Attackers exploiting CVE-2025-59718 to bypass authentication on FortiGate firewalls and access configurations
Published on: 2025-12-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Attackers are exploiting auth bypass vulnerability on FortiGate firewalls CVE-2025-59718
1. BLUF (Bottom Line Up Front)
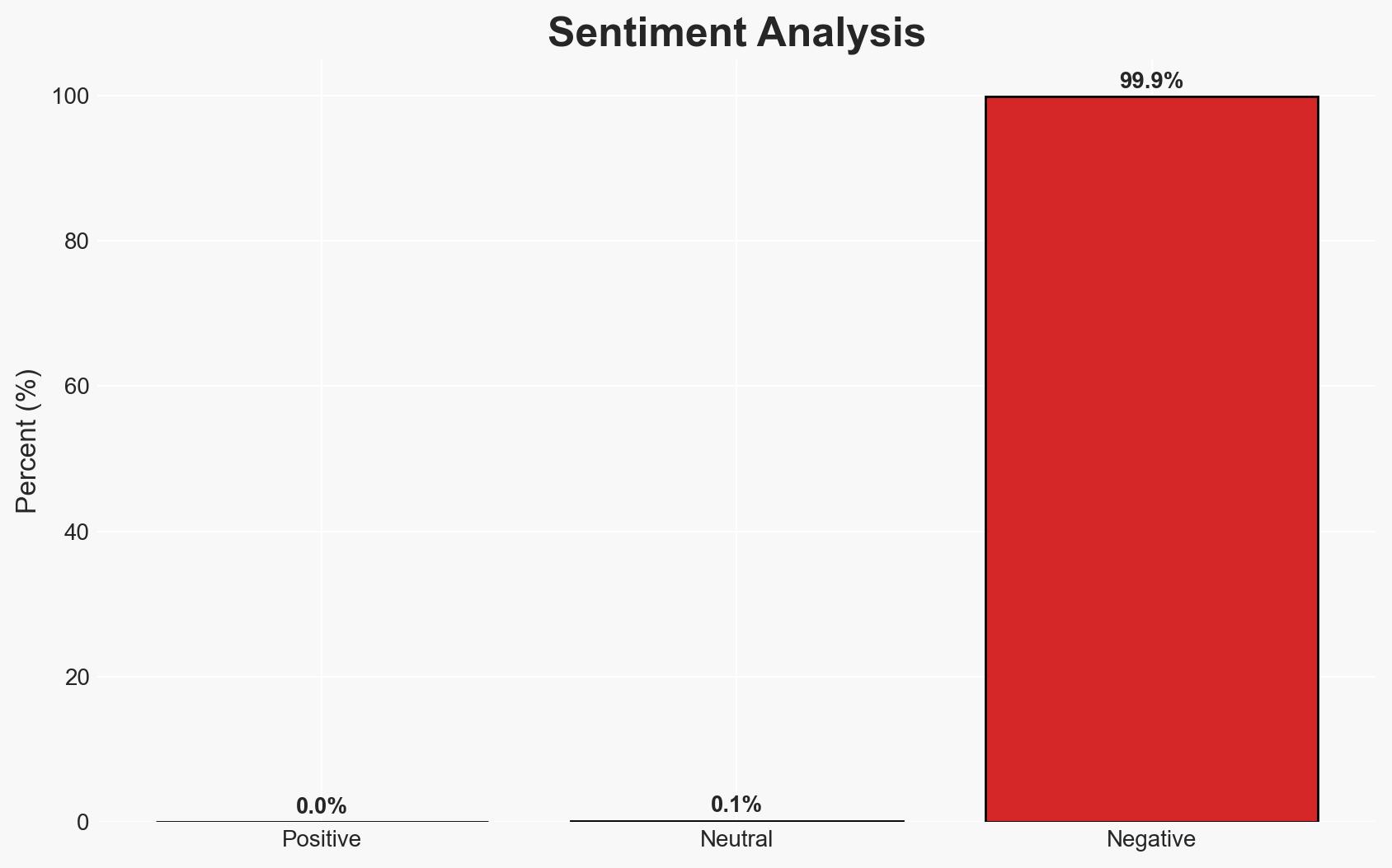
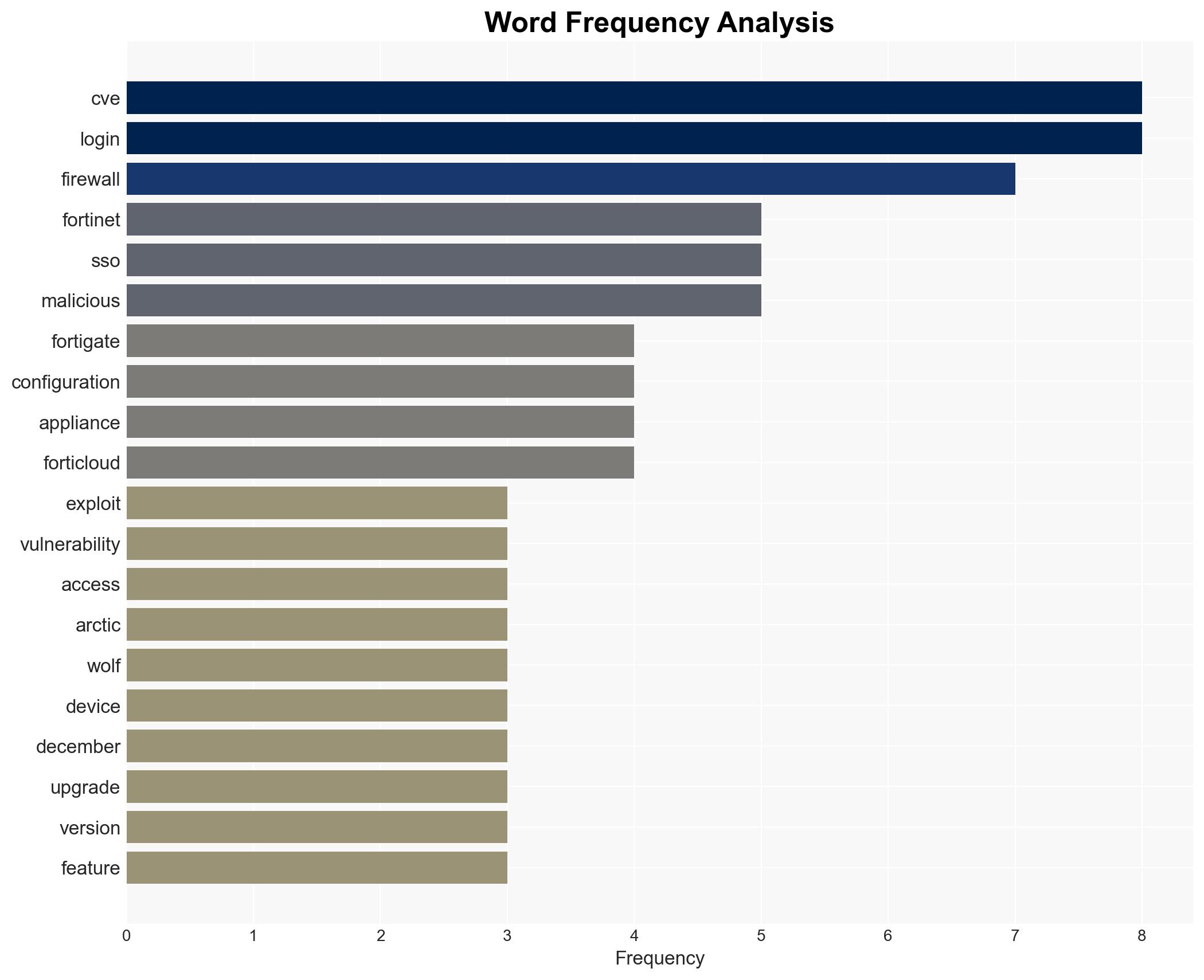
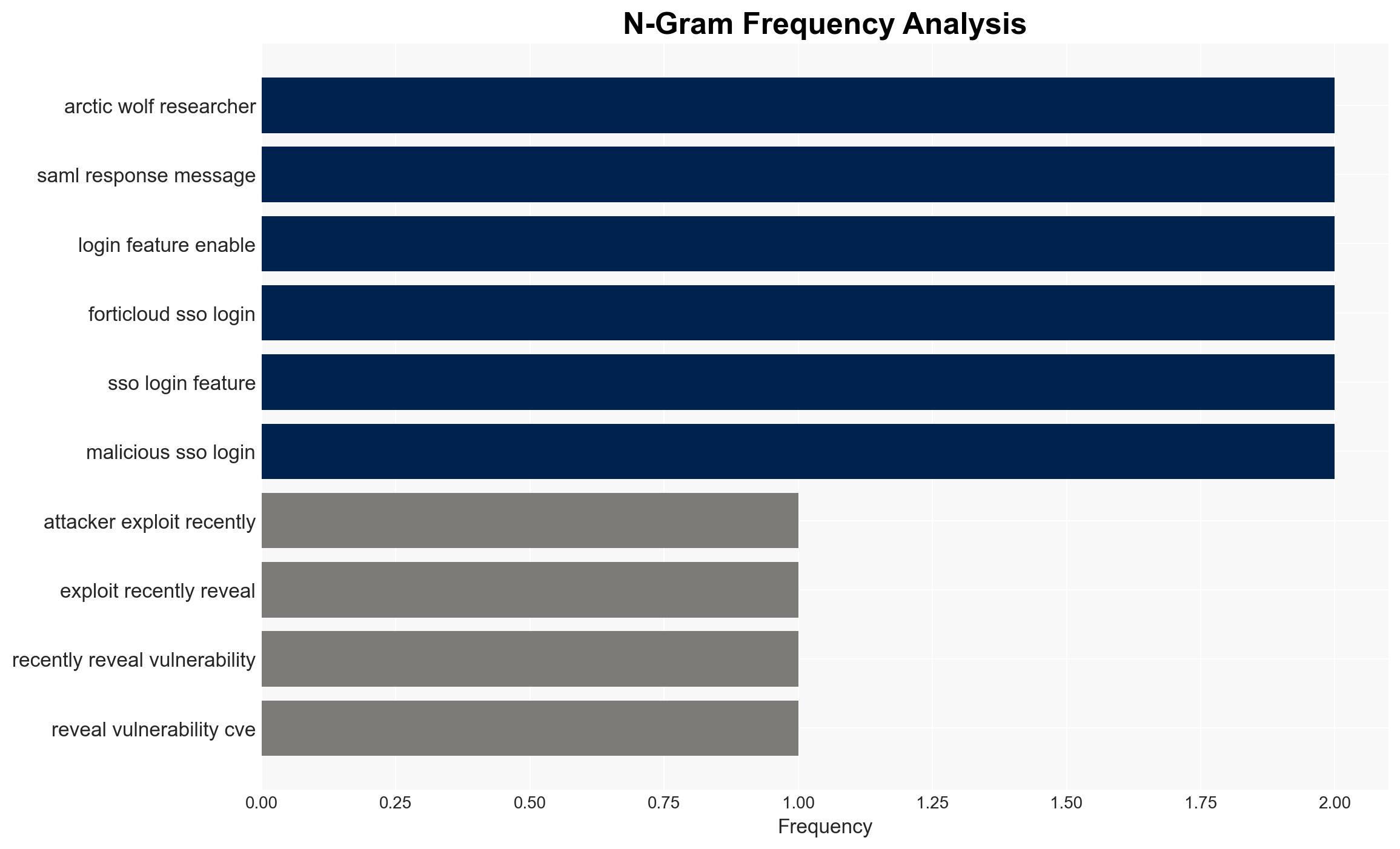
Attackers are actively exploiting a vulnerability (CVE-2025-59718) in Fortinet’s FortiGate firewalls, leading to unauthorized access and potential data exfiltration. Organizations using these firewalls are at risk, particularly if they have not applied the latest patches. The most likely hypothesis is that these attacks are opportunistic, targeting unpatched systems. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: The attacks are opportunistic, leveraging known vulnerabilities in unpatched systems to gain unauthorized access. This is supported by the timing of the attacks following the public disclosure of the vulnerability and the use of multiple IP addresses, suggesting a broad, non-targeted approach. Key uncertainty includes the specific motivations of the attackers.
- Hypothesis B: The attacks are targeted, possibly by a state-sponsored or organized cybercrime group, aiming to gather intelligence or cause disruption. This hypothesis is less supported due to the lack of specific targeting indicators and the use of a known vulnerability rather than a zero-day exploit.
