Authenticated RCE Vulnerabilities Identified in Netgate pfSense CE Versions 272 and 280
Published on: 2026-02-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Full Disclosure CVE-2025-69690 CVE-2025-69691 Authenticated RCE in Netgate pfSense CE 272 and 280
1. BLUF (Bottom Line Up Front)
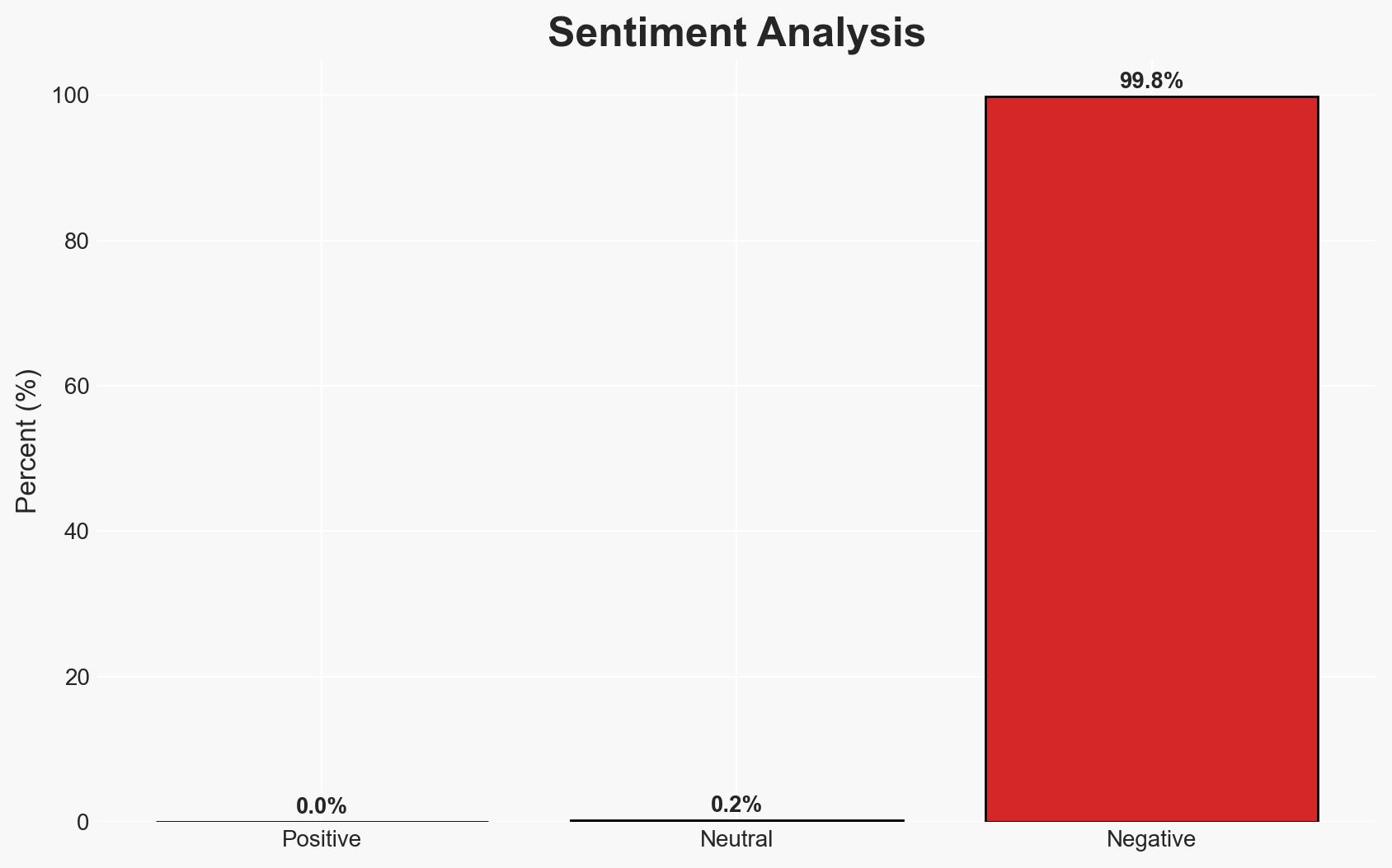
The disclosure of CVE-2025-69690 and CVE-2025-69691 presents significant security vulnerabilities in Netgate pfSense Community Edition, allowing authenticated remote code execution. These vulnerabilities could lead to complete firewall takeover by malicious actors with administrative access. The vendor’s decision not to patch these issues increases the risk of exploitation. Overall confidence in this assessment is moderate due to the lack of vendor response and potential for exploitation.
2. Competing Hypotheses
- Hypothesis A: The vulnerabilities are a result of oversight in security design, and the vendor’s classification as “expected behavior” for administrators reflects a misunderstanding of the threat landscape. This is supported by the high CVSS scores and the potential for severe impact.
- Hypothesis B: The vendor’s response indicates a strategic decision to prioritize other security issues or resource constraints, viewing the vulnerabilities as low risk due to the requirement for authenticated access. This is contradicted by the critical nature of the vulnerabilities and the potential for exploitation.
- Assessment: Hypothesis A is currently better supported due to the high severity ratings and the potential for significant impact, which outweigh the vendor’s rationale. Indicators that could shift this judgment include a change in vendor response or evidence of widespread exploitation.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerabilities are exploitable by any authenticated administrator; the vendor’s response reflects their final stance; no patches will be issued in the near term.
- Information Gaps: Details on the vendor’s internal risk assessment process; potential exploitation attempts or incidents in the wild.
- Bias & Deception Risks: Potential bias in the vendor’s classification of the vulnerabilities; lack of transparency in vendor communications could indicate downplaying of risks.
4. Implications and Strategic Risks
The existence of these vulnerabilities without a vendor patch could lead to increased exploitation attempts, particularly targeting organizations with less stringent access controls. This situation might evolve to affect broader cybersecurity dynamics if left unaddressed.
- Political / Geopolitical: Potential for state-sponsored actors to exploit these vulnerabilities for intelligence gathering or disruptive operations.
- Security / Counter-Terrorism: Increased risk of targeted attacks on critical infrastructure using these vulnerabilities.
- Cyber / Information Space: Likely rise in exploit kits or automated tools leveraging these vulnerabilities, increasing the attack surface.
- Economic / Social: Potential financial losses for affected organizations due to data breaches or service disruptions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Organizations using pfSense should implement strict access controls, monitor for suspicious activity, and consider compensating controls such as network segmentation.
- Medium-Term Posture (1–12 months): Encourage vendor engagement to reassess the vulnerabilities, and develop alternative security measures or seek third-party patches.
- Scenario Outlook:
- Best: Vendor issues patches, reducing risk of exploitation.
- Worst: Widespread exploitation leading to significant breaches and operational disruptions.
- Most-Likely: Continued risk with sporadic exploitation attempts, primarily targeting less secure environments.
6. Key Individuals and Entities
- Nelson Adhepeau (Researcher)
- Netgate (Vendor)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, remote code execution, vulnerability management, network security, pfSense, authenticated access, vendor response
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us