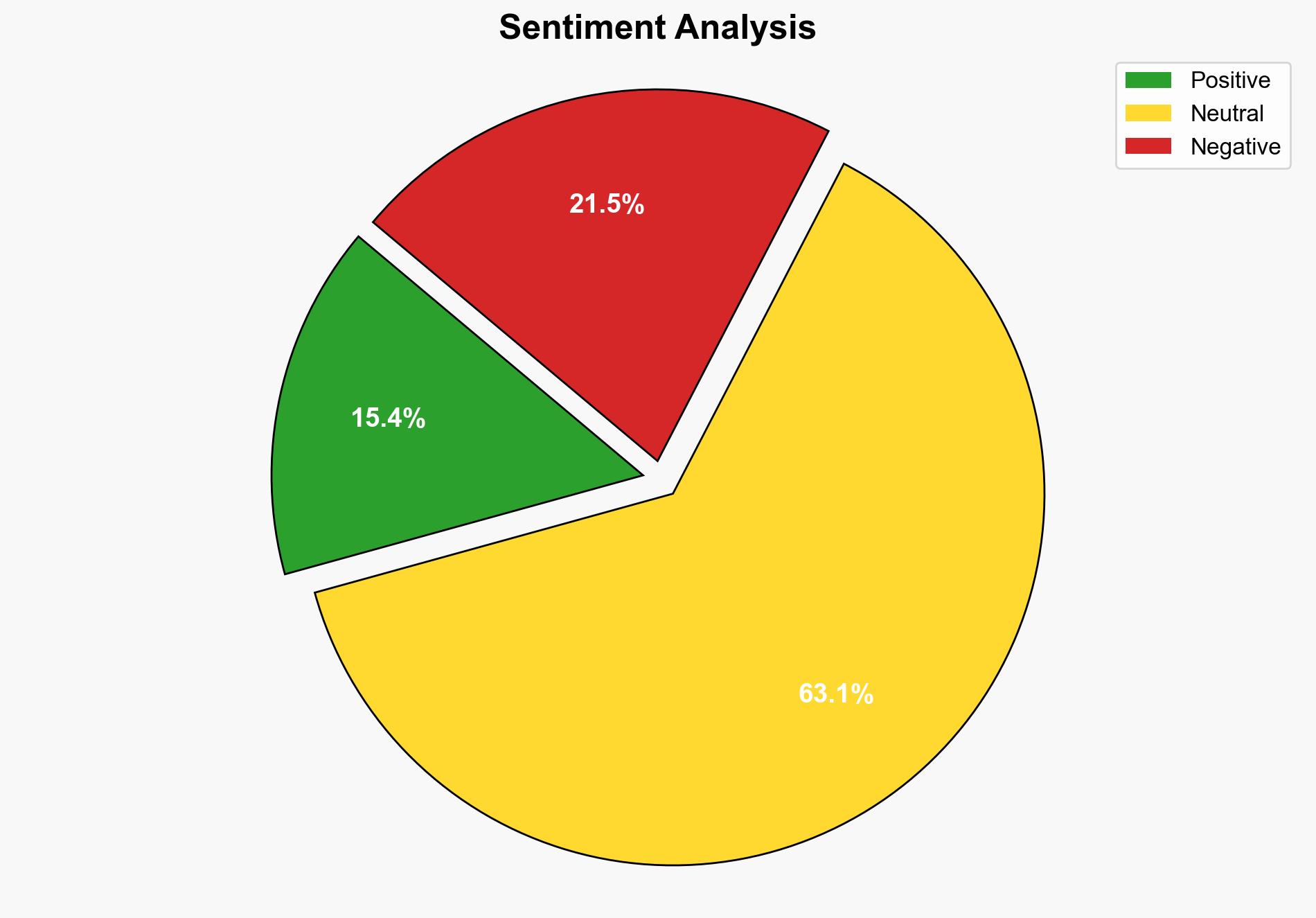
The most supported hypothesis is that the Spotlight plugin exploit represents a significant vulnerability that could be leveraged by attackers to access sensitive user data on macOS devices. The confidence level in this assessment is moderate due to the rapid response by Apple to patch the vulnerability. Recommended actions include enhancing monitoring of macOS systems for signs of exploitation and increasing awareness of potential vulnerabilities in third-party plugins.
2. Competing Hypotheses
1. **Hypothesis A**: The vulnerability in Spotlight plugins is a critical security flaw that could be exploited by attackers to access sensitive metadata from macOS devices, posing a significant risk to user privacy and security.
2. **Hypothesis B**: The vulnerability is not as severe as initially perceived due to Apple’s swift patching and the limited scope of exploitation in the wild, suggesting it poses a minimal threat to users.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the detailed description of the exploit’s capabilities and the potential for significant data exposure. Hypothesis B lacks evidence of limited exploitation and relies heavily on the assumption that the patch was timely and effective.
3. Key Assumptions and Red Flags
– **Assumptions**: Hypothesis A assumes that attackers have the capability and intent to exploit the vulnerability. Hypothesis B assumes that the patch effectively mitigates the risk and that there is no widespread exploitation.
– **Red Flags**: The lack of specific data on the number of devices affected or exploited raises questions about the true scope of the threat. The reliance on a single source (Microsoft) for the discovery and reporting of the vulnerability could introduce bias.
4. Implications and Strategic Risks
The exploit could lead to unauthorized access to sensitive user data, including geolocation and facial recognition information, which could be used for identity theft or targeted attacks. The potential for cascading threats exists if similar vulnerabilities are found in other macOS features or third-party applications. Economically, this could impact Apple’s reputation and consumer trust. Geopolitically, it could escalate tensions if state actors are involved in exploiting such vulnerabilities.
5. Recommendations and Outlook
- Enhance monitoring of macOS systems for unusual activity that may indicate exploitation attempts.
- Conduct a comprehensive review of third-party plugins to identify and mitigate similar vulnerabilities.
- Increase user awareness about the importance of timely software updates and potential risks associated with third-party applications.
- Scenario-based projections:
- **Best Case**: The patch effectively mitigates the risk, and no further exploitation occurs.
- **Worst Case**: Attackers find new ways to exploit similar vulnerabilities, leading to widespread data breaches.
- **Most Likely**: The patch reduces the immediate threat, but ongoing vigilance is required to prevent future exploits.
6. Key Individuals and Entities
– Microsoft (discovered the vulnerability)
– Apple (responsible for patching the vulnerability)
7. Thematic Tags
national security threats, cybersecurity, data privacy, software vulnerabilities