Badenoch says hacking into Harriet Harman’s website 17 years ago ‘not the same’ as Reeves breaking law – Sky.com
Published on: 2025-10-30
Intelligence Report: Badenoch says hacking into Harriet Harman’s website 17 years ago ‘not the same’ as Reeves breaking law – Sky.com
1. BLUF (Bottom Line Up Front)
The analysis suggests that the situation involving Kemi Badenoch and Rachel Reeves reflects differing perceptions of legal and ethical standards within political contexts. The most supported hypothesis is that Badenoch’s comments aim to minimize the political impact of her past actions while highlighting Reeves’ current legal issues. Confidence level: Moderate. Recommended action: Monitor public and political reactions to gauge potential shifts in political alliances or public trust.
2. Competing Hypotheses
1. **Hypothesis A**: Kemi Badenoch’s comments are an attempt to downplay her past actions by drawing a distinction between a youthful indiscretion and a current legal violation, thereby mitigating political fallout.
2. **Hypothesis B**: Badenoch’s statements are strategically designed to deflect criticism and shift focus onto Rachel Reeves, leveraging the situation to weaken political opponents.
Using ACH 2.0, Hypothesis A is better supported as it aligns with Badenoch’s acknowledgment of her past actions as a “foolish prank” and her emphasis on the legal implications of Reeves’ actions.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the public perceives hacking and legal violations as distinctly different in severity. Another assumption is that political figures can effectively separate personal actions from their professional roles.
– **Red Flags**: Potential bias in Badenoch’s framing of the issue, as well as the risk of underestimating public sensitivity to cybersecurity issues. The lack of detailed legal context regarding both incidents could skew perceptions.
4. Implications and Strategic Risks
