APT28 Launches Prolonged Phishing Campaign Against UKR-net Users to Harvest Credentials
Published on: 2025-12-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: APT28 Targets Ukrainian UKR-net Users in Long-Running Credential Phishing Campaign
1. BLUF (Bottom Line Up Front)
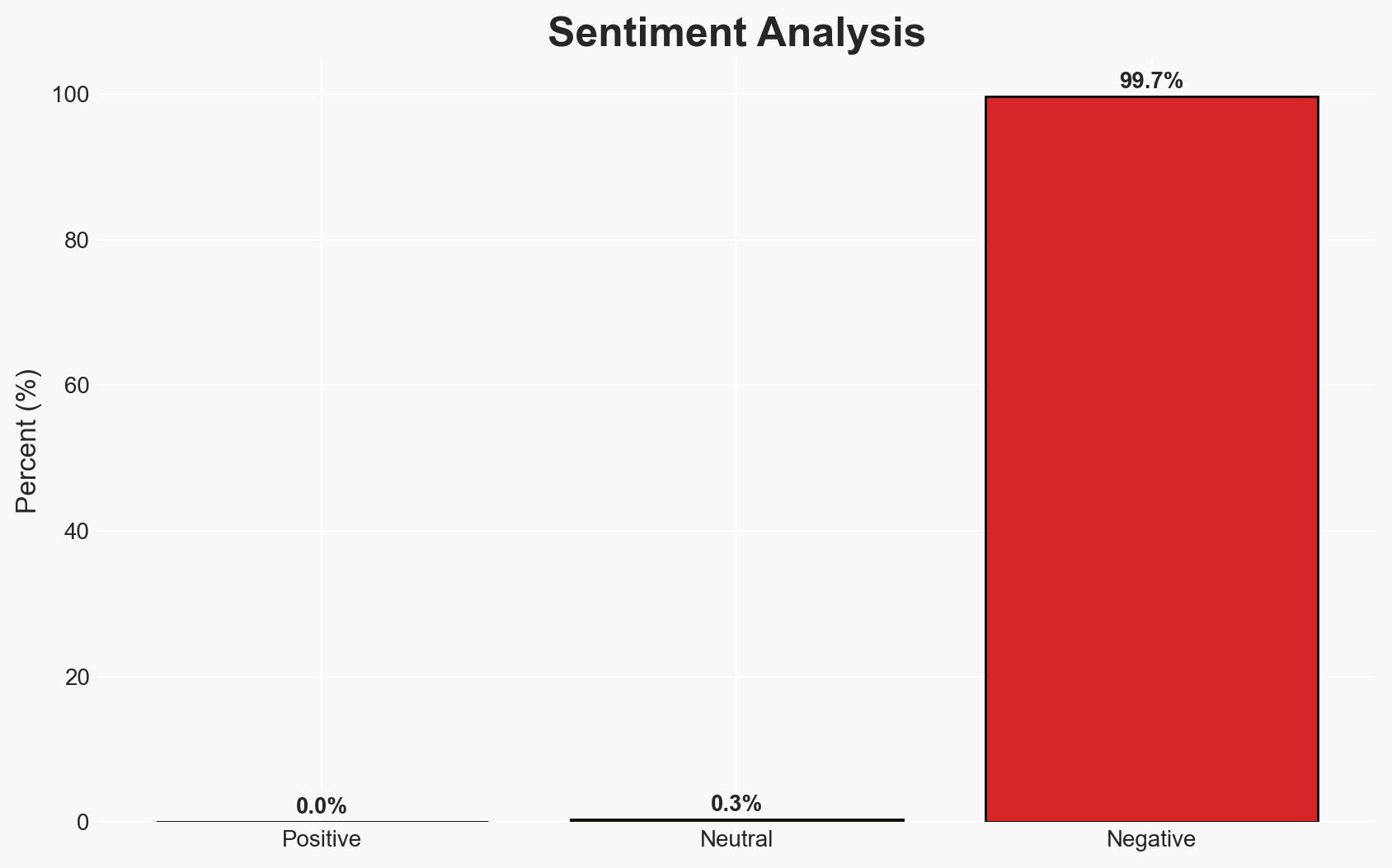
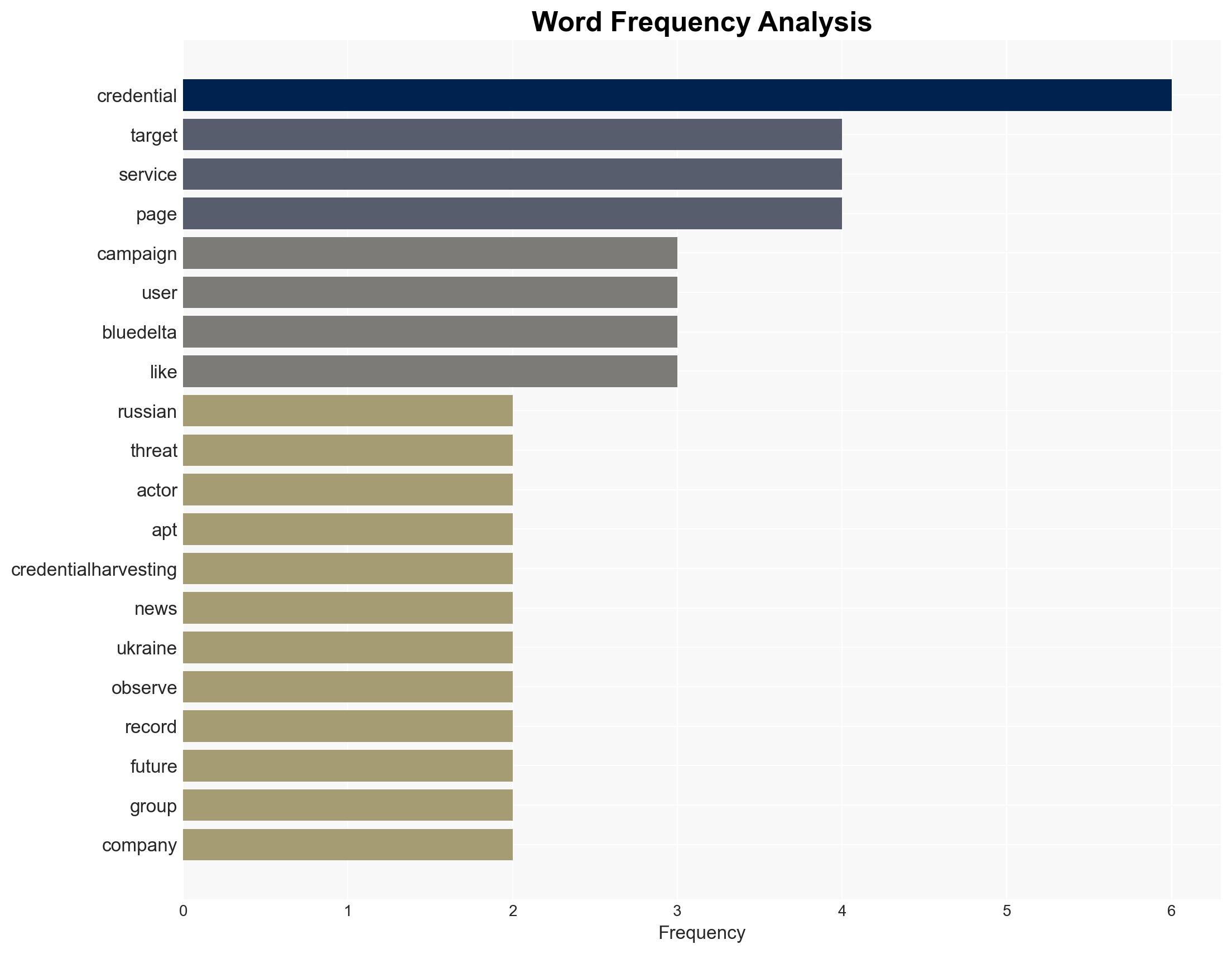
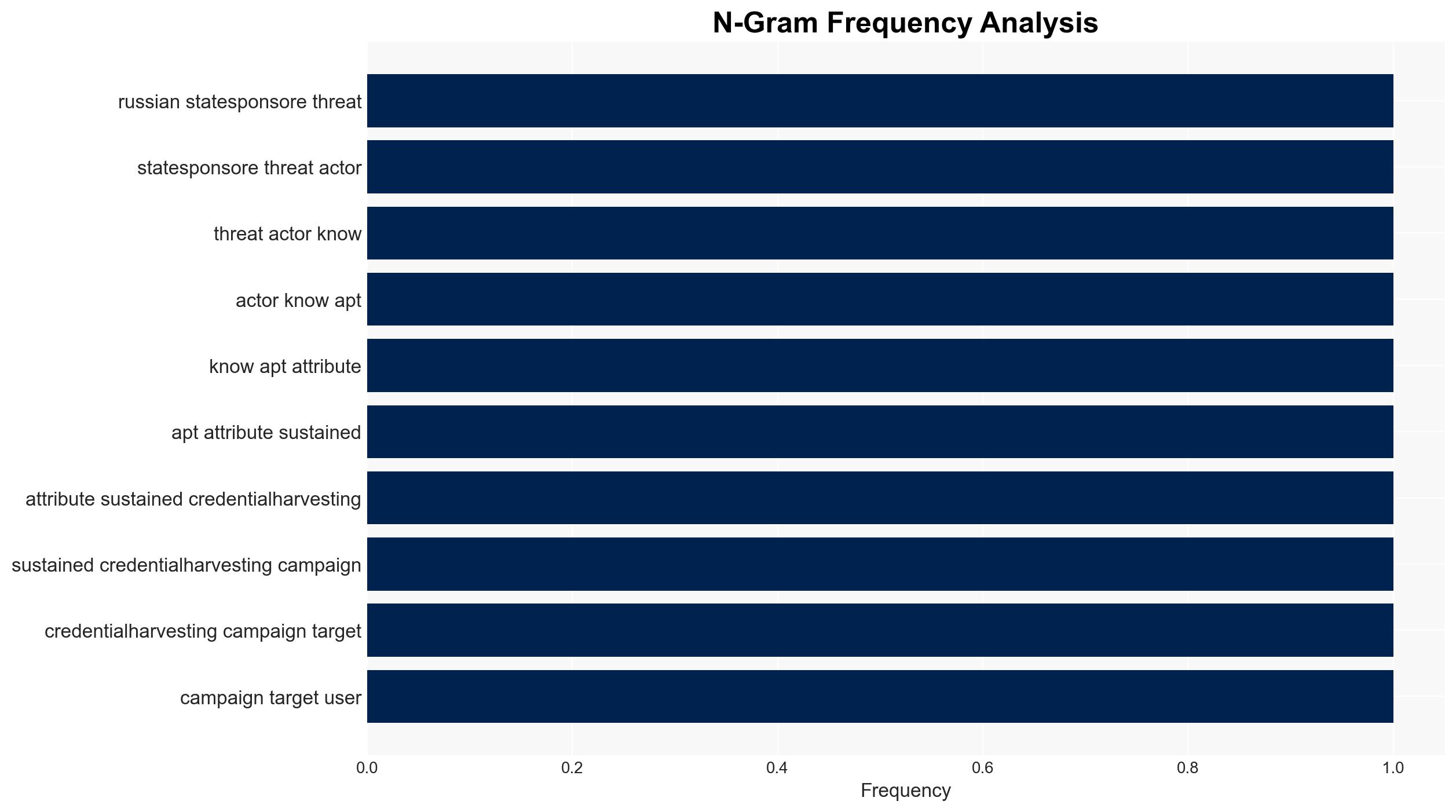
APT28, a Russian state-sponsored threat actor, is conducting a sustained credential phishing campaign targeting Ukrainian UKR-net users. This activity is likely aimed at intelligence collection to support Russian military objectives in Ukraine. The campaign’s use of adaptive techniques indicates a high level of sophistication. Overall confidence in this assessment is moderate due to the lack of specific target identification.
2. Competing Hypotheses
- Hypothesis A: APT28 is targeting UKR-net users to collect intelligence that supports Russian military objectives in Ukraine. This is supported by the group’s historical focus on credential theft and the current geopolitical context. However, the lack of specific target information introduces uncertainty.
- Hypothesis B: The campaign is a broader effort to disrupt Ukrainian communications and sow confusion, rather than a focused intelligence-gathering operation. This is less supported due to the sophistication and historical patterns of APT28’s operations.
