Backdoors Installed Passwords Stolen Who Is The ToyMaker – Forbes
Published on: 2025-04-28
Intelligence Report: Backdoors Installed Passwords Stolen Who Is The ToyMaker – Forbes
1. BLUF (Bottom Line Up Front)
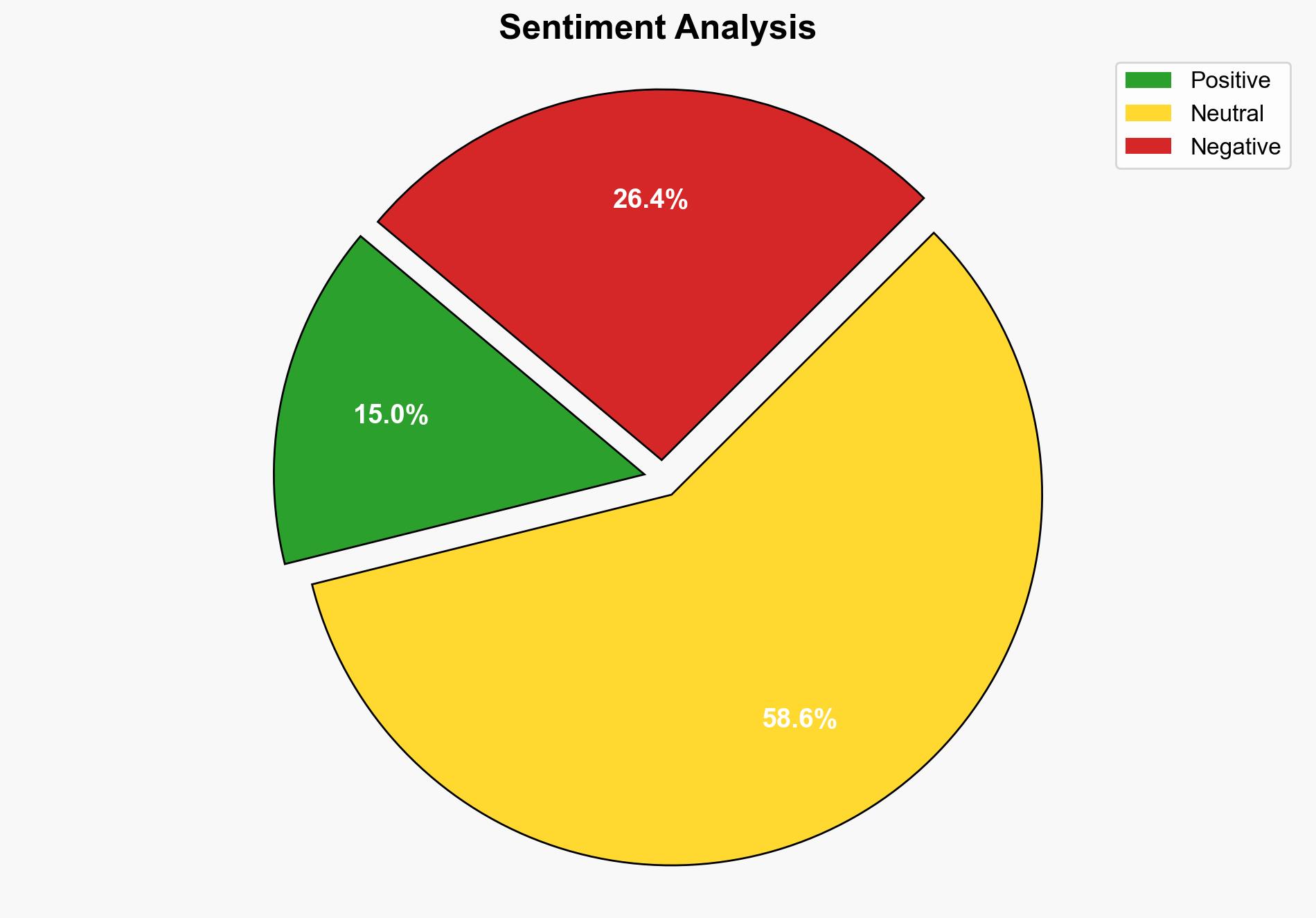
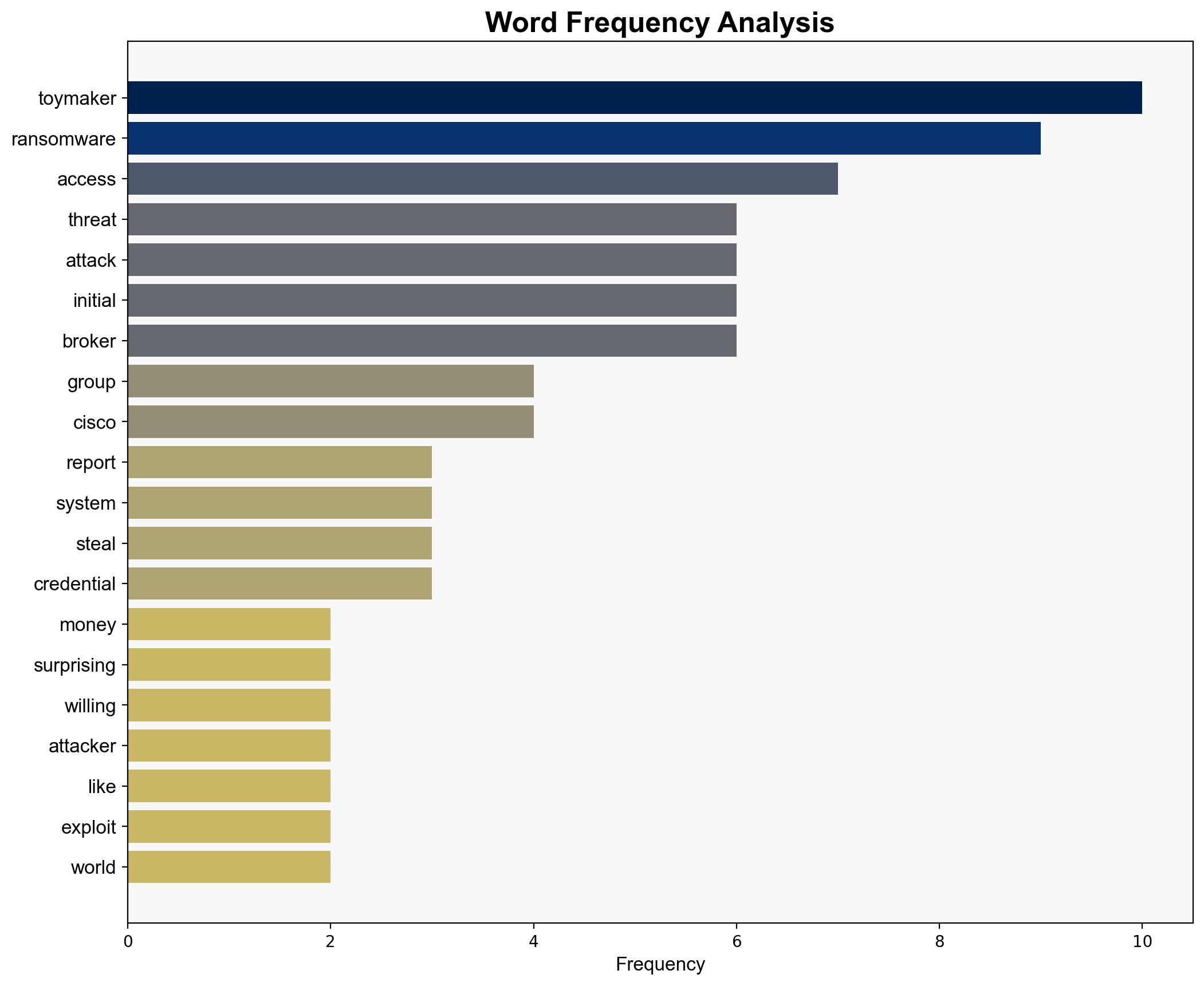
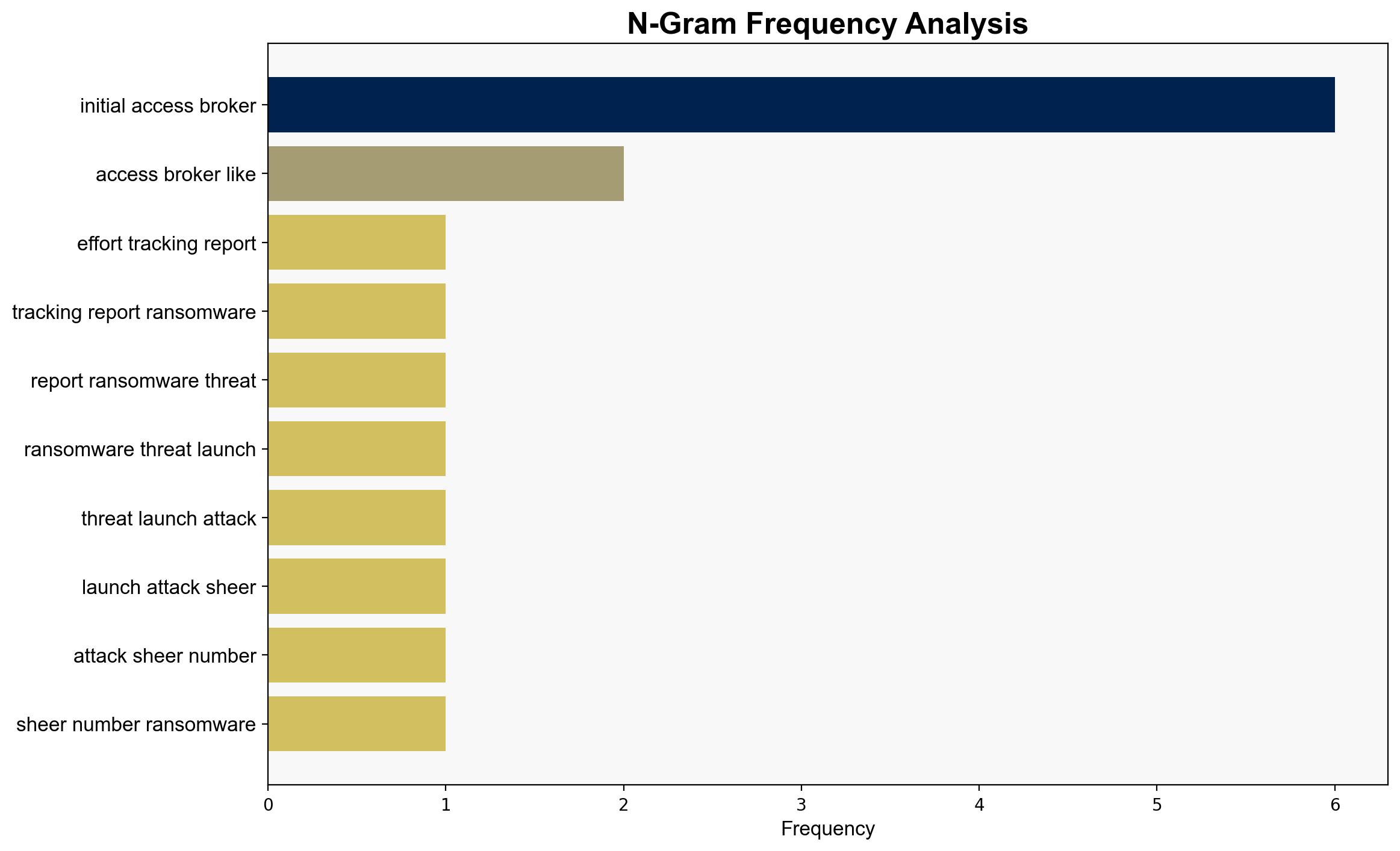
The report highlights the critical role of an entity known as “ToyMaker,” an initial access broker, in facilitating ransomware attacks. ToyMaker exploits vulnerable systems to install backdoors and steal credentials, which are then used by ransomware groups like Cactus. The primary motivation appears to be financial gain rather than political or state-sponsored objectives. Immediate attention is required to enhance cybersecurity defenses and monitor for indicators of compromise associated with ToyMaker’s activities.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Analysis of Competing Hypotheses (ACH)
