Are your neighbors stealing your Wi-Fi Heres what the law says – TalkAndroid
Published on: 2025-07-20
Intelligence Report: Are your neighbors stealing your Wi-Fi? Here’s what the law says – TalkAndroid
1. BLUF (Bottom Line Up Front)
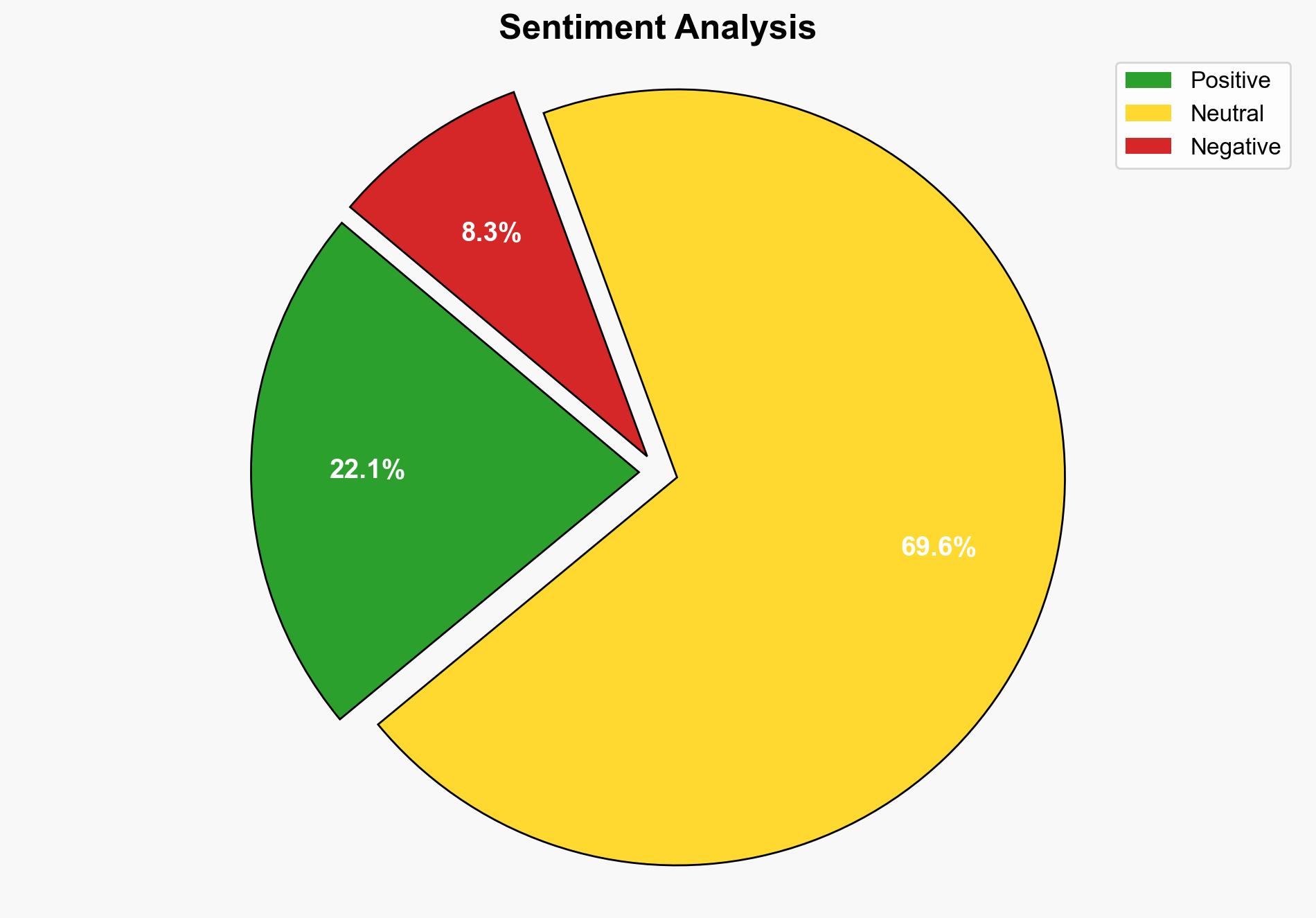
Unauthorized access to Wi-Fi networks by neighbors poses significant security risks, including potential data breaches and compromised network performance. Effective detection and protection measures are essential to safeguard personal and network security. Key recommendations include enhancing encryption protocols, implementing MAC address filtering, and regularly monitoring network activity.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations reveal that unauthorized Wi-Fi access can lead to vulnerabilities such as data interception and network manipulation. Understanding adversary tactics helps in developing robust defense mechanisms.
Indicators Development
Key indicators of unauthorized access include unexpected decreases in internet speed and unfamiliar devices on the network. Regular network scans can detect these anomalies early.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of unauthorized access in densely populated areas, with potential escalation to more severe cyber threats if left unaddressed.
Network Influence Mapping
Mapping network connections highlights potential intruders and helps in understanding the influence and reach of unauthorized users within the network.
3. Implications and Strategic Risks
Unauthorized Wi-Fi access can lead to broader cybersecurity threats, including identity theft and unauthorized data access. The systemic vulnerability of unsecured networks can have cascading effects, potentially impacting personal and organizational data integrity.
4. Recommendations and Outlook
- Enhance network security by upgrading to WPA3 encryption and regularly changing passwords.
- Implement MAC address filtering to restrict network access to approved devices only.
- Conduct regular network audits to identify and remove unauthorized devices.
- Scenario Projections:
- Best Case: Implementation of robust security measures leads to a secure and efficient network.
- Worst Case: Continued unauthorized access results in data breaches and network exploitation.
- Most Likely: Incremental improvements in security reduce unauthorized access incidents.
5. Key Individuals and Entities
This section is not applicable as the report focuses on general network security practices rather than specific individuals or entities.
6. Thematic Tags
cybersecurity, network security, unauthorized access, data protection