- Assessment: Hypothesis A is currently better supported due to APT28’s known affiliation with the GRU and its historical focus on intelligence collection. Indicators that could shift this judgment include evidence of broader disruption efforts or identification of specific high-value targets.
3. Key Assumptions and Red Flags
- Assumptions: APT28 is acting under the direction of the GRU; the campaign’s primary goal is intelligence collection; the use of free hosting and tunneling services is an adaptive response to infrastructure takedowns.
- Information Gaps: Specific targets within the Ukrainian user base; the full extent of data compromised; potential collaboration with other threat actors.
- Bias & Deception Risks: Potential bias in attributing all activities to APT28 without considering other actors; deception by APT28 to mask true objectives or capabilities.
4. Implications and Strategic Risks
This campaign could exacerbate tensions between Russia and Ukraine, potentially influencing broader geopolitical dynamics and cyber defense postures.
- Political / Geopolitical: Increased cyber operations could lead to heightened tensions and retaliatory measures by Ukraine or its allies.
- Security / Counter-Terrorism: Potential for increased cyber threat levels and the need for enhanced defensive measures.
- Cyber / Information Space: The campaign highlights vulnerabilities in digital infrastructure and the need for improved cyber hygiene among users.
- Economic / Social: Potential impacts on public trust in digital services and increased costs for cybersecurity measures.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase monitoring of phishing activities targeting Ukrainian digital services; enhance public awareness campaigns on phishing threats.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for threat intelligence sharing; invest in infrastructure resilience and incident response capabilities.
- Scenario Outlook:
- Best Case: Effective mitigation reduces the impact of the campaign, and diplomatic efforts de-escalate tensions.
- Worst Case: Escalation of cyber operations leads to significant disruptions in Ukrainian digital services and broader geopolitical conflict.
- Most-Likely: Continued low-level cyber operations with periodic escalations, requiring sustained defensive efforts.
6. Key Individuals and Entities
- APT28 (also known as BlueDelta, Fancy Bear, etc.)
- GRU (Main Directorate of the General Staff of the Russian Federation’s Armed Forces)
- Recorded Future’s Insikt Group
- UKR.net users (general target group)
7. Thematic Tags
cybersecurity, cyber-espionage, phishing, Russian intelligence, Ukraine conflict, GRU, cyber defense, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us