AT&T customer data breach exposes 176 million records, heightening risks for individuals and security.
Published on: 2026-02-03
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
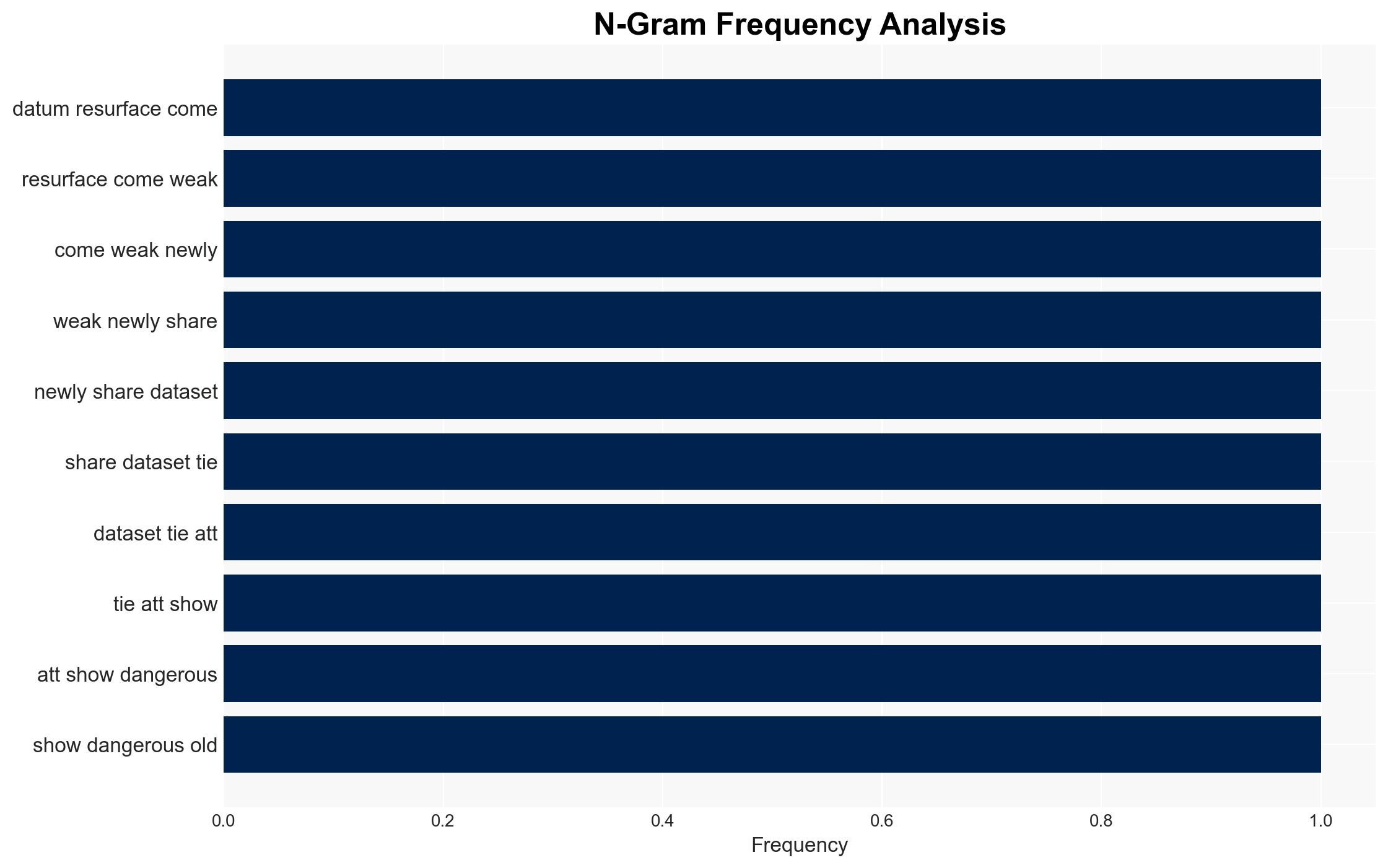
Intelligence Report: ATT breach data resurfaces with new risks for customers
1. BLUF (Bottom Line Up Front)
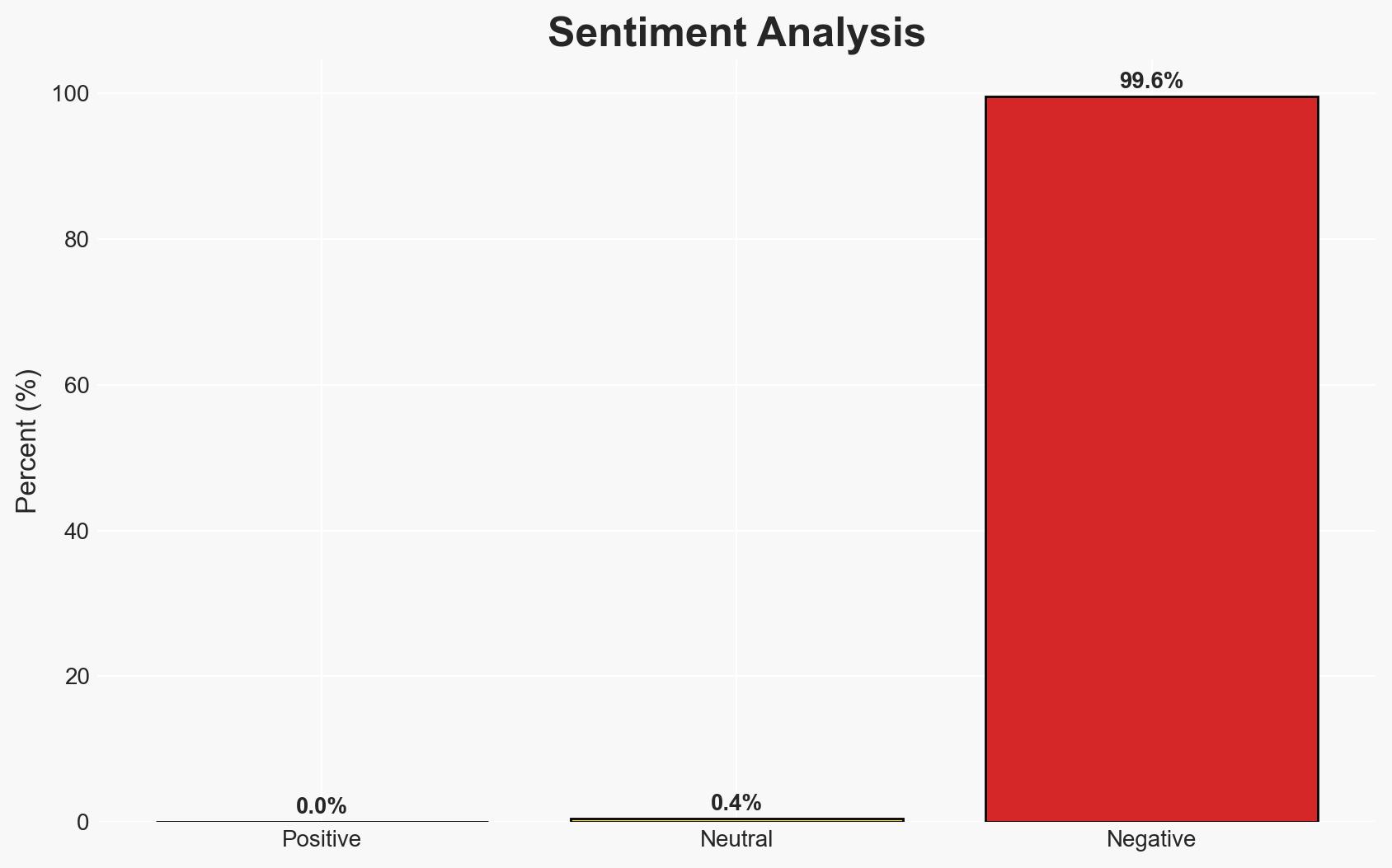
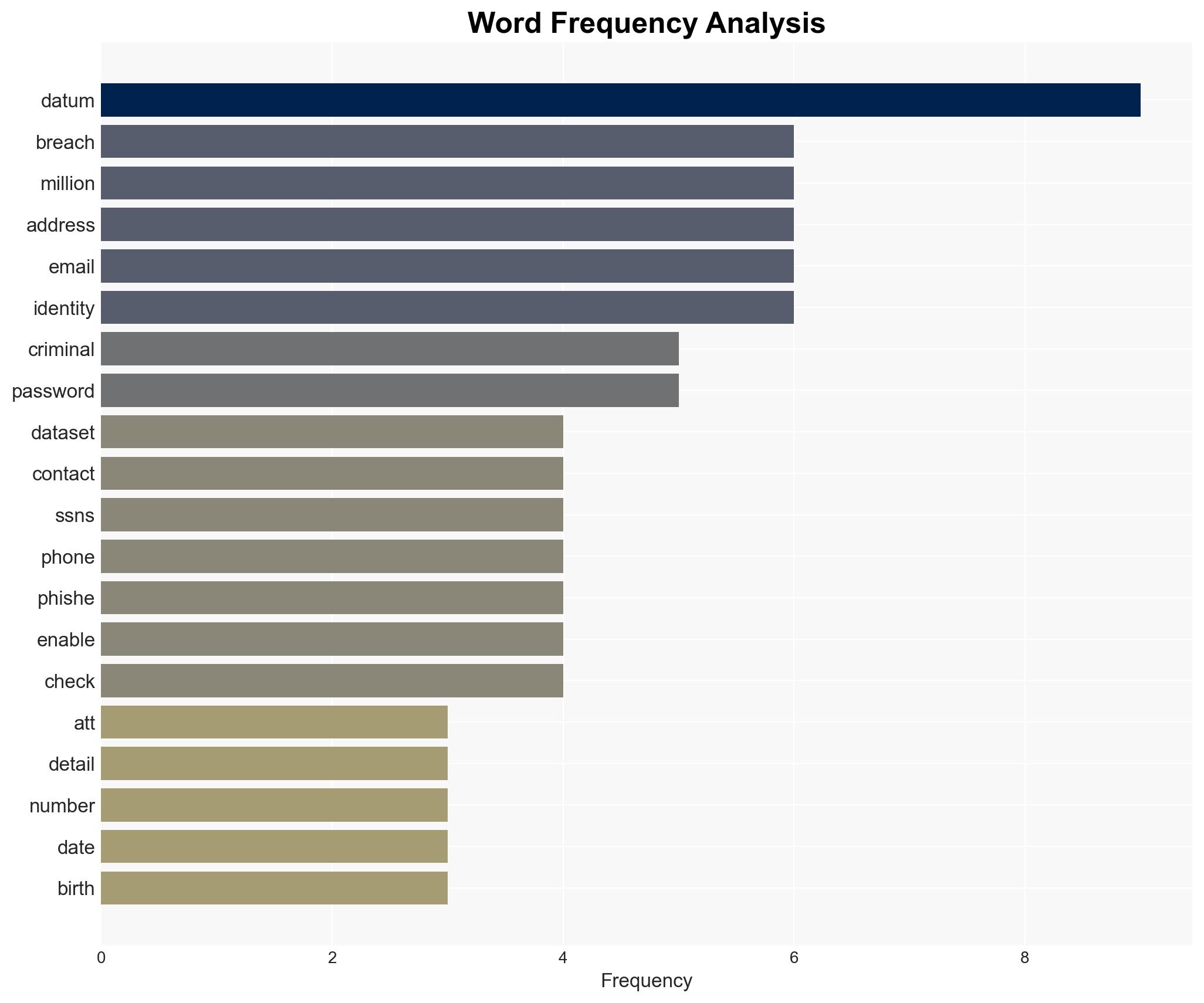
The resurfacing of a comprehensive dataset from a previous AT&T breach poses significant risks to former customers, as it contains sensitive personal information that can be exploited for identity theft and fraud. The dataset’s breadth and quality make it particularly attractive to cybercriminals. This situation requires immediate attention and mitigation efforts. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The dataset was compiled from multiple breaches over time, and its recent circulation is due to improvements in data aggregation techniques. Supporting evidence includes the dataset’s comprehensive nature and historical patterns of data accumulation. Uncertainties include the exact sources and timeline of data collection.
- Hypothesis B: The dataset is primarily the result of a recent, undisclosed breach of AT&T systems. This hypothesis is less supported due to the lack of evidence of a new breach and the historical tendency for old data to be re-circulated.
