Assessing Global Resilience: Countries Prepared to Counter State-Sponsored Cyber Threats
Published on: 2026-02-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Which countries are best-placed to resist state-supported cyber-attacks A government advisor explains
1. BLUF (Bottom Line Up Front)
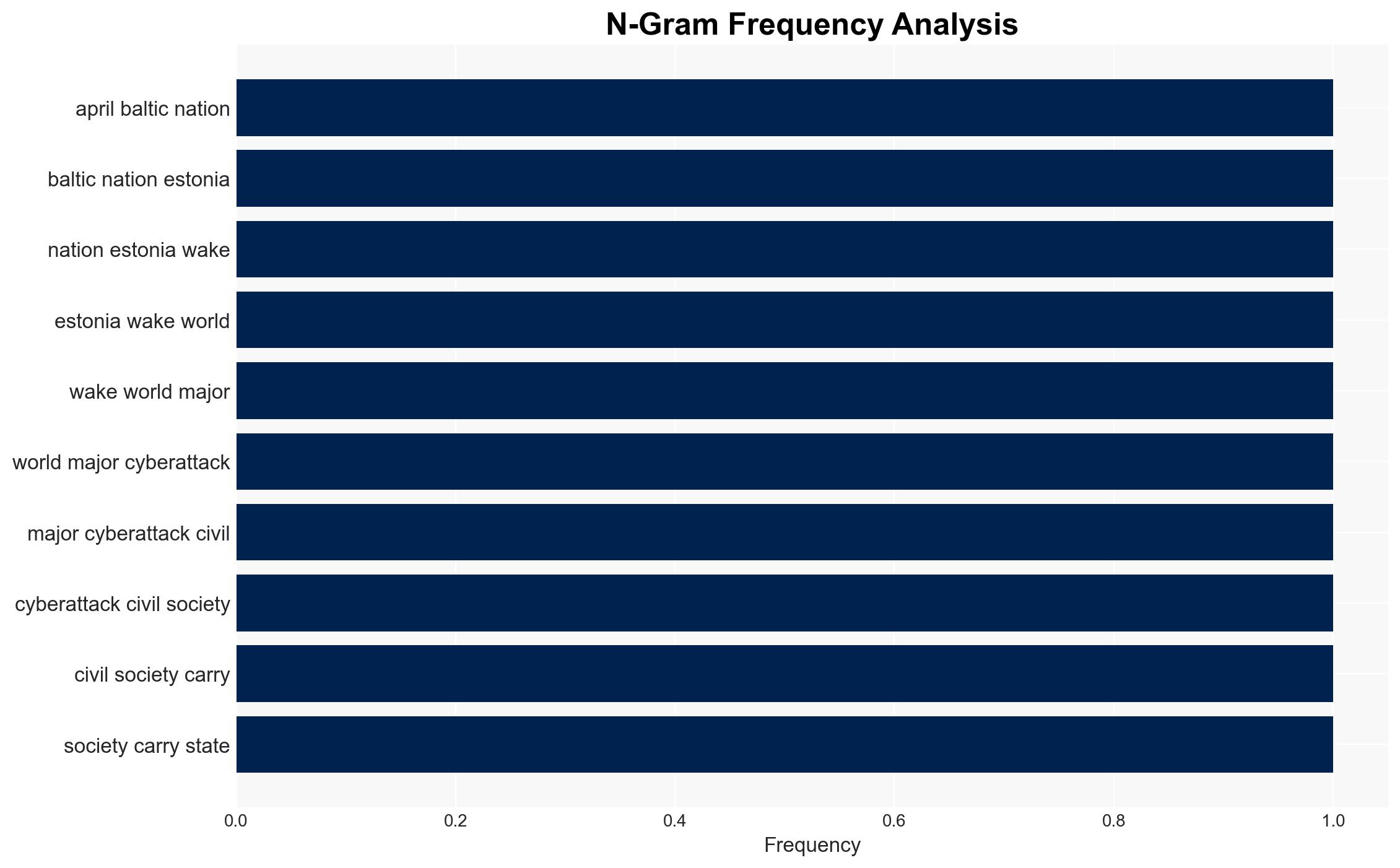
Estonia has emerged as a leading nation in cybersecurity resilience due to its proactive measures following a significant cyber-attack in 2007, while the UK is currently enhancing its cybersecurity posture but remains vulnerable due to historical underinvestment. The most likely hypothesis is that Estonia’s model could inform UK improvements, but substantial challenges remain. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Estonia’s proactive cybersecurity measures and international collaboration make it better positioned to resist state-supported cyber-attacks than the UK. This is supported by Estonia’s high ranking in global cybersecurity indices and its hosting of NATO’s Cyber Defence Centre of Excellence. However, uncertainties include the evolving nature of cyber threats and Estonia’s reliance on international support.
- Hypothesis B: The UK’s recent initiatives, such as the Cyber Action Plan and increased funding, will significantly enhance its cybersecurity resilience, potentially matching or surpassing Estonia’s capabilities. Contradicting evidence includes the UK’s current vulnerabilities and the challenge of attracting private-sector talent to public roles.