- Assessment: Hypothesis A is currently better supported due to the pattern of widespread exploitation and the nature of the vulnerability. Indicators that could shift this judgment include evidence of targeted attacks against specific entities or the use of more sophisticated tactics.
3. Key Assumptions and Red Flags
- Assumptions: Organizations have not universally applied patches; attackers have access to the technical knowledge required to exploit the vulnerability; Fortinet’s advisories are accurate and comprehensive.
- Information Gaps: Specific identities and motivations of the attackers; the total number of affected organizations; the extent of data exfiltration.
- Bias & Deception Risks: Potential bias in reporting due to reliance on a single security firm’s analysis; risk of attackers using deception to mask their true intentions or origins.
4. Implications and Strategic Risks
This vulnerability exploitation could lead to increased cyber threats and potential data breaches, affecting organizational security and trust. Over time, this could result in more sophisticated attacks as adversaries refine their tactics.
- Political / Geopolitical: Potential for increased tensions if state actors are involved or perceived to be involved.
- Security / Counter-Terrorism: Heightened alert for cybersecurity teams; potential for increased demand for cybersecurity services and solutions.
- Cyber / Information Space: Possible increase in similar attacks exploiting other vulnerabilities; heightened awareness and scrutiny of Fortinet products.
- Economic / Social: Potential financial losses for affected organizations; erosion of trust in cybersecurity measures and products.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urgently apply patches to affected systems; monitor for indicators of compromise; restrict access to management interfaces.
- Medium-Term Posture (1–12 months): Enhance cybersecurity training and awareness; develop partnerships with cybersecurity firms for threat intelligence sharing; invest in more robust security infrastructure.
- Scenario Outlook:
- Best: Rapid patching and mitigation reduce attack success rates, restoring confidence.
- Worst: Continued exploitation leads to significant data breaches and financial losses.
- Most-Likely: Ongoing attacks prompt increased cybersecurity measures and awareness, with gradual reduction in successful exploits.
6. Key Individuals and Entities
- Fortinet (vendor of affected products)
- Arctic Wolf (security research firm)
- Not clearly identifiable from open sources in this snippet (attackers)
7. Thematic Tags
cybersecurity, vulnerability exploitation, Fortinet, network security, data exfiltration, cyber threat, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us