Astaroth malware exploits WhatsApp to target Brazilian users with new automated worm campaign
Published on: 2026-01-08
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Astaroth banking malware returns with WhatsApp-based worm targeting Brazil
1. BLUF (Bottom Line Up Front)
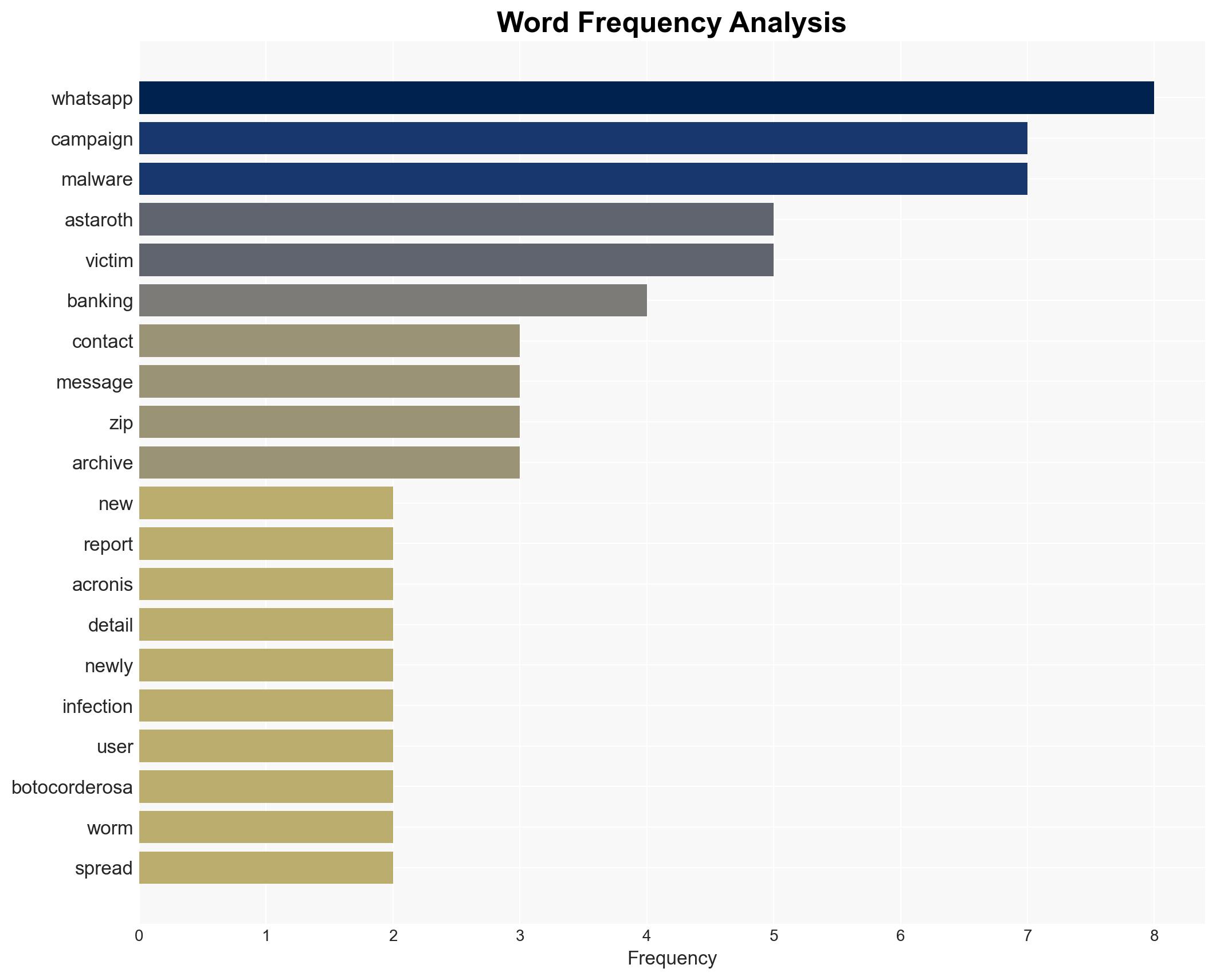
The Astaroth banking malware has resurfaced with a new campaign leveraging WhatsApp to propagate among Brazilian users. This development marks a significant evolution in malware distribution tactics, combining social engineering with multiplatform propagation. The campaign’s sophistication suggests a potential for broader regional or global impact. Overall confidence in this assessment is moderate, given the specific targeting and technical details provided.
2. Competing Hypotheses
- Hypothesis A: The Astaroth campaign is primarily targeting Brazilian users to exploit local banking systems and user behaviors. This is supported by the use of Portuguese in social engineering messages and the initial targeting of Brazilian WhatsApp users. However, the broader implications of multilanguage frameworks suggest potential for expansion beyond Brazil.
- Hypothesis B: The campaign is a testbed for a larger, global operation aimed at refining techniques for broader deployment. The use of Python and Delphi indicates a versatile approach that could be adapted for other regions. Contradicting this is the current focus on Brazilian users and the absence of evidence indicating immediate global targeting.
- Assessment: Hypothesis A is currently better supported due to the specific targeting of Brazilian users and the use of localized social engineering tactics. Indicators that could shift this judgment include evidence of similar campaigns in other regions or adaptations of the malware to target different languages and banking systems.
3. Key Assumptions and Red Flags
- Assumptions: The campaign’s primary goal is financial theft from Brazilian banking users; WhatsApp’s popularity in Brazil makes it an effective vector; the malware’s current capabilities are accurately described in the report.