The situation could lead to increased scrutiny of political figures’ past and present actions, impacting public trust. There is a risk of escalating political tensions and potential reputational damage. Cybersecurity concerns might gain prominence, influencing legislative priorities.
5. Recommendations and Outlook
- Monitor media and public discourse to assess shifts in public opinion and potential impacts on political stability.
- Consider proactive communication strategies to address cybersecurity concerns and reinforce ethical standards in political conduct.
- Scenario Projections:
- Best: The issue subsides with minimal impact on political dynamics.
- Worst: Escalation leads to broader investigations and political instability.
- Most Likely: Temporary political turbulence with minor long-term effects.
6. Key Individuals and Entities
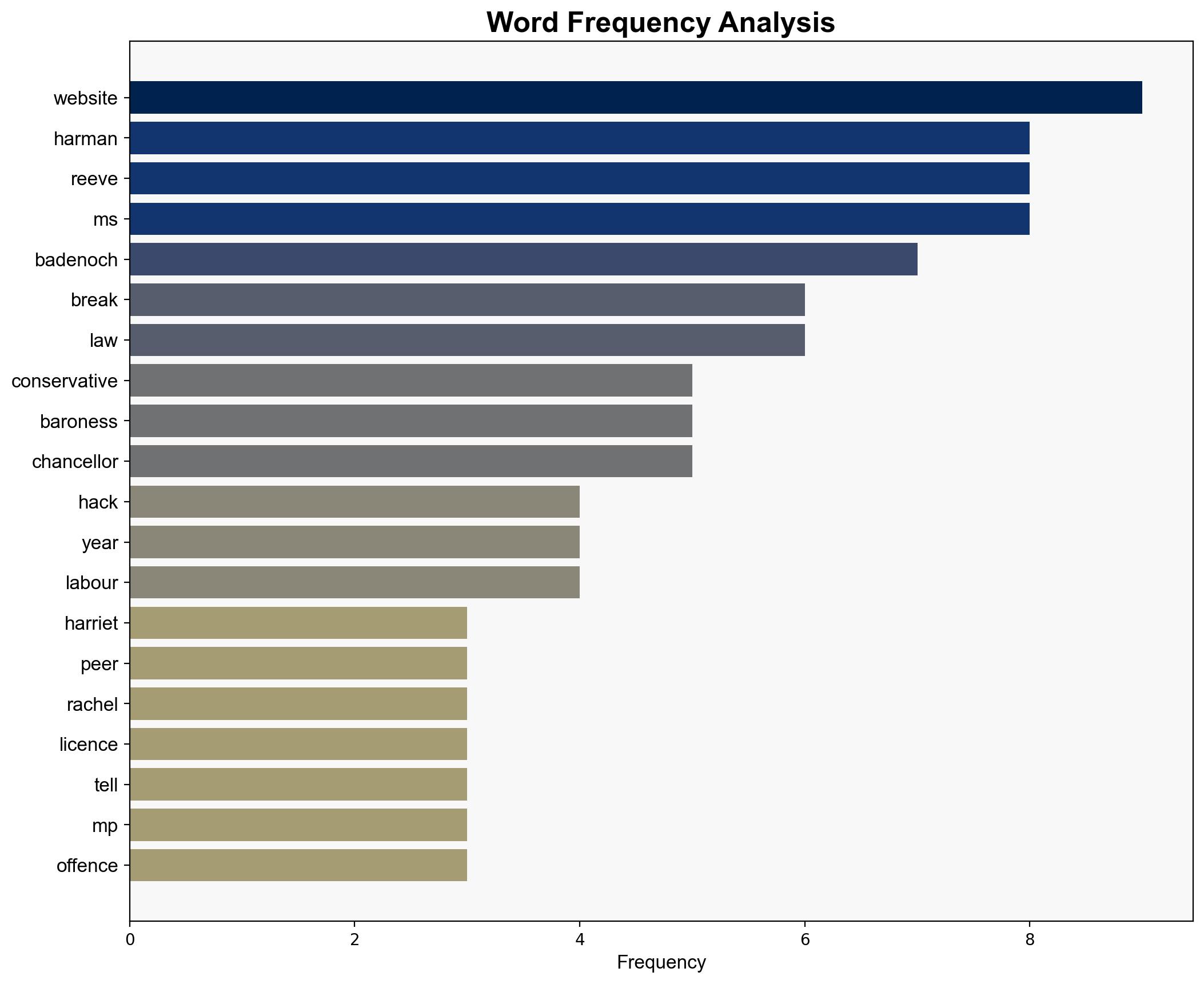
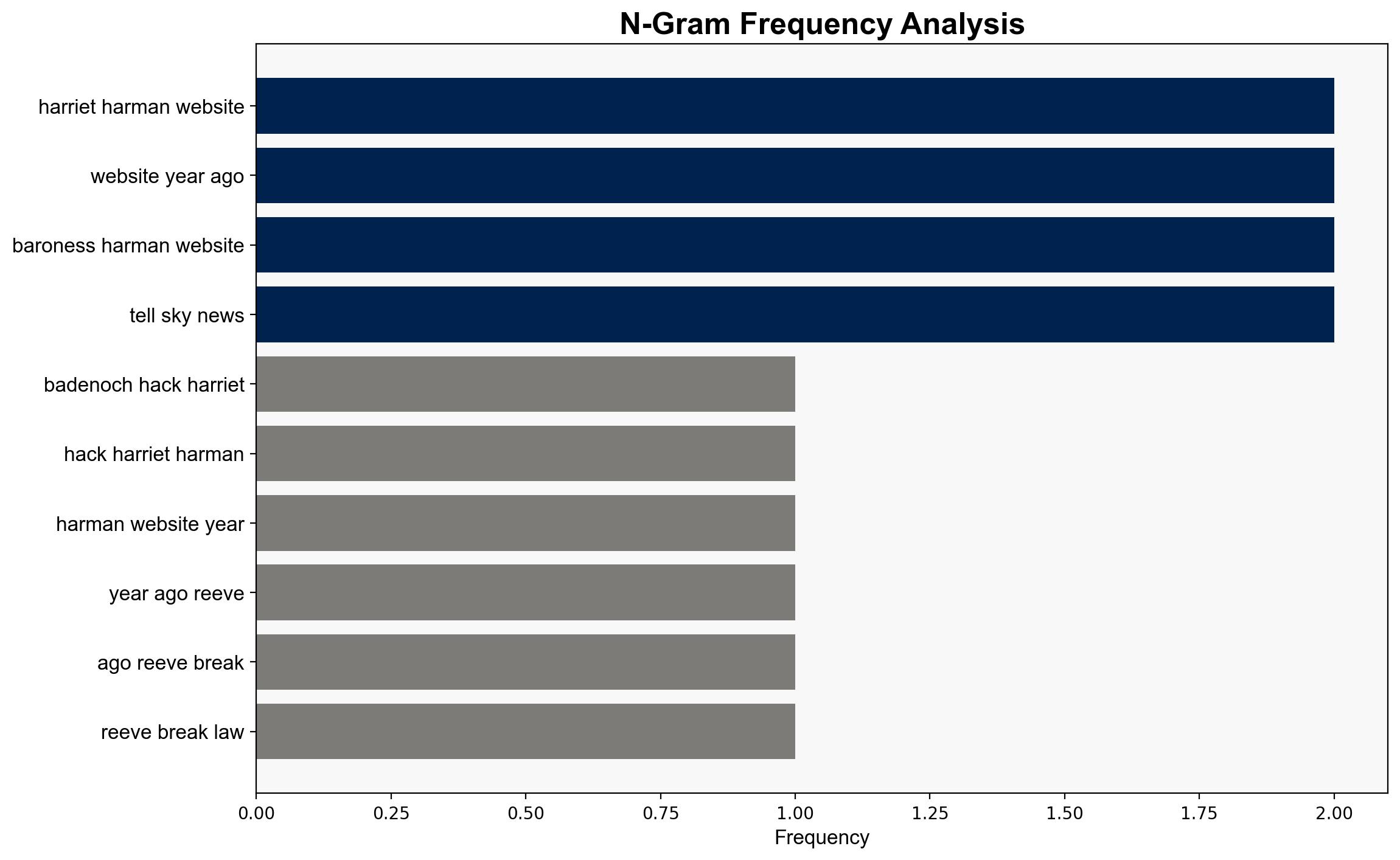
– Kemi Badenoch
– Rachel Reeves
– Harriet Harman
– Harvey Wheeler
7. Thematic Tags
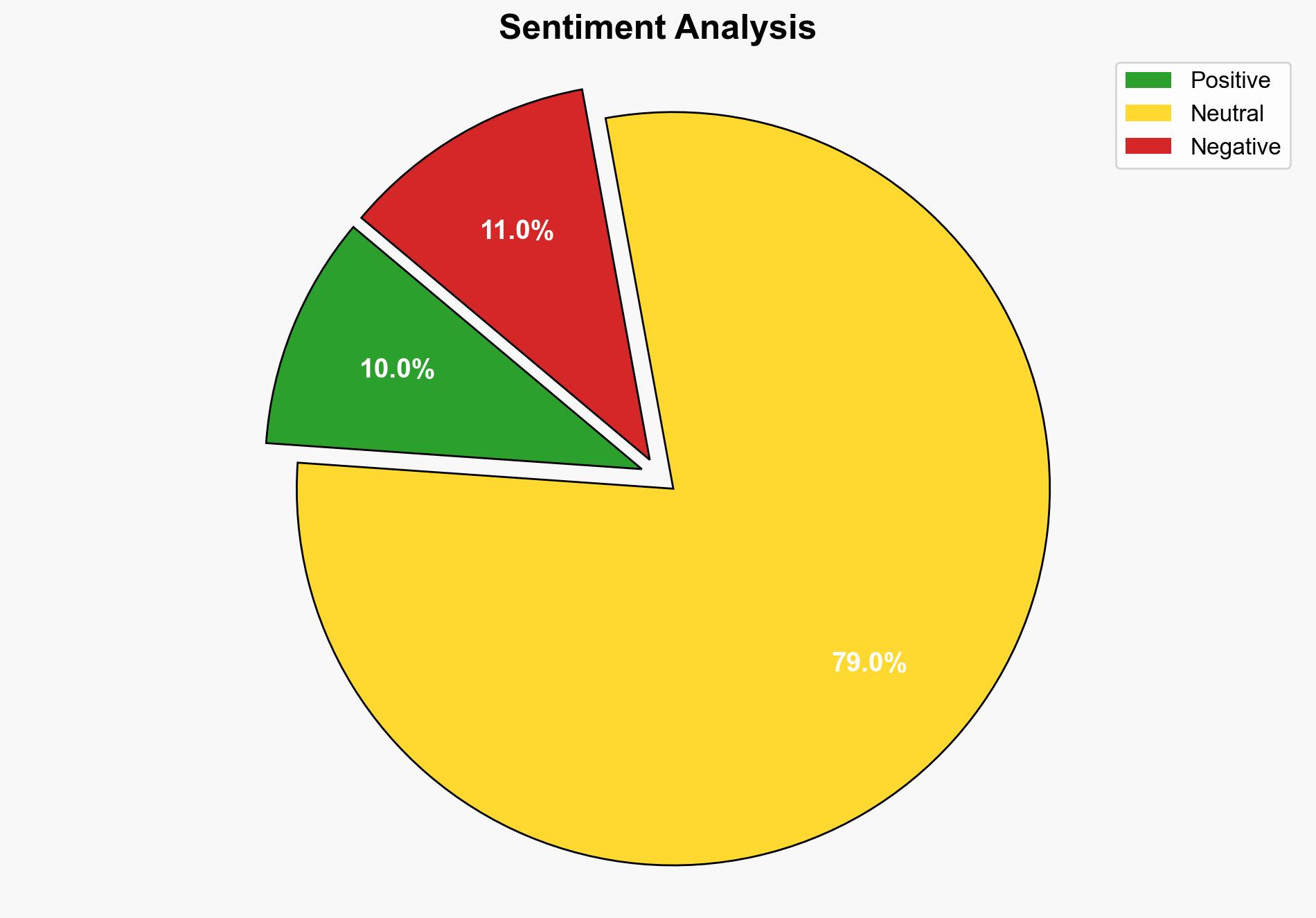
national security threats, cybersecurity, political strategy, public trust