Attackers Abuse Virtual Private Servers to Compromise SaaS Accounts – Infosecurity Magazine
Published on: 2025-08-22
Intelligence Report: Attackers Abuse Virtual Private Servers to Compromise SaaS Accounts – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
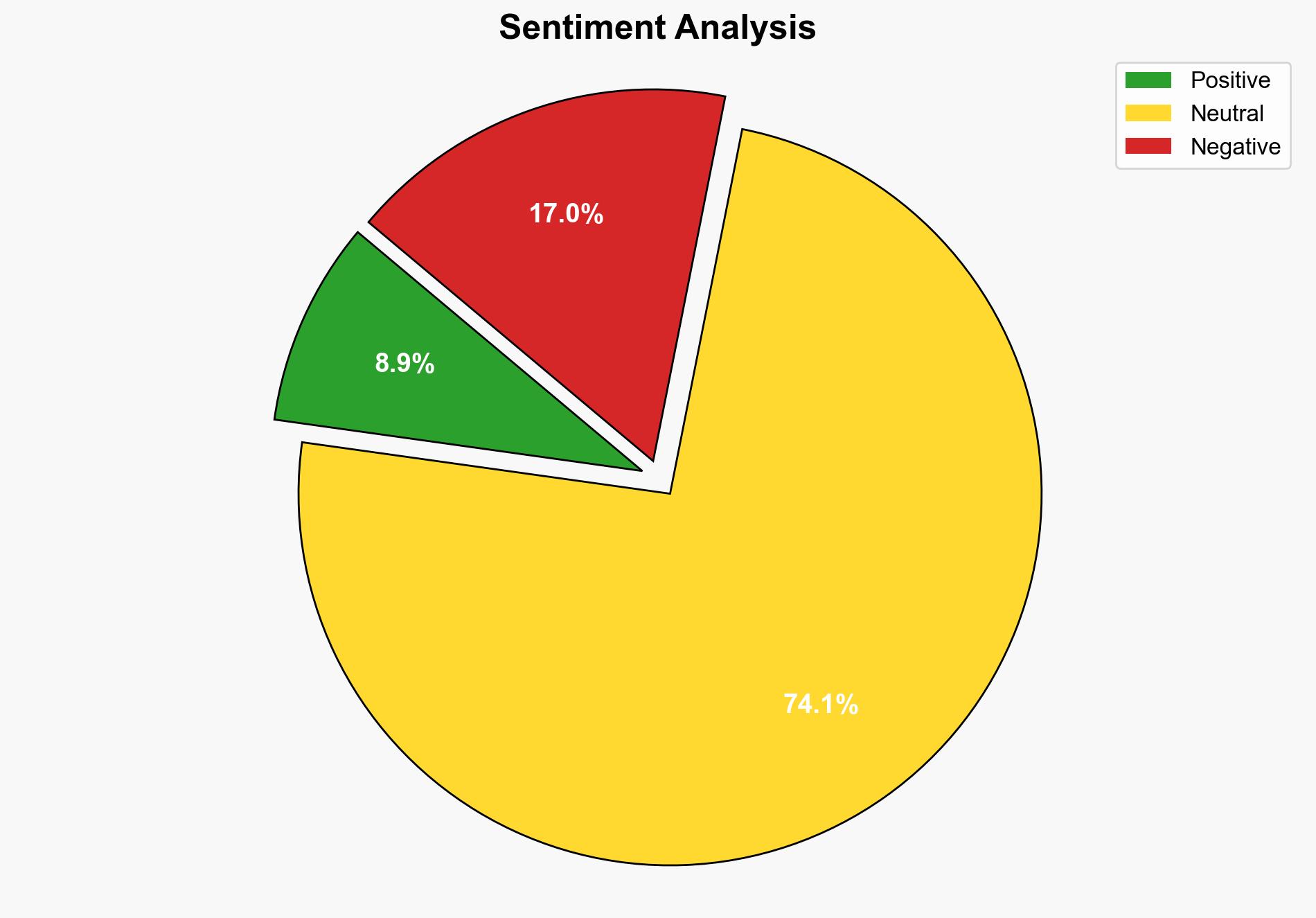
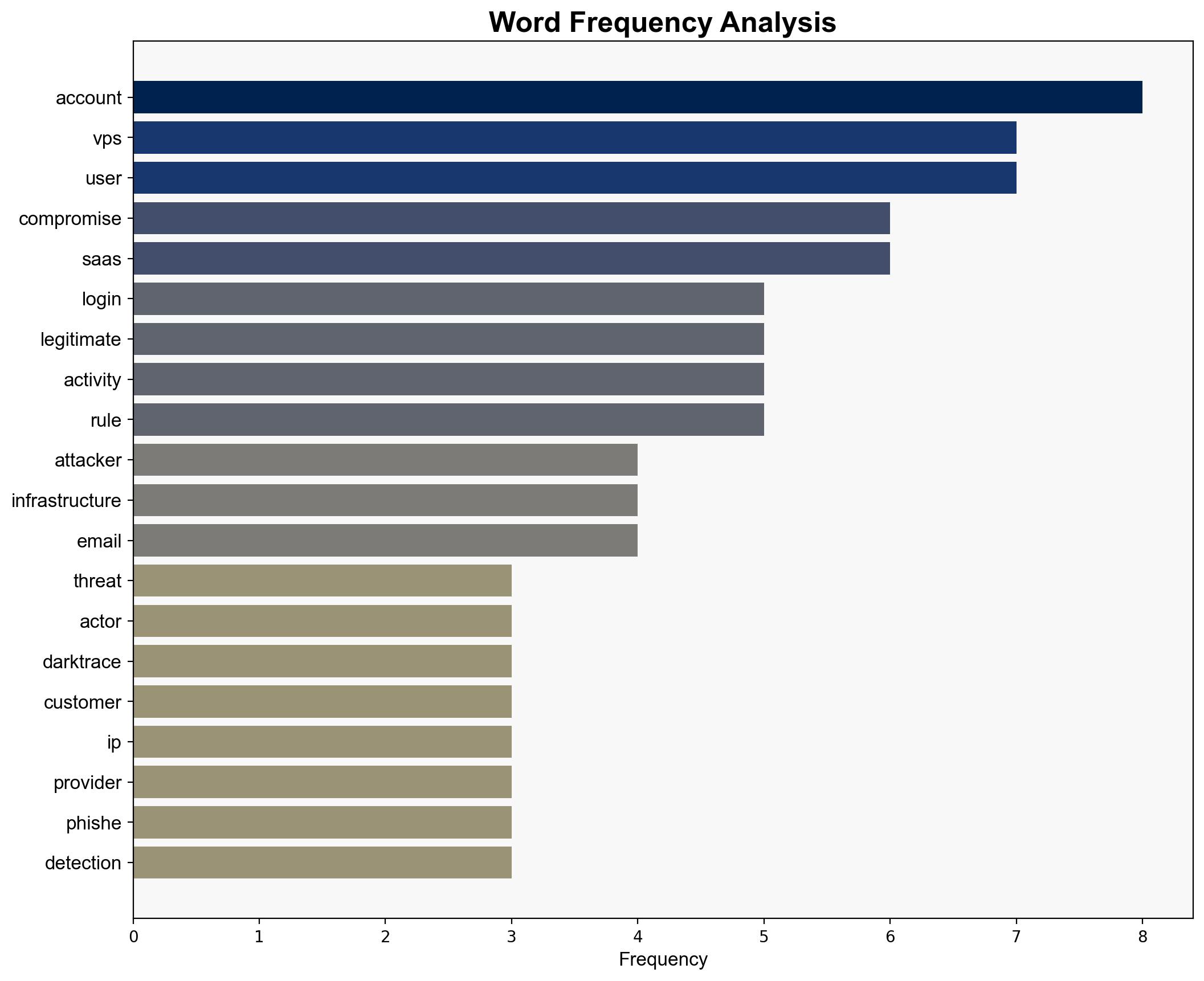
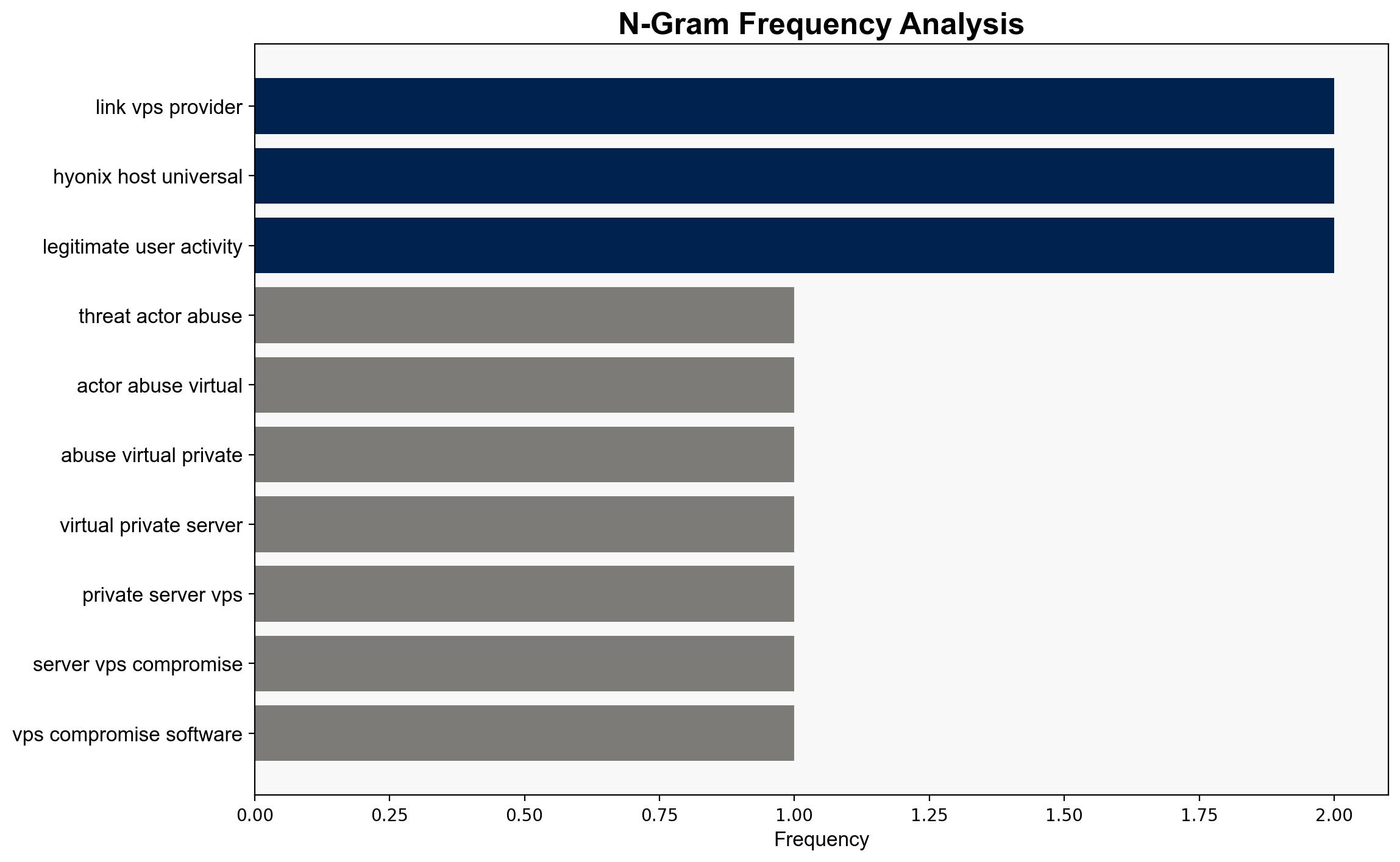
The most supported hypothesis is that threat actors are leveraging Virtual Private Servers (VPS) to conduct coordinated and persistent attacks on SaaS accounts, exploiting the anonymity and low-cost infrastructure provided by VPS providers like Hyonix and Host Universal. Confidence in this assessment is moderate due to the reliance on observed patterns and behaviors. Recommended actions include enhancing detection capabilities for anomalous login patterns and strengthening user education on phishing tactics.
2. Competing Hypotheses
Hypothesis 1: Threat actors are using VPS to mimic legitimate user activity and evade detection, allowing them to conduct targeted and persistent attacks on SaaS accounts.