- Assessment: Hypothesis A is currently better supported due to the dataset’s extensive nature and the absence of indications of a new breach. Key indicators that could shift this judgment include discovery of a recent breach or confirmation of new data elements not previously compromised.
3. Key Assumptions and Red Flags
- Assumptions: The dataset is authentic and accurately represents AT&T customer information; cybercriminals will exploit the dataset for financial gain; AT&T’s security measures have not significantly improved since the data was initially compromised.
- Information Gaps: Details on the original breach sources and confirmation of whether new breaches have occurred; the extent of AT&T’s current security posture and response strategies.
- Bias & Deception Risks: Potential bias in assuming the dataset’s authenticity without independent verification; risk of underestimating AT&T’s current cybersecurity capabilities.
4. Implications and Strategic Risks
The circulation of this dataset could lead to increased identity theft and fraud incidents, impacting financial institutions and individuals. The situation may also affect AT&T’s reputation and customer trust.
- Political / Geopolitical: Minimal direct impact, but potential for increased regulatory scrutiny on data protection practices.
- Security / Counter-Terrorism: Elevated risk of cybercrime, but no direct counter-terrorism implications identified.
- Cyber / Information Space: Potential for increased phishing and social engineering attacks leveraging the dataset.
- Economic / Social: Potential financial losses for individuals and institutions; erosion of trust in digital services.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Encourage affected individuals to enable multi-factor authentication, monitor financial accounts, and report suspicious activities. AT&T should issue public guidance and enhance customer support for affected individuals.
- Medium-Term Posture (1–12 months): Develop partnerships with financial institutions to monitor fraud patterns; invest in cybersecurity infrastructure and public awareness campaigns.
- Scenario Outlook:
- Best: Rapid mitigation reduces fraud incidents, and AT&T regains customer trust.
- Worst: Widespread identity theft leads to significant financial and reputational damage.
- Most-Likely: Incremental increase in fraud cases with moderate impact on AT&T’s reputation.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data breach, identity theft, cybercrime, AT&T, personal data security, fraud prevention
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us