Attackers phish OAuth codes take over Microsoft 365 accounts – Help Net Security
Published on: 2025-04-23
Intelligence Report: Attackers phish OAuth codes take over Microsoft 365 accounts – Help Net Security
1. BLUF (Bottom Line Up Front)
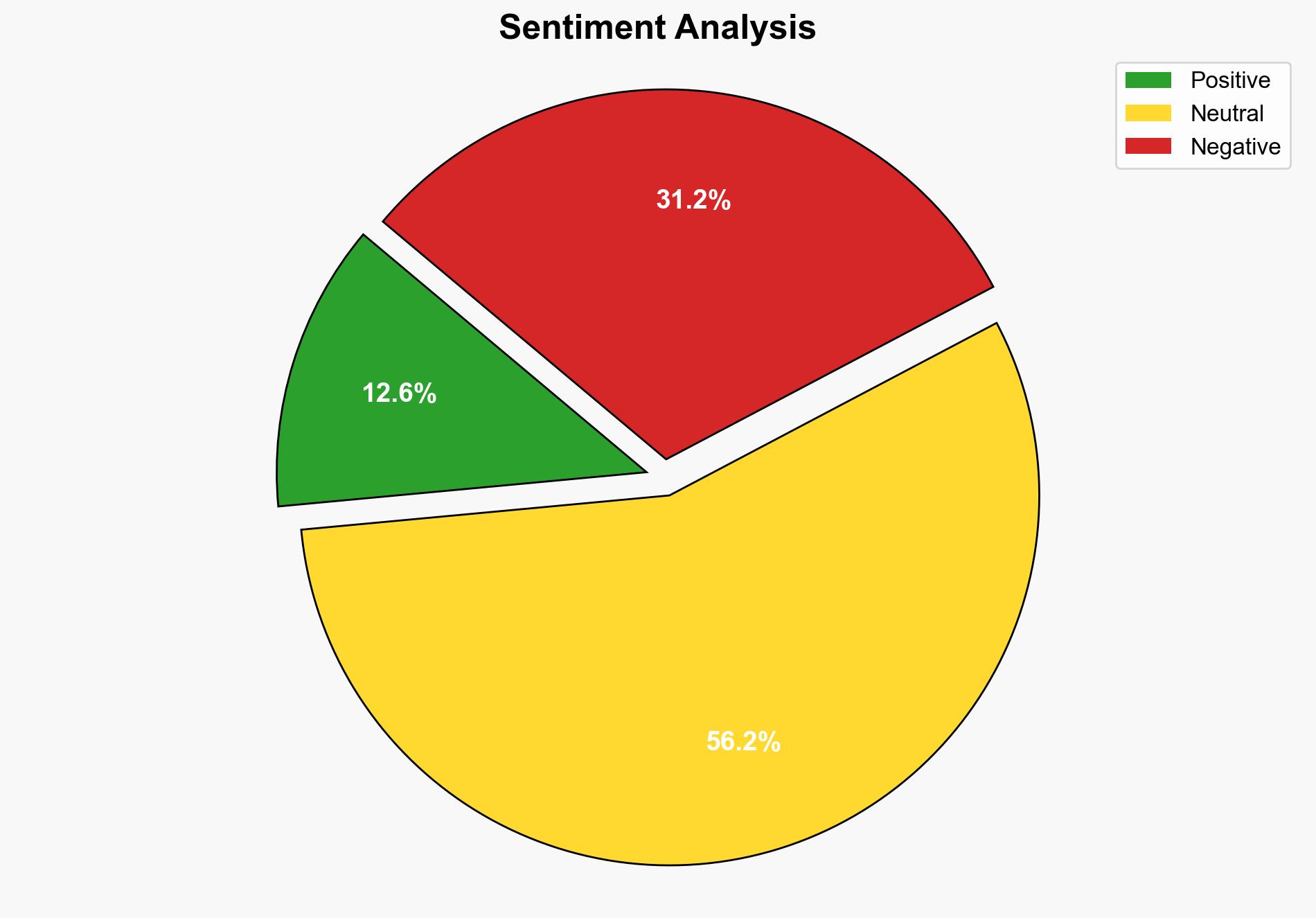
Recent phishing attacks targeting Microsoft 365 accounts have been linked to suspected Russian threat actors. These attacks exploit OAuth codes to gain unauthorized access to accounts, posing significant risks to organizations, particularly those involved in human rights and humanitarian efforts. Immediate enhancements in cybersecurity measures are recommended to mitigate these threats.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Analysis of Competing Hypotheses (ACH)
The primary hypothesis is that the phishing attacks are conducted by a Russian threat actor group, leveraging OAuth-based phishing tactics. Alternative hypotheses, such as independent cybercriminal activity, were considered but found less consistent with the observed patterns and targets.
SWOT Analysis
Strengths: Use of official Microsoft infrastructure increases attack credibility.
Weaknesses: Reliance on user interaction for success.
Opportunities: Increased awareness and training can reduce susceptibility.
Threats: Potential for widespread data breaches and unauthorized access to sensitive information.
Indicators Development
Key indicators include unusual OAuth consent requests, phishing emails mimicking official communications, and unexpected account access from new devices or locations.
3. Implications and Strategic Risks
The attack patterns suggest a strategic focus on organizations with geopolitical significance, such as those involved in the Ukraine conflict. The use of OAuth phishing indicates a sophisticated approach that could evolve, increasing the risk of data breaches and espionage activities. This could lead to broader geopolitical tensions and undermine trust in digital communications.
4. Recommendations and Outlook
- Enhance user training on recognizing phishing attempts and OAuth consent requests.
- Implement multi-factor authentication and restrict third-party application access.
- Monitor for unusual account activity and OAuth consent grants.
- Scenario Projections:
- Best Case: Increased awareness leads to a significant reduction in successful phishing attempts.
- Worst Case: Continued attacks result in major data breaches and geopolitical fallout.
- Most Likely: Ongoing attempts with moderate success, prompting gradual improvements in cybersecurity defenses.
5. Key Individuals and Entities
No specific individuals are named in the available data. The threat actor group is suspected to have ties to Russian entities.
6. Thematic Tags
(‘national security threats, cybersecurity, counter-terrorism, regional focus’, ‘cybersecurity’, ‘counter-terrorism’, ‘regional focus’)