Android 16 has a clever way to defeat USB-based hacking – Android Headlines
Published on: 2025-04-25
Intelligence Report: Android 16’s Strategy to Counter USB-based Hacking
1. BLUF (Bottom Line Up Front)
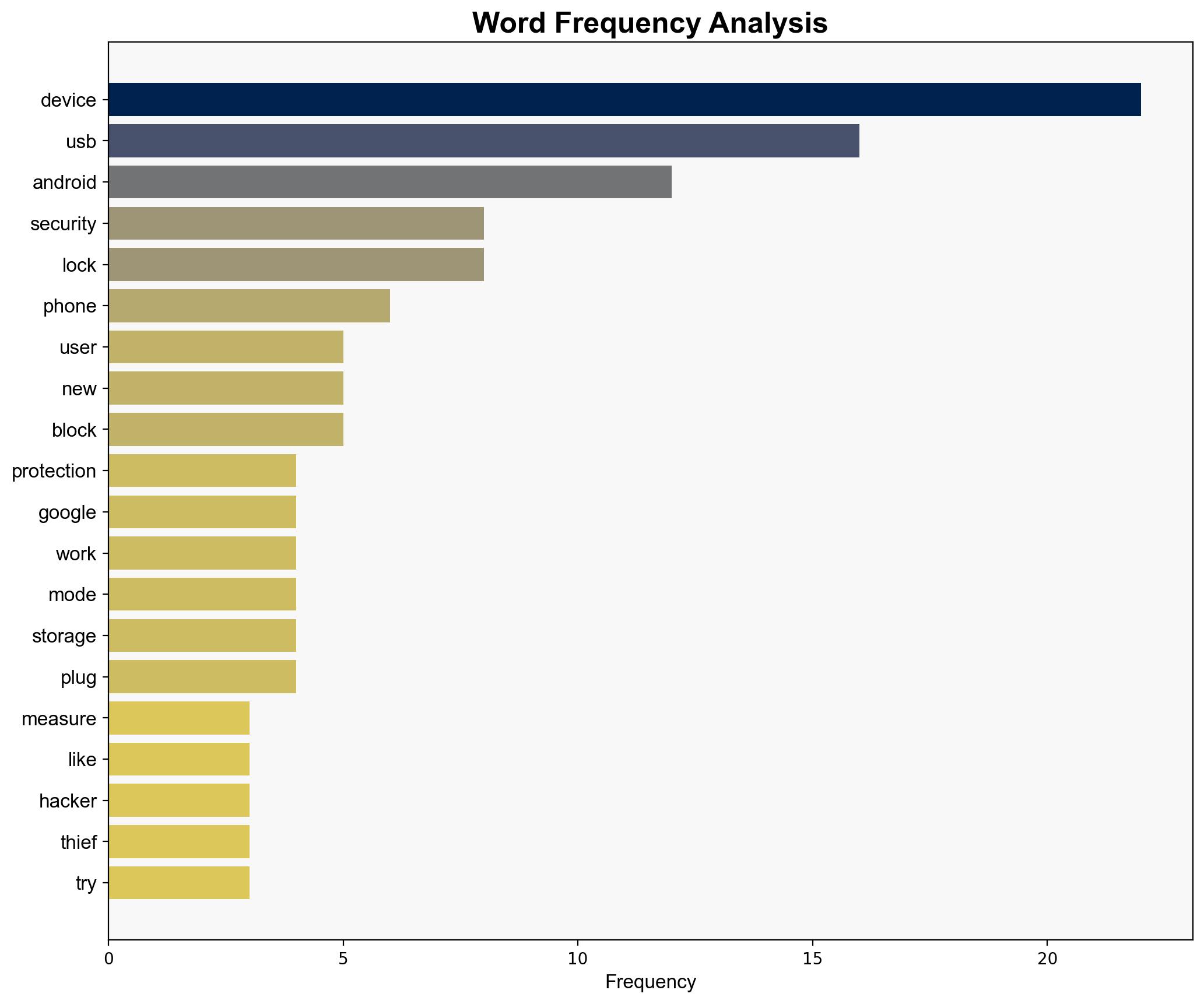
Android 16 introduces a security feature designed to mitigate USB-based hacking risks by blocking USB devices when the phone is locked. This measure enhances user data protection and reduces the likelihood of unauthorized access. The strategic implementation of this feature underscores Google’s commitment to bolstering cybersecurity on its platform.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
SWOT Analysis
Strengths: Enhanced security for user data, proactive protection against USB-based attacks.
Weaknesses: Potential inconvenience for users needing frequent USB access.
Opportunities: Positioning Android as a leader in mobile security, increasing user trust.
Threats: Potential for hackers to develop new methods to bypass this security feature.
Cross-Impact Matrix
This security feature may influence other tech companies to adopt similar measures, potentially leading to industry-wide shifts in mobile security protocols. It could also impact the development of USB peripherals, as manufacturers may need to adapt to new security standards.
Scenario Generation
Best Case: Widespread adoption of the feature leads to a significant reduction in USB-based cyber threats.
