Asian State-Sponsored Hackers Breach Critical Infrastructure in 37 Countries, Targeting Government Entities
Published on: 2026-02-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Asia-based government spies quietly broke into critical networks across 37 countries
1. BLUF (Bottom Line Up Front)
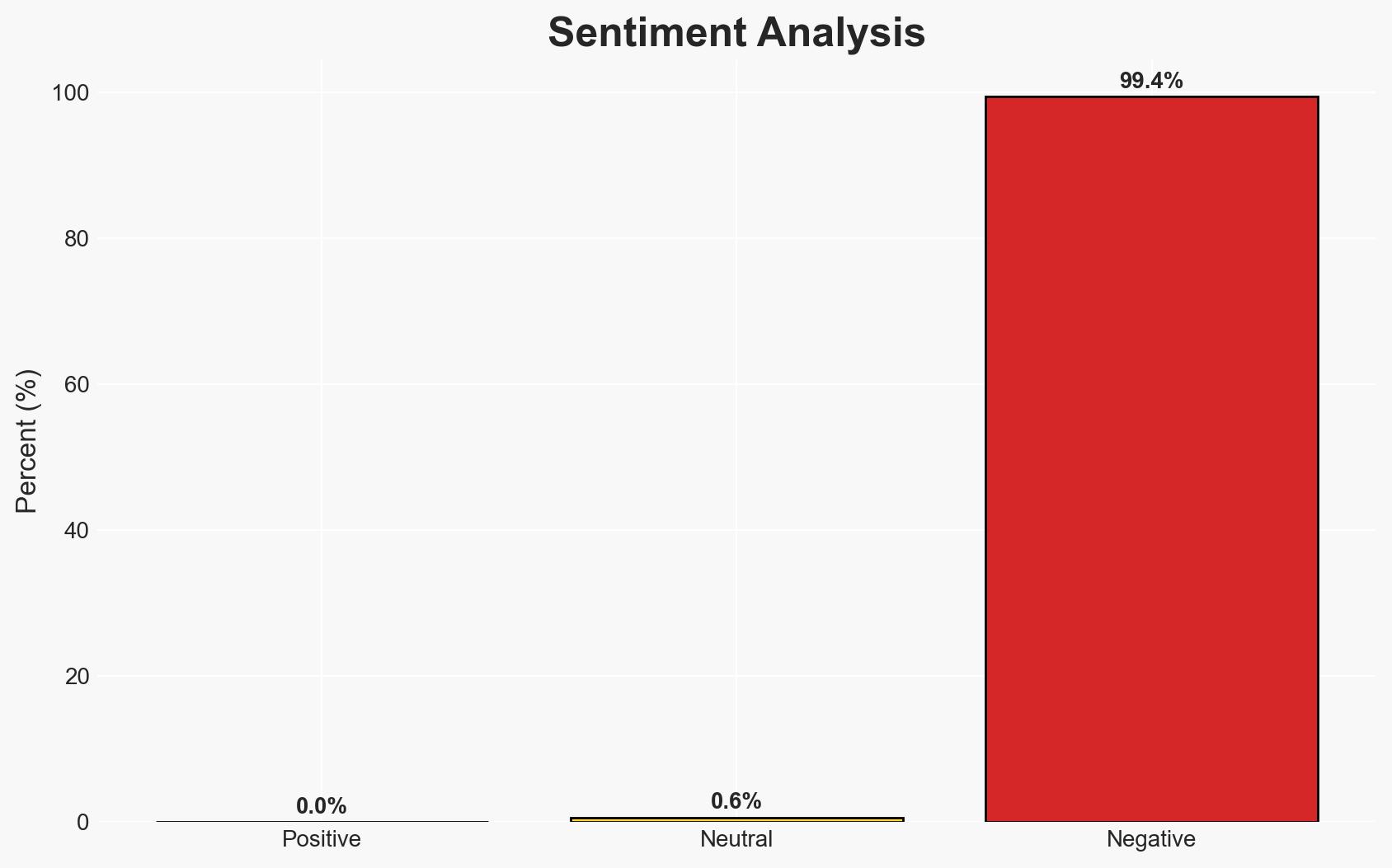
An Asia-based state-aligned cyber group, identified as TGR-STA-1030, has compromised critical networks in 37 countries, targeting government and infrastructure organizations. The espionage campaign has significant implications for national security and key services, with moderate confidence in the assessment due to limited attribution to a specific nation. The group’s activities pose a substantial threat to global cybersecurity and political stability.
2. Competing Hypotheses
- Hypothesis A: TGR-STA-1030 is an independent cyber group operating with tacit state approval. This is supported by the scale and sophistication of the operations, targeting high-value government entities, and the lack of direct attribution to a specific country. Key uncertainties include the group’s exact origin and the extent of state involvement.
- Hypothesis B: TGR-STA-1030 is a direct arm of a specific Asian government conducting state-sponsored cyber-espionage. This hypothesis is less supported due to the absence of explicit attribution by researchers and the potential for false flag operations to obscure true origins.
- Assessment: Hypothesis A is currently better supported due to the operational characteristics and lack of direct attribution. Indicators that could shift this judgment include credible attribution to a specific nation or evidence of direct governmental control over the group.
3. Key Assumptions and Red Flags
- Assumptions: The cyber group operates with some level of state approval; the group’s primary objective is espionage; the methods and tools used are indicative of advanced persistent threat (APT) capabilities.
- Information Gaps: Specific attribution to a nation-state; detailed motivations behind targeting specific entities; the full extent of data exfiltration and its potential uses.
- Bias & Deception Risks: Potential bias in open-source reporting; risk of misattribution due to sophisticated obfuscation techniques; possibility of disinformation campaigns to mislead attribution efforts.
4. Implications and Strategic Risks
The ongoing cyber-espionage campaign by TGR-STA-1030 could lead to heightened geopolitical tensions and increased cyber defense measures globally. The group’s activities may prompt retaliatory cyber operations or sanctions, affecting international relations.
- Political / Geopolitical: Potential for diplomatic fallout and increased scrutiny on Asian cyber activities; risk of retaliatory actions by affected nations.
- Security / Counter-Terrorism: Increased threat to national security infrastructures; potential for exploitation by other malicious actors.
- Cyber / Information Space: Escalation in cyber warfare tactics; increased demand for cybersecurity solutions and international cooperation.
- Economic / Social: Potential economic impacts from compromised financial data; erosion of public trust in government cybersecurity capabilities.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of critical networks; collaborate with international partners to share threat intelligence; conduct thorough forensic investigations of compromised systems.
- Medium-Term Posture (1–12 months): Develop and implement resilience measures; strengthen public-private partnerships in cybersecurity; invest in advanced threat detection and response capabilities.
- Scenario Outlook:
- Best: Successful attribution and diplomatic resolution reduce tensions.
- Worst: Escalation to cyber warfare with significant geopolitical and economic impacts.
- Most-Likely: Continued espionage with incremental improvements in global cyber defenses.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, national security, geopolitical tensions, advanced persistent threat, cyber defense, international cooperation
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us