The evidence strongly supports the hypothesis that ToyMaker operates as a financially motivated threat actor. Alternative hypotheses, such as political or espionage motivations, are less supported by the current evidence.
SWOT Analysis
Strengths: Ability to deploy custom malware and perform reconnaissance effectively.
Weaknesses: Reliance on initial access brokers makes operations detectable.
Opportunities: Increased vigilance and improved cybersecurity measures can disrupt operations.
Threats: Continued evolution of ransomware tactics and techniques.
Indicators Development
Key indicators include unusual network traffic patterns, unauthorized access attempts, and the presence of malware signatures associated with ToyMaker’s tools, such as LagToy.
3. Implications and Strategic Risks
The activities of ToyMaker underscore a significant risk to cybersecurity infrastructures globally. The potential for widespread data breaches and financial losses is high, particularly if ransomware groups continue to exploit these initial access points. The interconnected nature of cyber threats poses systemic risks across economic and national security domains.
4. Recommendations and Outlook
- Enhance network monitoring to detect early indicators of ToyMaker’s activities.
- Implement robust access controls and regular security audits to identify and mitigate vulnerabilities.
- Scenario-based projections suggest that without intervention, ransomware attacks may increase in frequency and sophistication. Conversely, proactive measures could significantly reduce the threat landscape.
5. Key Individuals and Entities
Joey Chen, Asheer Malhotra, Ashley Shen, Vitor Ventura, Brandon White.
6. Thematic Tags
(‘national security threats, cybersecurity, counter-terrorism, regional focus’, ‘cybersecurity’, ‘counter-terrorism’, ‘regional focus’)