- Assessment: Hypothesis A is currently better supported due to Estonia’s established track record and infrastructure. Indicators that could shift this judgment include successful implementation of the UK’s Cyber Action Plan and measurable improvements in its cybersecurity posture.
3. Key Assumptions and Red Flags
- Assumptions: Estonia will maintain its current level of cybersecurity investment and international collaboration; the UK’s Cyber Action Plan will be fully funded and implemented; cyber threats will continue to evolve in complexity.
- Information Gaps: Detailed data on the effectiveness of Estonia’s cybersecurity measures and the specific vulnerabilities within the UK’s public sector IT systems.
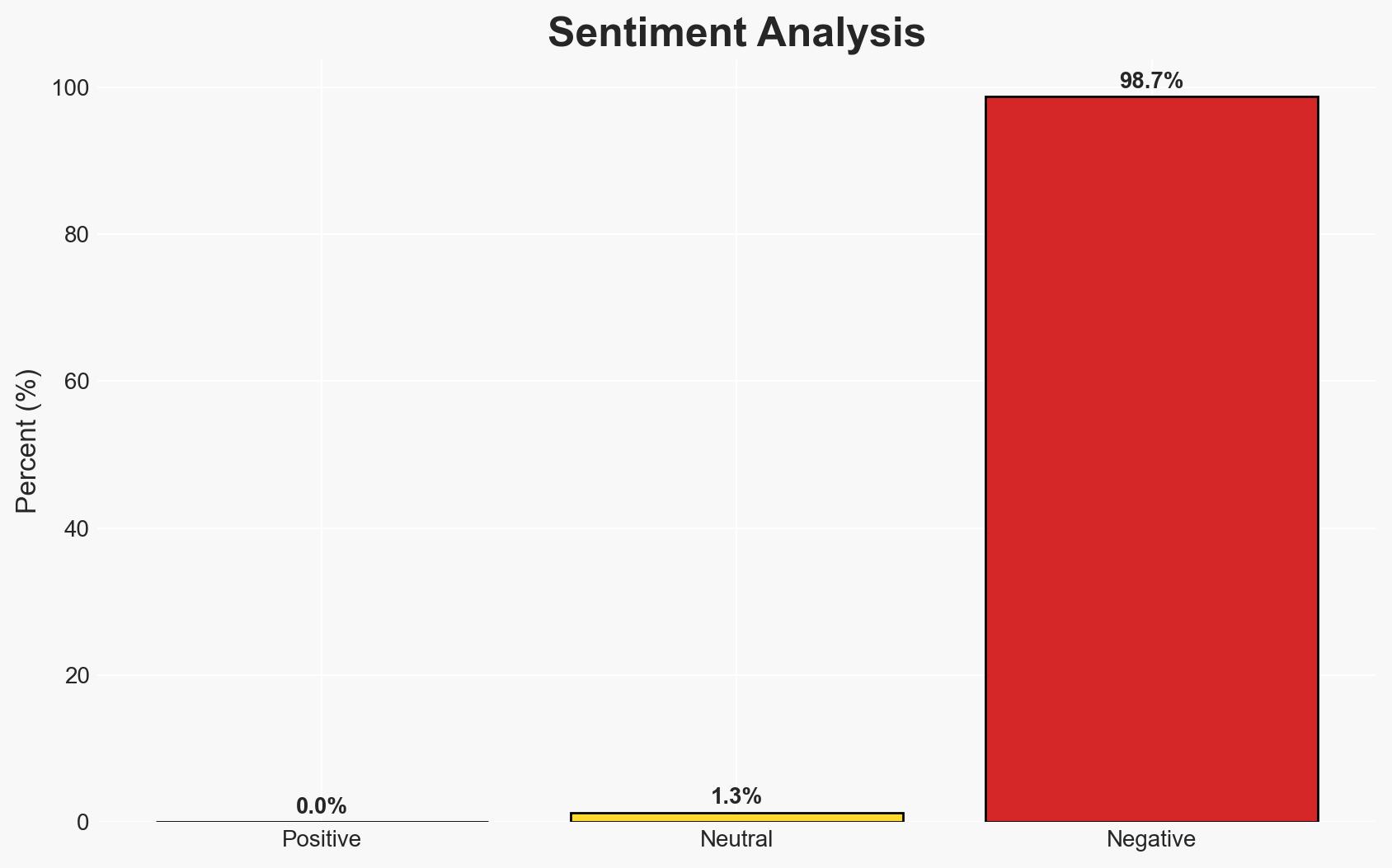
- Bias & Deception Risks: Potential bias in reporting from sources with vested interests in promoting Estonia’s model or the UK’s initiatives; possible deception in cyber threat reporting to influence public perception.
4. Implications and Strategic Risks
The development of cybersecurity capabilities in Estonia and the UK could influence regional security dynamics and set benchmarks for other nations. However, failure to address vulnerabilities could lead to significant disruptions.
- Political / Geopolitical: Increased cybersecurity capabilities could deter state-sponsored cyber aggression, but may also escalate tensions with adversaries.
