Best Practices For Effective Data Security And Governance Policies – Bitrebels.com
Published on: 2025-07-12
Intelligence Report: Best Practices For Effective Data Security And Governance Policies – Bitrebels.com
1. BLUF (Bottom Line Up Front)
The report highlights the critical need for robust data security and governance policies to protect sensitive information and maintain stakeholder trust. Key recommendations include implementing zero trust architecture, end-to-end encryption, regular security audits, and multi-factor authentication (MFA). These measures are essential to mitigate risks, prevent data breaches, and ensure compliance with regulatory standards.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulations indicate that cyber adversaries often exploit weak access controls and outdated software. Implementing zero trust architecture can significantly reduce these vulnerabilities.
Indicators Development
Monitoring for anomalies such as unusual login patterns or data access requests can provide early warnings of potential breaches.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of attack vectors targeting unencrypted data in transit. Strengthening encryption protocols is recommended.
Network Influence Mapping
Mapping internal and external network influences helps identify potential insider threats and external attack vectors.
3. Implications and Strategic Risks
Failure to implement effective data security and governance policies could lead to significant financial losses, reputational damage, and legal penalties. The increasing sophistication of cyber threats poses a systemic risk to organizations, potentially affecting economic stability and national security.
4. Recommendations and Outlook
- Adopt zero trust architecture to ensure all access requests are verified before granting access.
- Implement end-to-end encryption and regularly update encryption keys to protect data in transit and at rest.
- Conduct regular security audits and risk assessments to identify and address vulnerabilities.
- Deploy multi-factor authentication to enhance user verification processes.
- Scenario-based projections: Best case – Enhanced security posture and compliance; Worst case – Data breach with significant impact; Most likely – Incremental improvements with ongoing challenges.
5. Key Individuals and Entities
No specific individuals are mentioned in the source text.
6. Thematic Tags
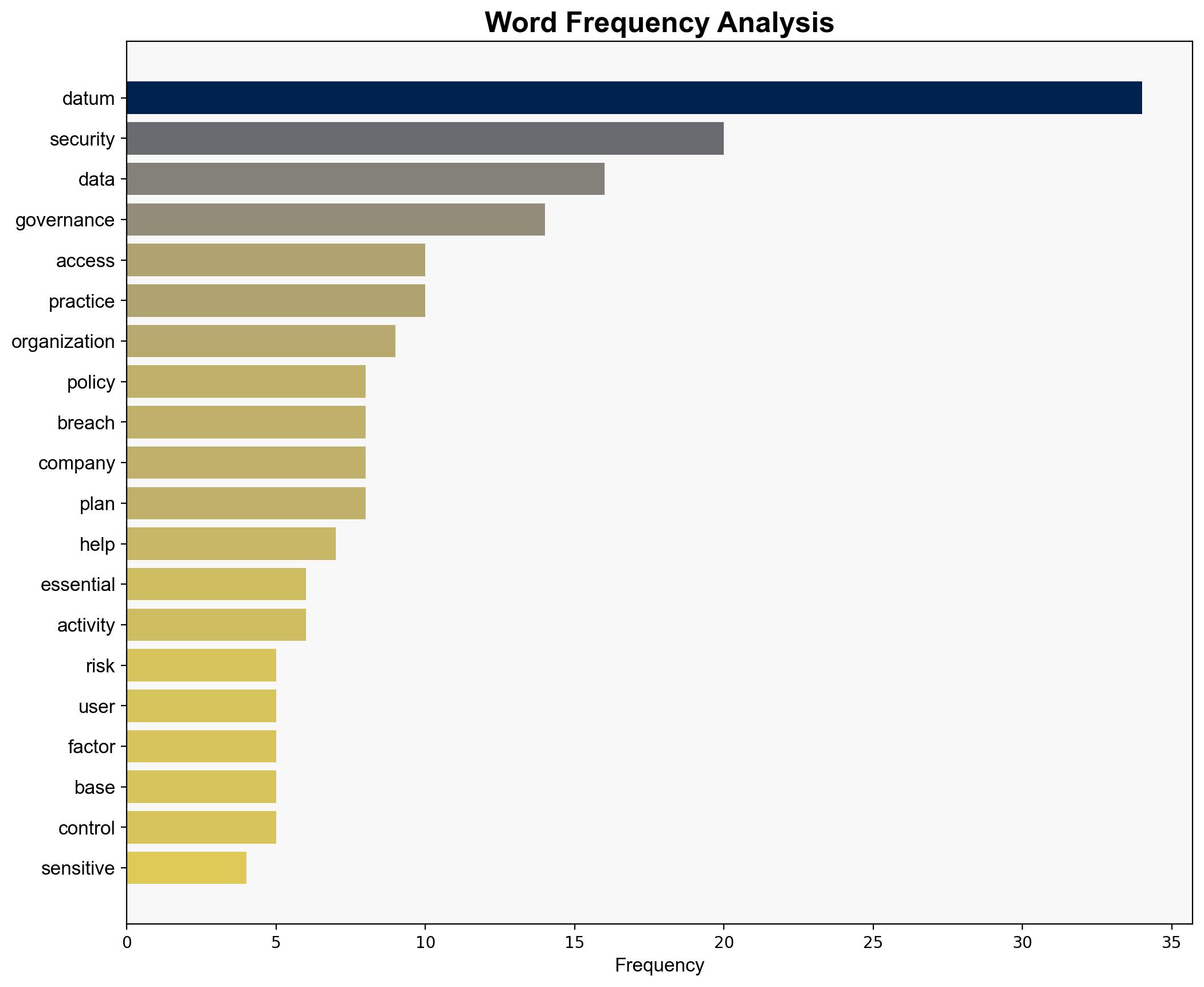
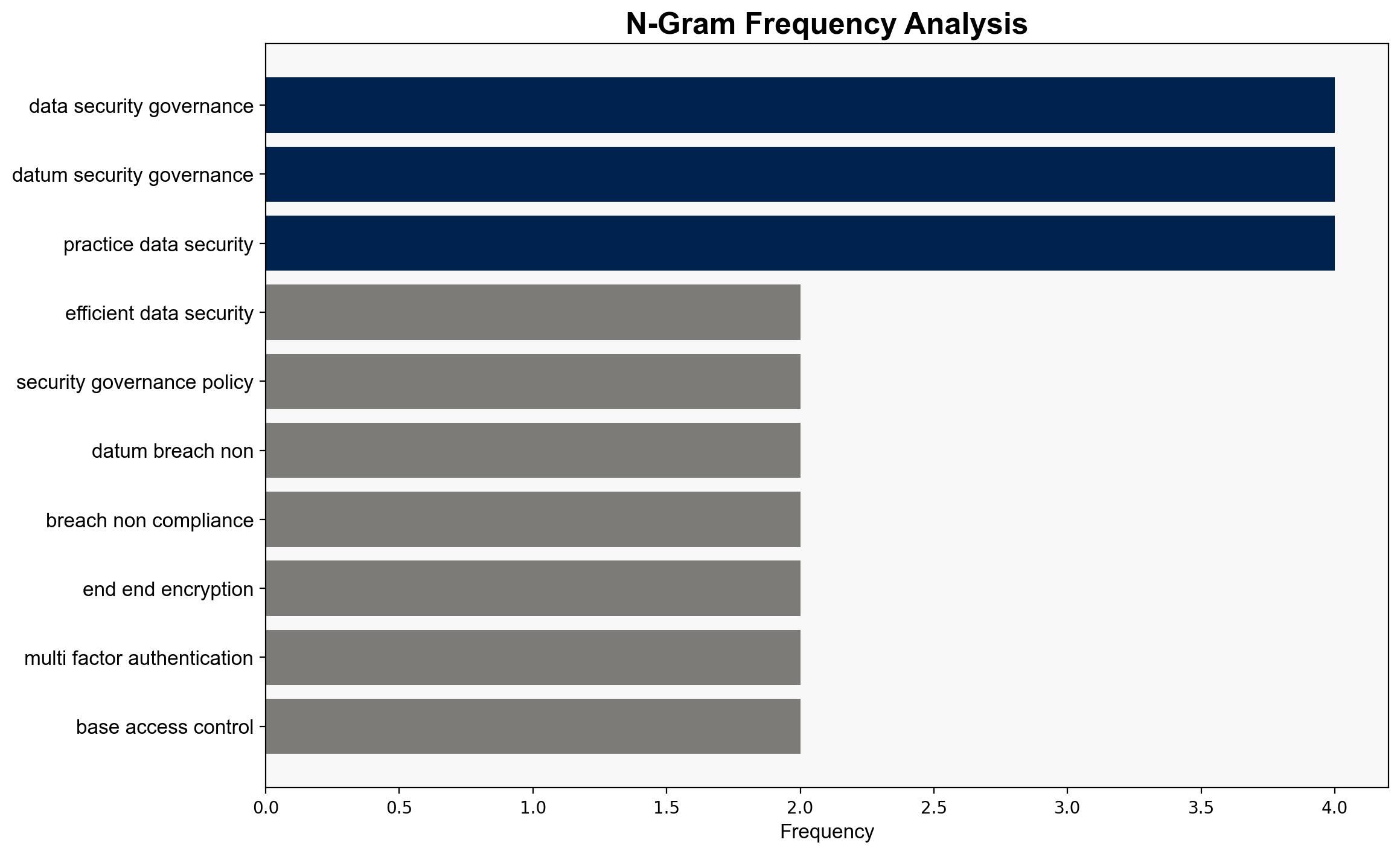
national security threats, cybersecurity, data governance, risk management