Avoid Engaging with Scattered Lapsus ShinyHunters to Prevent Escalating Harassment and Extortion Tactics
Published on: 2026-02-02
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Please Dont Feed the Scattered Lapsus Shiny Hunters
1. BLUF (Bottom Line Up Front)
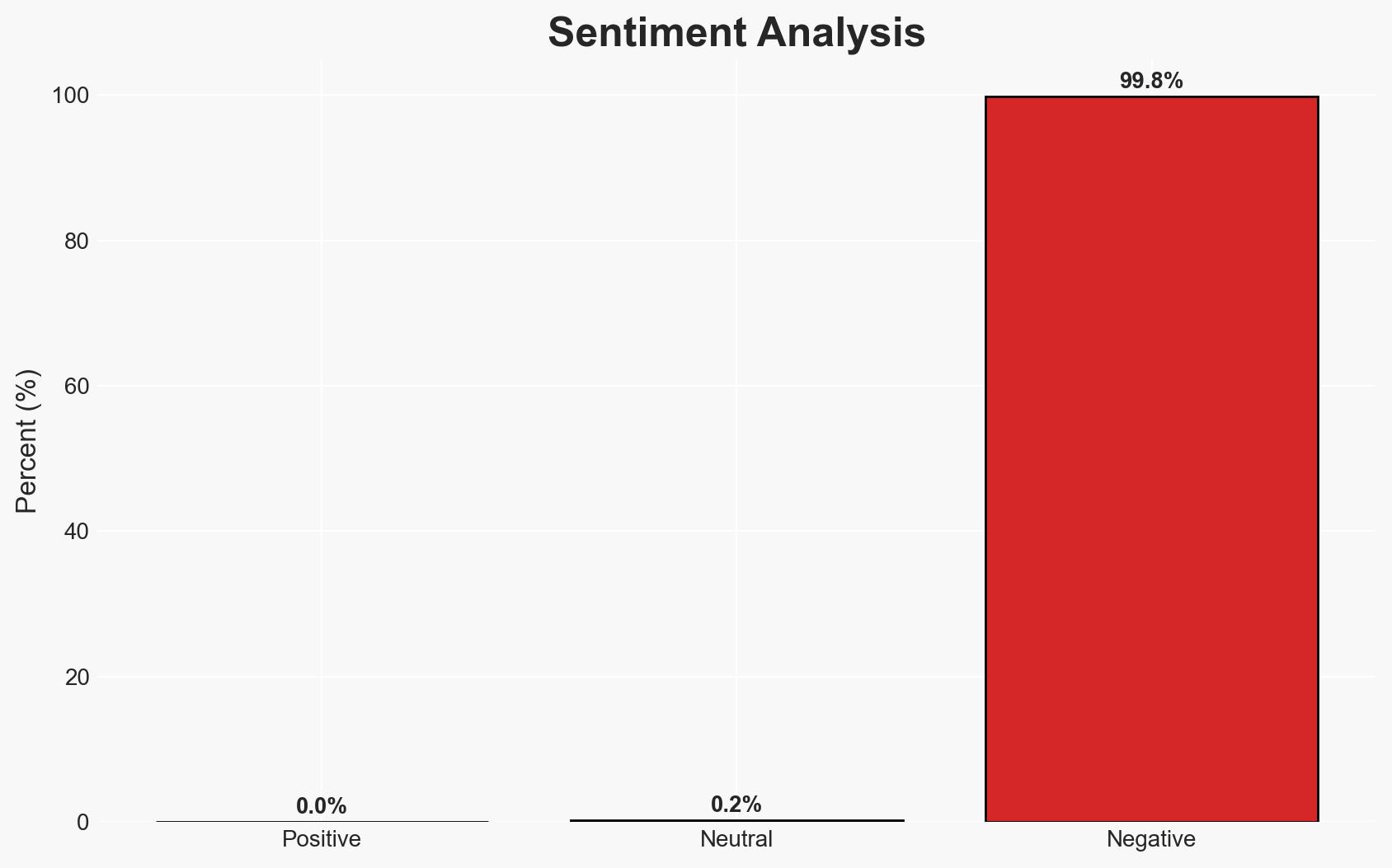
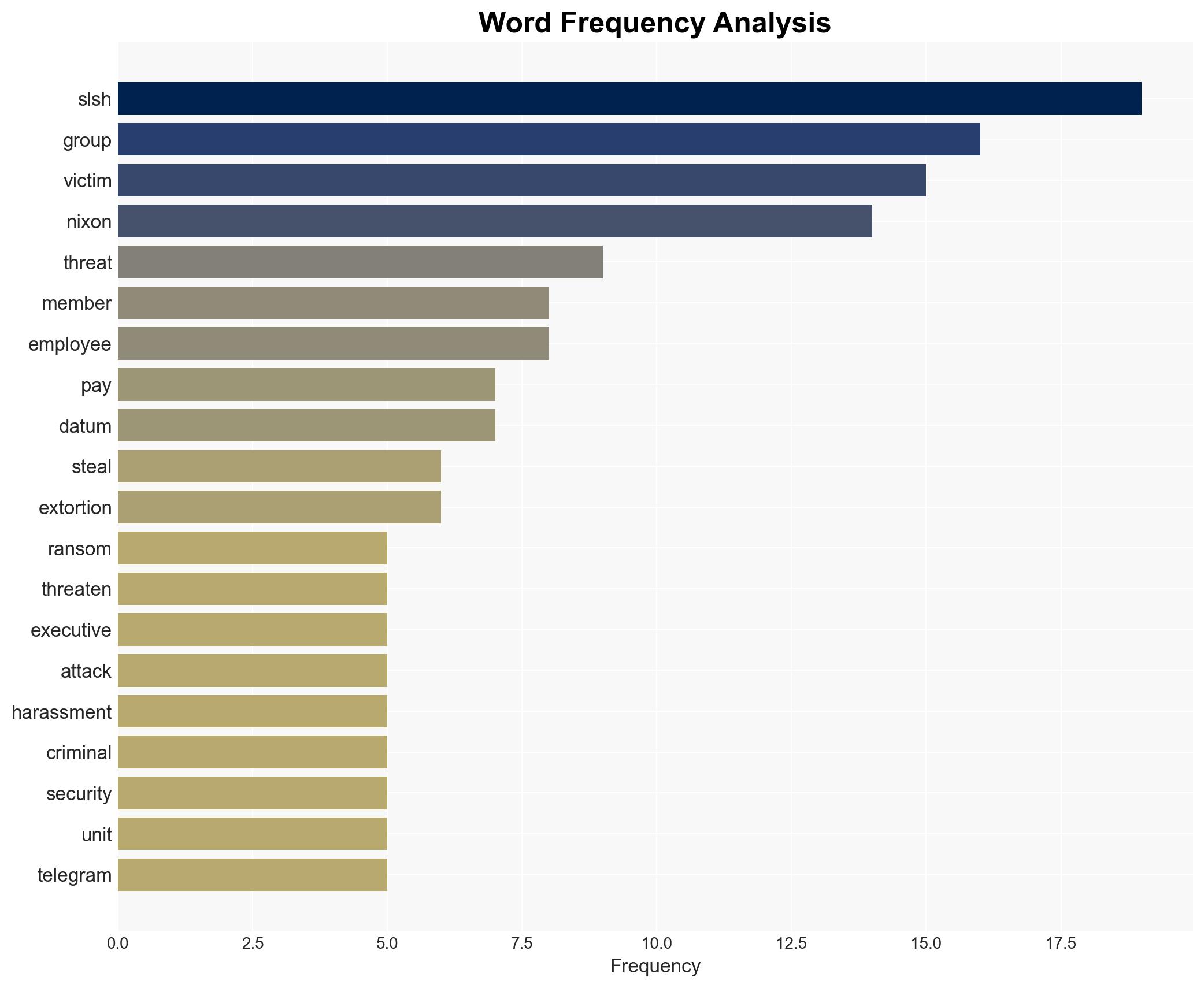
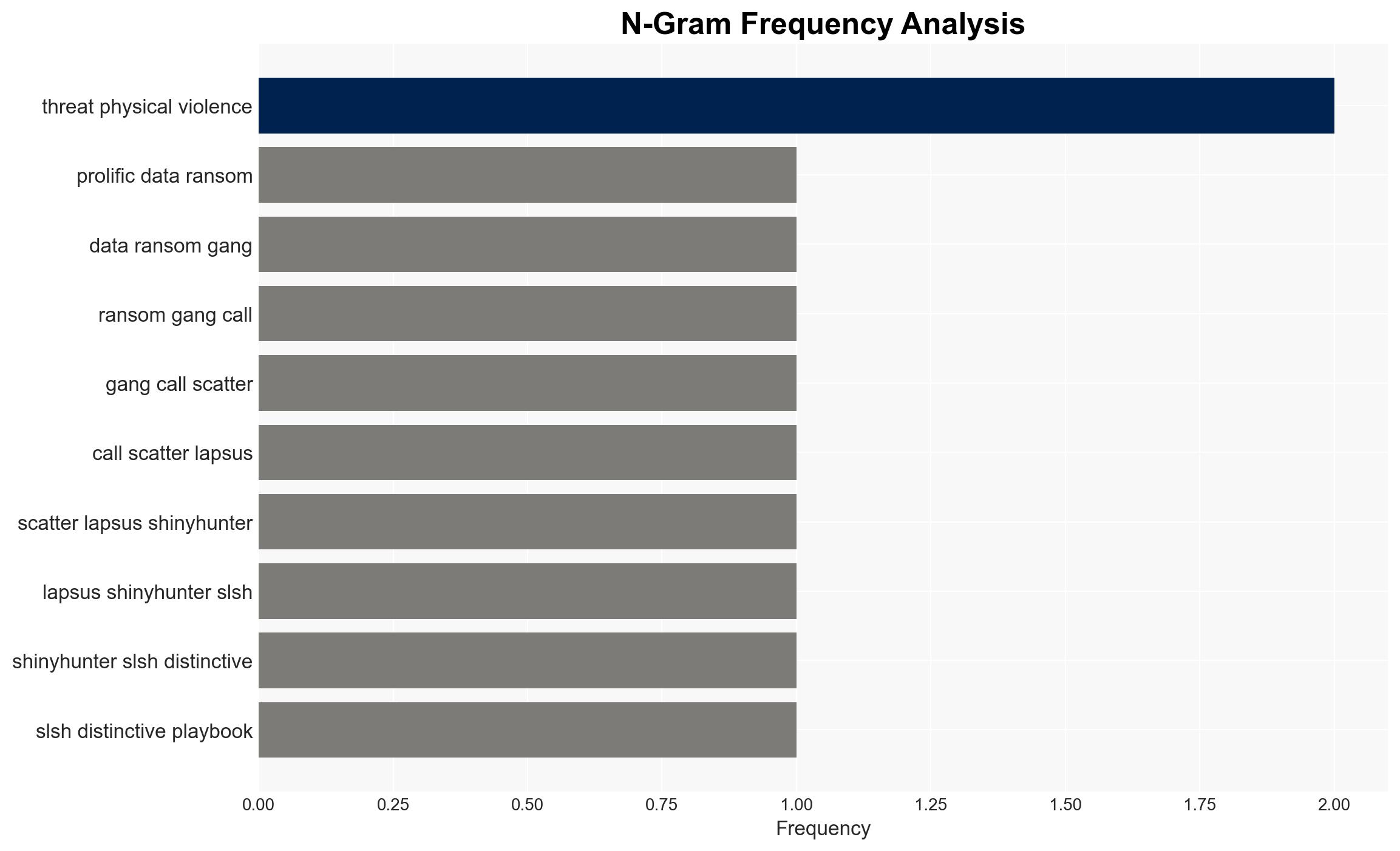
The Scattered Lapsus ShinyHunters (SLSH) group poses a significant threat through its aggressive and unpredictable extortion tactics, affecting corporate executives and their families. The group’s lack of a consistent operational pattern complicates mitigation efforts. The most likely hypothesis is that SLSH will continue its high-pressure tactics without honoring any agreements, with moderate confidence in this assessment.
2. Competing Hypotheses
- Hypothesis A: SLSH will maintain its current strategy of aggressive harassment and extortion, showing no interest in building a reputation for reliability. This is supported by their history of fractious behavior and lack of consistent operations. However, the group’s fluidity introduces uncertainty regarding their future actions.
- Hypothesis B: SLSH may evolve towards a more structured and predictable model similar to traditional ransomware groups, potentially to increase their financial gain. This is contradicted by their current operational style and lack of interest in maintaining a trustworthy reputation.
