Australian chief at US defence contractor L3Harris sold exploits to Russia – iTnews
Published on: 2025-10-30
Intelligence Report: Australian chief at US defence contractor L3Harris sold exploits to Russia – iTnews
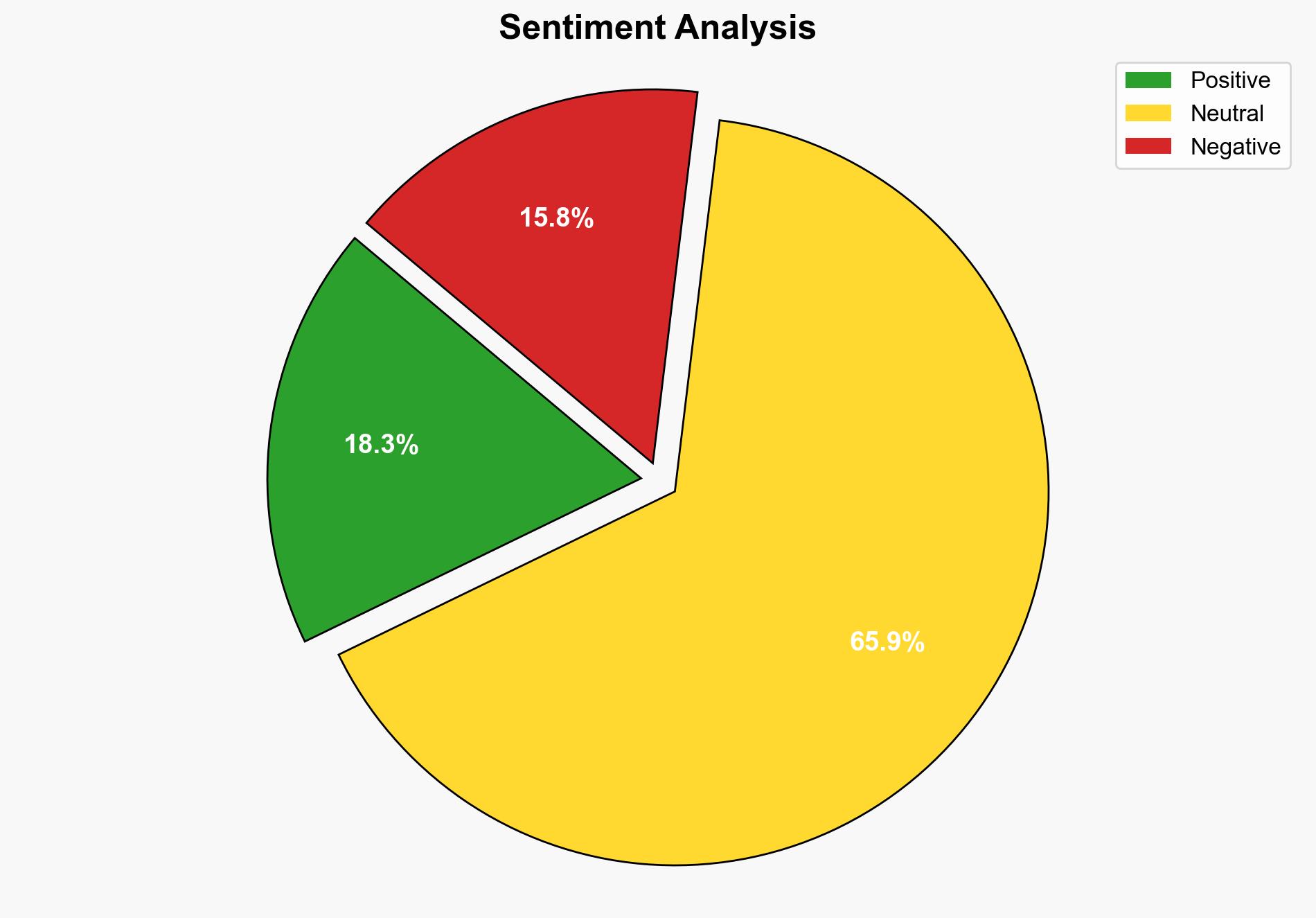
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that Peter Williams, motivated by financial gain, deliberately sold sensitive cyber exploits to Russian entities, posing a significant national security threat. Confidence in this assessment is high based on the evidence of financial transactions and Williams’ admission of guilt. Recommended actions include enhancing internal security protocols at defense contractors and increasing collaboration with international partners to monitor and mitigate similar threats.
2. Competing Hypotheses
Hypothesis 1: Peter Williams intentionally sold cyber exploits to Russian brokers for personal financial gain, fully aware of the implications for national security.
Hypothesis 2: Williams was coerced or manipulated into selling the exploits, possibly under duress or through deceptive means, without fully understanding the end-use or implications.
Using Analysis of Competing Hypotheses (ACH 2.0), Hypothesis 1 is better supported due to Williams’ guilty plea, the documented financial transactions, and the absence of evidence suggesting coercion or manipulation.