Hypothesis 2: The observed activities are part of a broader, less coordinated cybercrime campaign exploiting VPS for opportunistic attacks rather than targeted campaigns.
Using Analysis of Competing Hypotheses (ACH 2.0), Hypothesis 1 is better supported due to the observed coordination in login patterns, use of similar inbox rules, and efforts to conceal phishing activities. Hypothesis 2 lacks specific indicators of broader opportunistic behavior.
3. Key Assumptions and Red Flags
Assumptions include the belief that VPS providers are unaware of the misuse of their services and that threat actors have sufficient technical capability to mimic legitimate user behavior. Red flags include the potential for VPS providers to be complicit or negligent, and the lack of direct attribution to specific threat groups. Missing data on the exact scale and scope of the attacks could indicate a blind spot.
4. Implications and Strategic Risks
The use of VPS for cyberattacks presents a significant risk to SaaS providers and their customers, potentially leading to data breaches, financial loss, and reputational damage. The persistent nature of these attacks could escalate into more sophisticated campaigns targeting critical infrastructure. Economically, the low cost of VPS services makes them an attractive option for threat actors, potentially increasing the frequency of such attacks.
5. Recommendations and Outlook
- Enhance monitoring and detection systems to identify and respond to anomalous login patterns and phishing attempts.
- Conduct regular security awareness training for users to recognize and report phishing attempts.
- Collaborate with VPS providers to develop mechanisms for detecting and mitigating misuse of their services.
- Scenario Projections:
- Best Case: Improved detection and collaboration with VPS providers significantly reduce the success rate of such attacks.
- Worst Case: Attackers adapt quickly, leading to more sophisticated and damaging campaigns.
- Most Likely: Continued attacks with moderate success, prompting incremental improvements in security measures.
6. Key Individuals and Entities
Entities involved include VPS providers Hyonix and Host Universal, and cybersecurity vendor Darktrace. No specific individuals are identified in the intelligence.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus