APT28 Expands Credential-Harvesting Campaigns Targeting Turkish and Central Asian Energy and Policy Sectors
Published on: 2026-01-12
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Credential-harvesting attacks by APT28 hit Turkish European and Central Asian organizations
1. BLUF (Bottom Line Up Front)
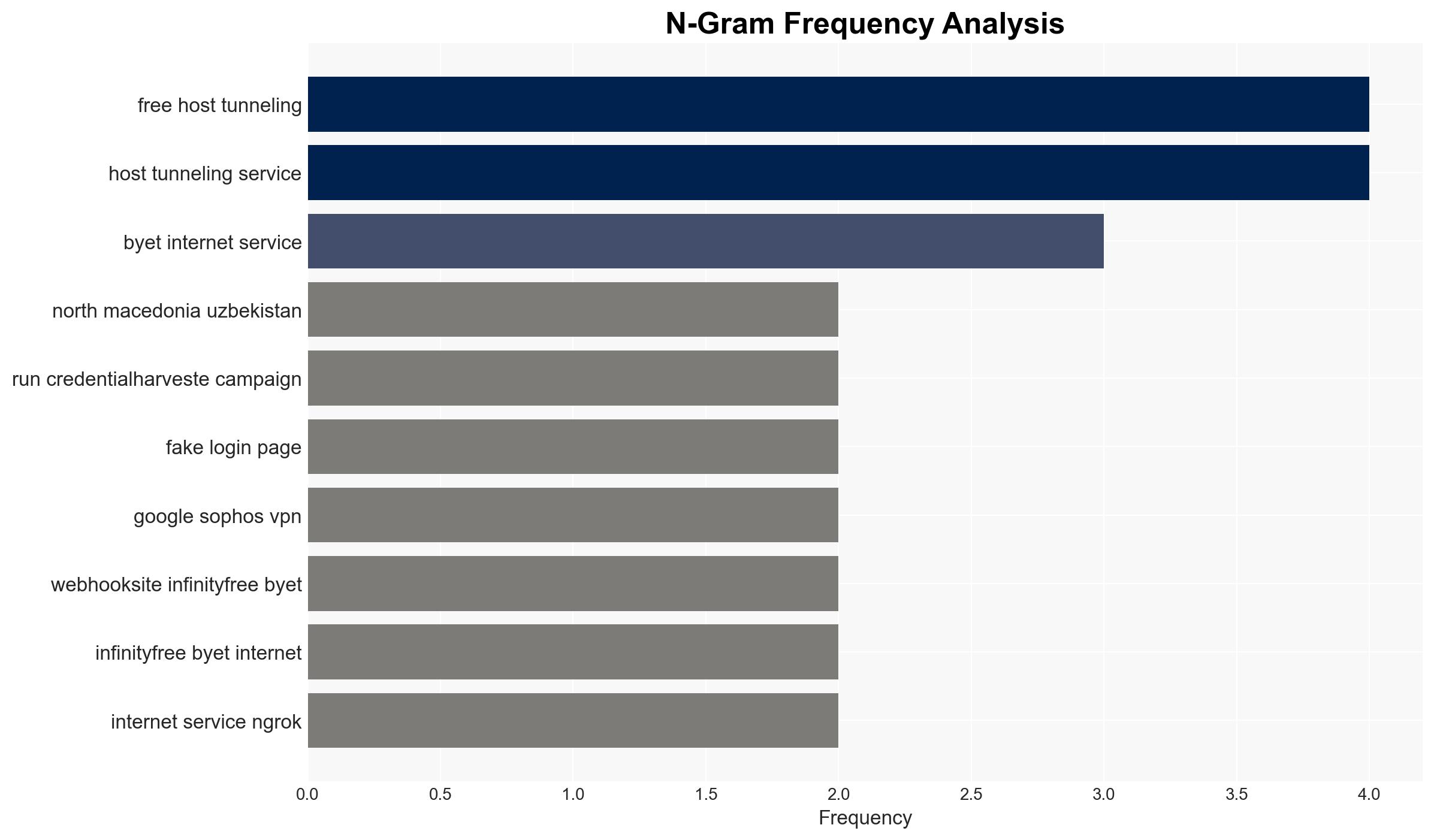
APT28, a Russia-linked cyberespionage group, has expanded its credential-harvesting operations targeting energy, nuclear, and policy sectors in Turkey, Europe, North Macedonia, and Uzbekistan. The group’s use of low-cost, regionally tailored cyber tactics aligns with Russian intelligence priorities. The most likely hypothesis is that these operations aim to gather strategic intelligence to support Russian geopolitical objectives. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: APT28’s attacks are primarily aimed at gathering intelligence to support Russian geopolitical and strategic interests. This is supported by the targeted sectors and regional focus, which align with known Russian priorities. However, the lack of direct attribution to Russian state directives remains a key uncertainty.
- Hypothesis B: The attacks are opportunistic cyber operations aimed at financial gain or disruption rather than strategic intelligence gathering. This is contradicted by the specific targeting of sectors and use of sophisticated, low-cost tactics, which are more indicative of state-sponsored espionage.
- Assessment: Hypothesis A is currently best supported due to the alignment of targets with Russian strategic interests and the sophisticated nature of the operations. Indicators that could shift this judgment include evidence of financial motives or non-state actor involvement.
3. Key Assumptions and Red Flags
- Assumptions: APT28 is acting under Russian state direction; the targeted sectors are of strategic interest to Russia; the use of low-cost tactics is a deliberate choice to maintain operational deniability.
- Information Gaps: Direct evidence linking APT28’s activities to specific Russian state directives; detailed impact assessments of the credential thefts.
- Bias & Deception Risks: Potential confirmation bias in attributing attacks to state-sponsored motives; risk of deception through false-flag operations or misattribution.
4. Implications and Strategic Risks
The expansion of APT28’s operations could lead to increased geopolitical tensions and a more hostile cyber environment. If left unchecked, these activities may embolden further cyber espionage efforts by state and non-state actors.
- Political / Geopolitical: Potential escalation in cyber conflict between Russia and affected states, impacting diplomatic relations.
- Security / Counter-Terrorism: Increased vulnerability of critical infrastructure sectors, necessitating enhanced cybersecurity measures.
- Cyber / Information Space: Heightened risk of information warfare and cyber espionage campaigns targeting sensitive sectors.
- Economic / Social: Potential destabilization of targeted sectors, leading to economic repercussions and public distrust in digital security.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of targeted sectors, deploy advanced threat detection systems, and increase awareness among potential targets.
- Medium-Term Posture (1–12 months): Develop international partnerships for intelligence sharing, invest in cybersecurity infrastructure, and conduct regular security audits.
- Scenario Outlook:
- Best: Successful mitigation of threats leads to reduced cyber espionage activities.
- Worst: Escalation of cyber operations results in significant geopolitical conflict.
- Most-Likely: Continued low-level cyber espionage with periodic spikes in activity, driven by geopolitical developments.
6. Key Individuals and Entities
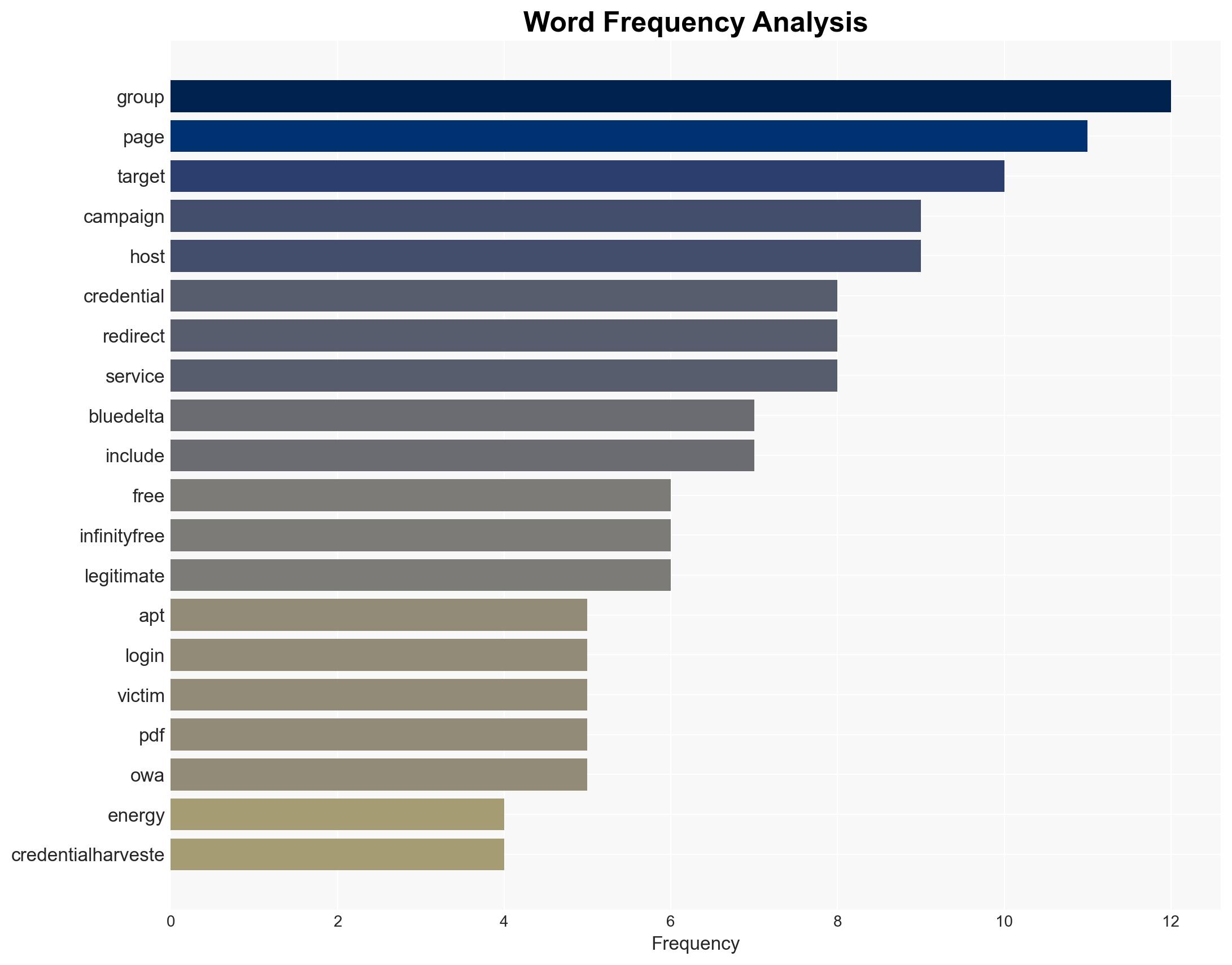
- APT28 (aka UAC-0001, Fancy Bear, Pawn Storm, Sofacy Group, Sednit, BlueDelta, STRONTIUM)
- Recorded Future’s Insikt Group
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, Russia, APT28, credential-harvesting, geopolitical tensions, energy sector
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us