- Assessment: Hypothesis A is currently better supported due to consistent reports of SLSH’s unpredictable and aggressive tactics. Indicators such as a shift towards more organized operations or a change in leadership could alter this judgment.
3. Key Assumptions and Red Flags
- Assumptions: SLSH will continue to operate without a coherent strategy; victims will remain vulnerable to harassment; current intelligence accurately reflects SLSH’s operational methods; SLSH lacks centralized leadership.
- Information Gaps: Detailed organizational structure of SLSH; motivations behind their operational choices; potential links to other criminal groups.
- Bias & Deception Risks: Potential bias in reporting due to reliance on victim accounts; risk of underestimating SLSH’s adaptability or strategic shifts.
4. Implications and Strategic Risks
The continuation of SLSH’s tactics could lead to increased corporate security spending and a potential rise in public fear regarding personal safety. Over time, this could influence regulatory frameworks and corporate policies on cyber extortion.
- Political / Geopolitical: Potential for increased international cooperation on cybercrime legislation and enforcement.
- Security / Counter-Terrorism: Heightened security measures for executives and potential for increased law enforcement involvement.
- Cyber / Information Space: Increased focus on phishing and social engineering defenses; potential for more sophisticated cyber defense technologies.
- Economic / Social: Financial strain on companies due to extortion payments and security investments; potential public relations challenges.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of SLSH’s communication channels; develop rapid response protocols for executive protection; increase employee training on phishing awareness.
- Medium-Term Posture (1–12 months): Strengthen partnerships with cybersecurity firms; invest in advanced threat detection systems; engage in public-private information sharing initiatives.
- Scenario Outlook:
- Best Case: SLSH disbands or significantly reduces activity, possibly due to internal conflict or law enforcement action.
- Worst Case: SLSH escalates to more severe forms of harassment or partners with more organized groups, increasing their threat level.
- Most-Likely: SLSH continues current operations with sporadic changes in tactics, maintaining pressure on targeted companies.
6. Key Individuals and Entities
- Scattered Lapsus ShinyHunters (SLSH)
- Allison Nixon, Director of Research, Unit 221B
- Google’s security forensics firm Mandiant
7. Thematic Tags
cybersecurity, cyber extortion, ransomware, cybercrime, corporate security, phishing attacks, information security, threat intelligence
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us