Worst Case: Hackers quickly find workarounds, diminishing the effectiveness of the security measure.
Most Likely: Gradual improvement in mobile security with incremental updates to address emerging threats.
3. Implications and Strategic Risks
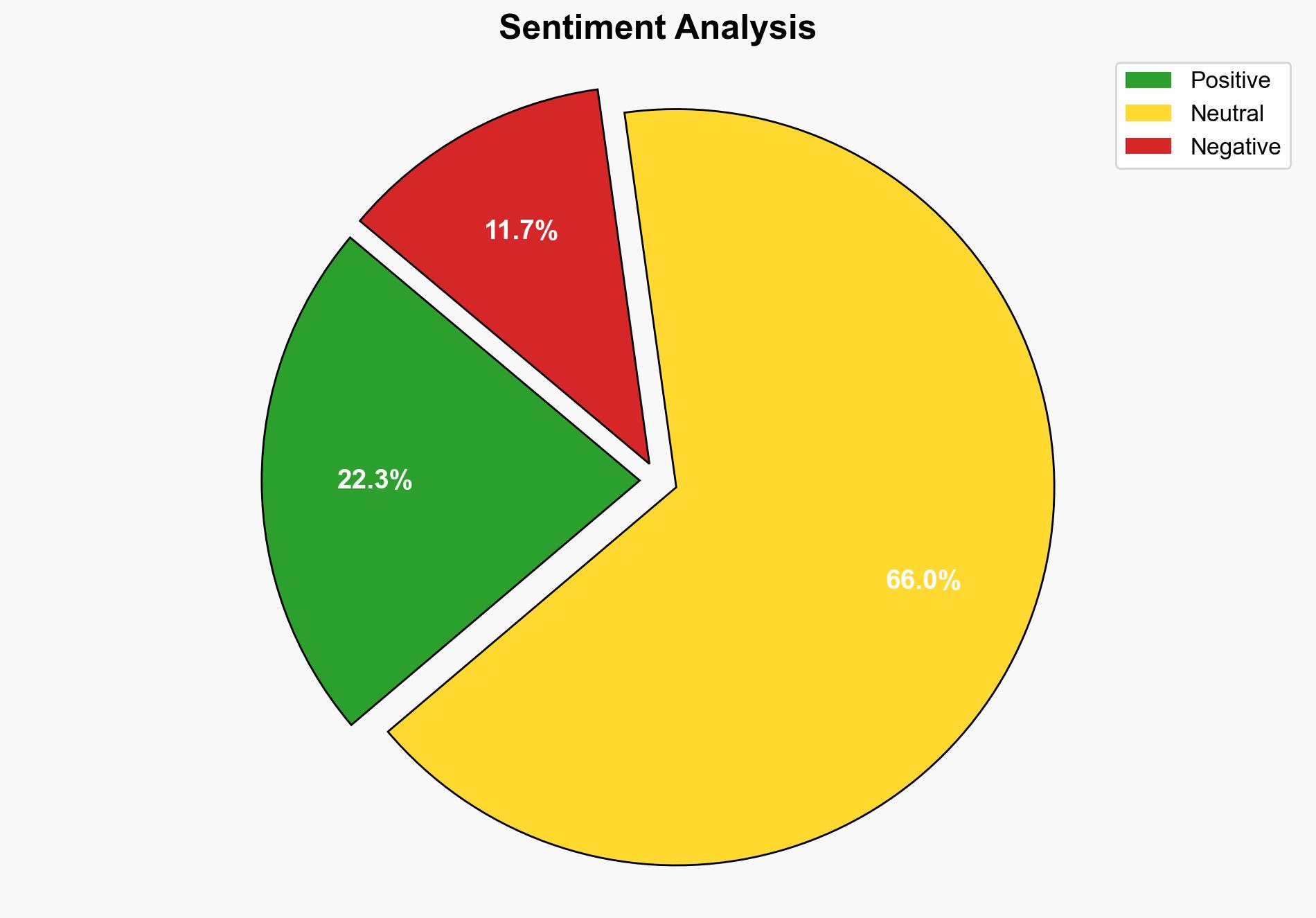
The introduction of this security feature could lead to a temporary decrease in USB-based hacking attempts. However, it may also prompt hackers to innovate new attack vectors. The feature’s success hinges on continuous updates and user adoption. Additionally, there is a risk of user dissatisfaction if the feature disrupts legitimate USB usage.
4. Recommendations and Outlook
- Encourage user education on the benefits and operation of the new security feature to enhance adoption.
- Continuously monitor and update the security protocol to address emerging threats and vulnerabilities.
- Engage with peripheral manufacturers to ensure compatibility and minimize user disruption.
- Scenario-based projections suggest a focus on adaptive security measures to maintain a competitive edge in mobile security.
5. Key Individuals and Entities
Mishaal Rahman (Android Authority)
6. Thematic Tags
(‘cybersecurity’, ‘mobile security’, ‘USB protection’, ‘Android security’, ‘data protection’)