- Information Gaps: Lack of data on the malware’s effectiveness in stealing credentials; absence of information on any countermeasures being deployed by Brazilian financial institutions.
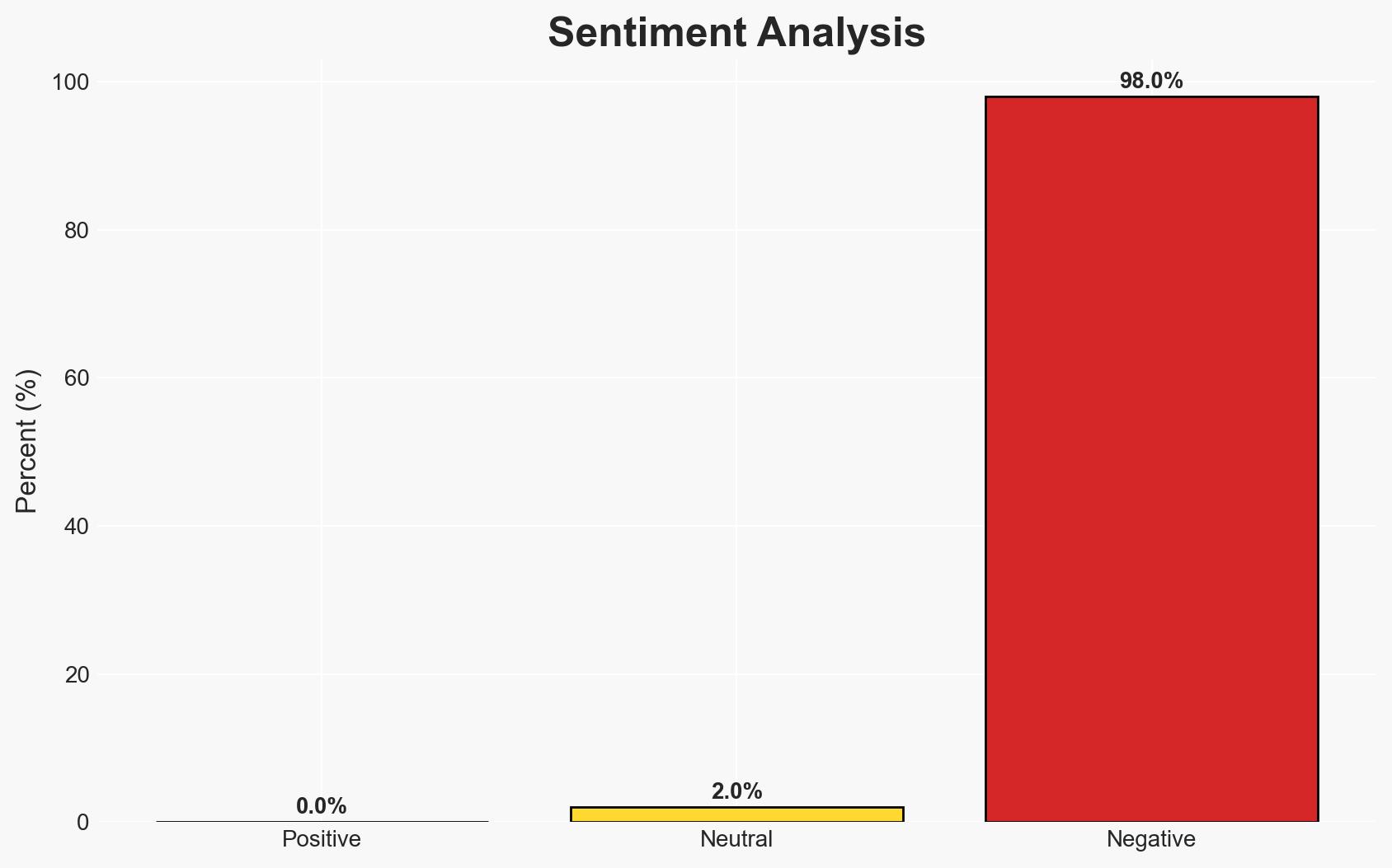
- Bias & Deception Risks: Potential bias from the cybersecurity company in highlighting threats to promote their services; the possibility of misinformation or exaggeration in the report to increase perceived threat levels.
4. Implications and Strategic Risks
The evolution of Astaroth malware using WhatsApp as a vector could set a precedent for future cyber campaigns, influencing both cyber defense strategies and malware development trends.
- Political / Geopolitical: Increased cyber threat perception could strain Brazil’s international relations, particularly if foreign nationals are affected.
- Security / Counter-Terrorism: The campaign could inspire similar tactics among cybercriminals and terrorist organizations, complicating law enforcement efforts.
- Cyber / Information Space: The use of social engineering and multiplatform propagation could drive advancements in cybersecurity defenses and information operations.
- Economic / Social: Potential financial losses and erosion of trust in digital communication platforms could impact economic stability and social cohesion.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase monitoring of WhatsApp communications for malicious activity; engage with Brazilian financial institutions to enhance security measures.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms to share threat intelligence; invest in public awareness campaigns about social engineering tactics.
- Scenario Outlook:
- Best: The campaign is contained within Brazil, with minimal financial impact and improved cybersecurity defenses.
- Worst: The malware spreads globally, causing significant financial and reputational damage to affected institutions.
- Most-Likely: The campaign remains focused on Brazil, but prompts regional cybersecurity enhancements and increased vigilance.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, banking malware, social engineering, Brazil, WhatsApp, cyber threat, malware propagation
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us