- Security / Counter-Terrorism: Enhanced cybersecurity could improve national resilience against cyber-terrorism and protect critical infrastructure.
- Cyber / Information Space: Improved defenses may lead to more sophisticated cyber-attack strategies by adversaries, requiring continuous adaptation.
- Economic / Social: Successful cybersecurity measures could protect economic interests and maintain public trust, while failures could lead to economic losses and social unrest.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive audit of current cybersecurity measures in the UK; enhance information sharing between Estonia and the UK.
- Medium-Term Posture (1–12 months): Develop public-private partnerships to attract cybersecurity talent; invest in continuous training and development for cybersecurity personnel.
- Scenario Outlook:
- Best: Successful implementation of cybersecurity measures leads to reduced cyber incidents.
- Worst: Continued vulnerabilities result in a major cyber-attack causing significant disruptions.
- Most-Likely: Incremental improvements in cybersecurity posture with ongoing challenges in talent acquisition and threat adaptation.
6. Key Individuals and Entities
- Richard Horne, CEO of the National Cyber Security Centre
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
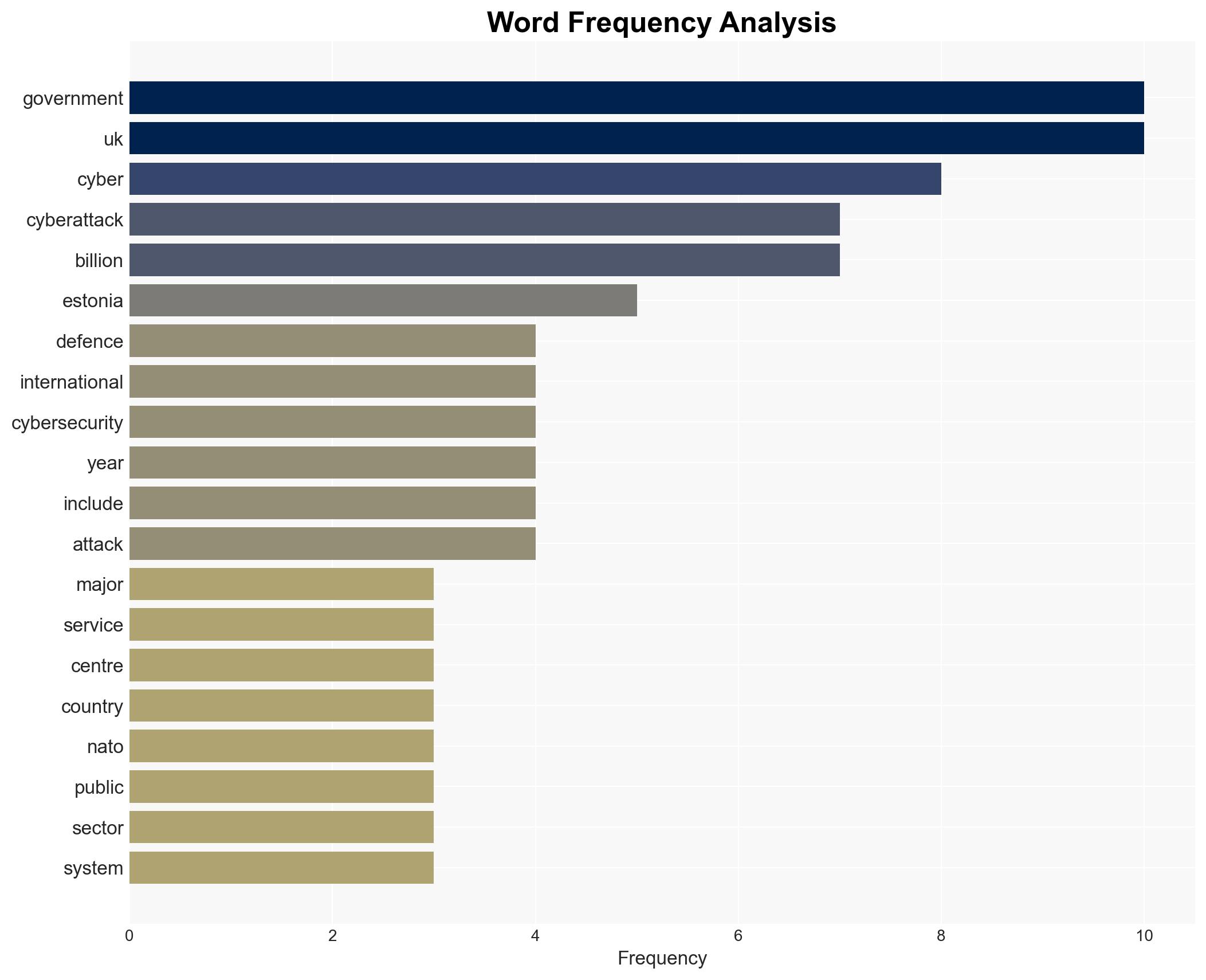
cybersecurity, state-sponsored attacks, Estonia, UK, cyber resilience, public-private partnerships, cyber defense
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us