3. Key Assumptions and Red Flags
Assumptions include the belief that Williams acted independently and that the financial transactions were solely for personal gain. A red flag is the lack of detailed information on how Williams accessed and extracted the exploits, indicating potential security lapses within L3Harris. Additionally, there is no evidence of coercion, which could be a blind spot.
4. Implications and Strategic Risks
The sale of cyber exploits to Russia could enhance their cyber warfare capabilities, posing a threat to the Five Eyes alliance. This incident highlights vulnerabilities in contractor security protocols and the potential for insider threats. It could lead to increased scrutiny and regulatory measures on defense contractors, impacting operational efficiency and international collaborations.
5. Recommendations and Outlook
- Implement stricter vetting and monitoring processes for employees with access to sensitive information.
- Enhance cybersecurity measures and conduct regular audits to detect and prevent insider threats.
- Foster international cooperation to track and counteract the dissemination of cyber exploits.
- Best Case: Strengthened security measures prevent future breaches, maintaining alliance integrity.
- Worst Case: Further breaches occur, leading to significant geopolitical tensions and weakened defense capabilities.
- Most Likely: Increased regulatory oversight and improved security protocols mitigate immediate risks but require ongoing vigilance.
6. Key Individuals and Entities
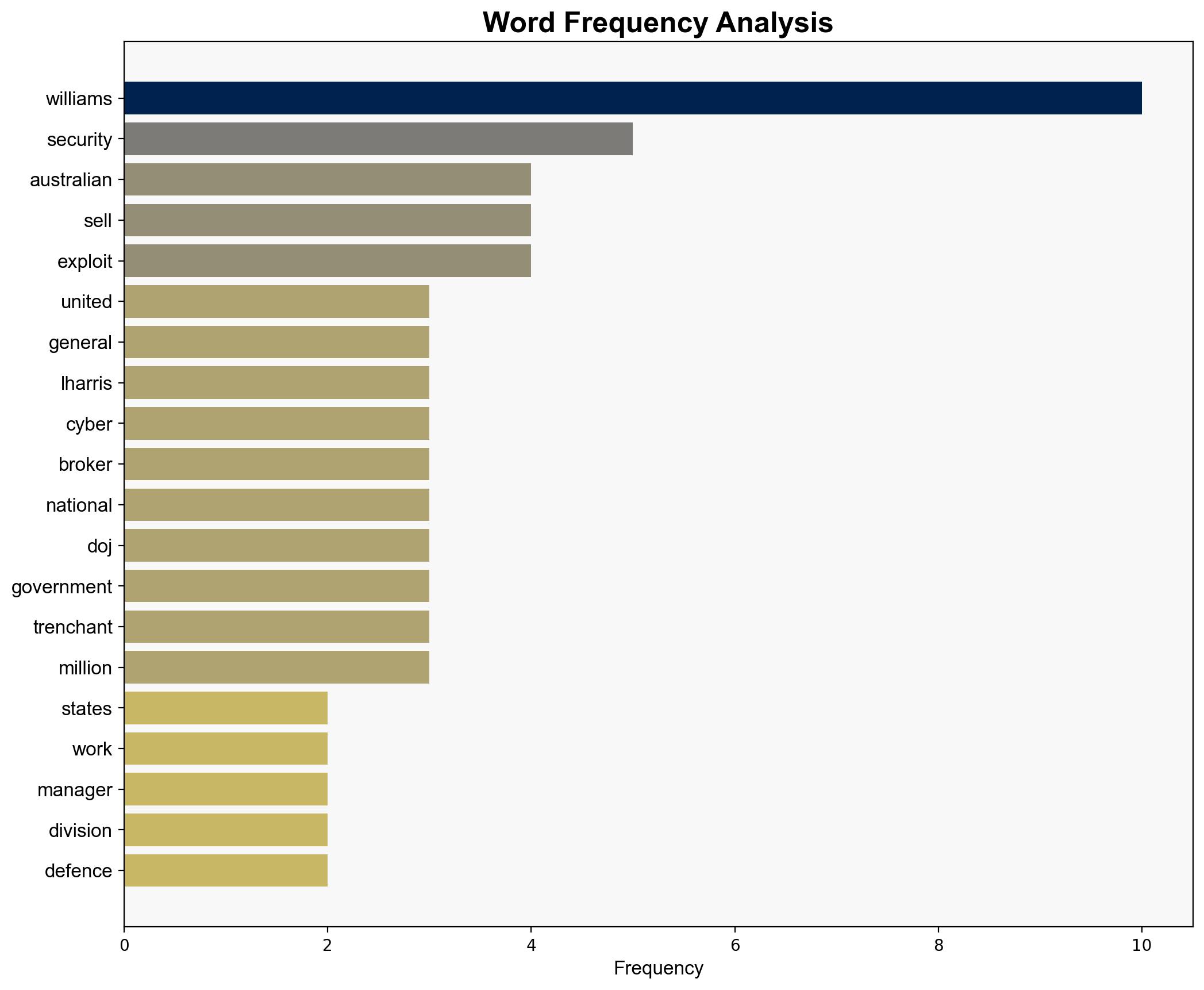
Peter Williams, L3Harris, Azimuth Security, Linchpin Labs, Australian Signals Directorate, Department of Justice, Russian government entities.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus