Big August update fixes dozens of security flaws in Windows and Office – PCWorld
Published on: 2025-09-10
Intelligence Report: Big August update fixes dozens of security flaws in Windows and Office – PCWorld
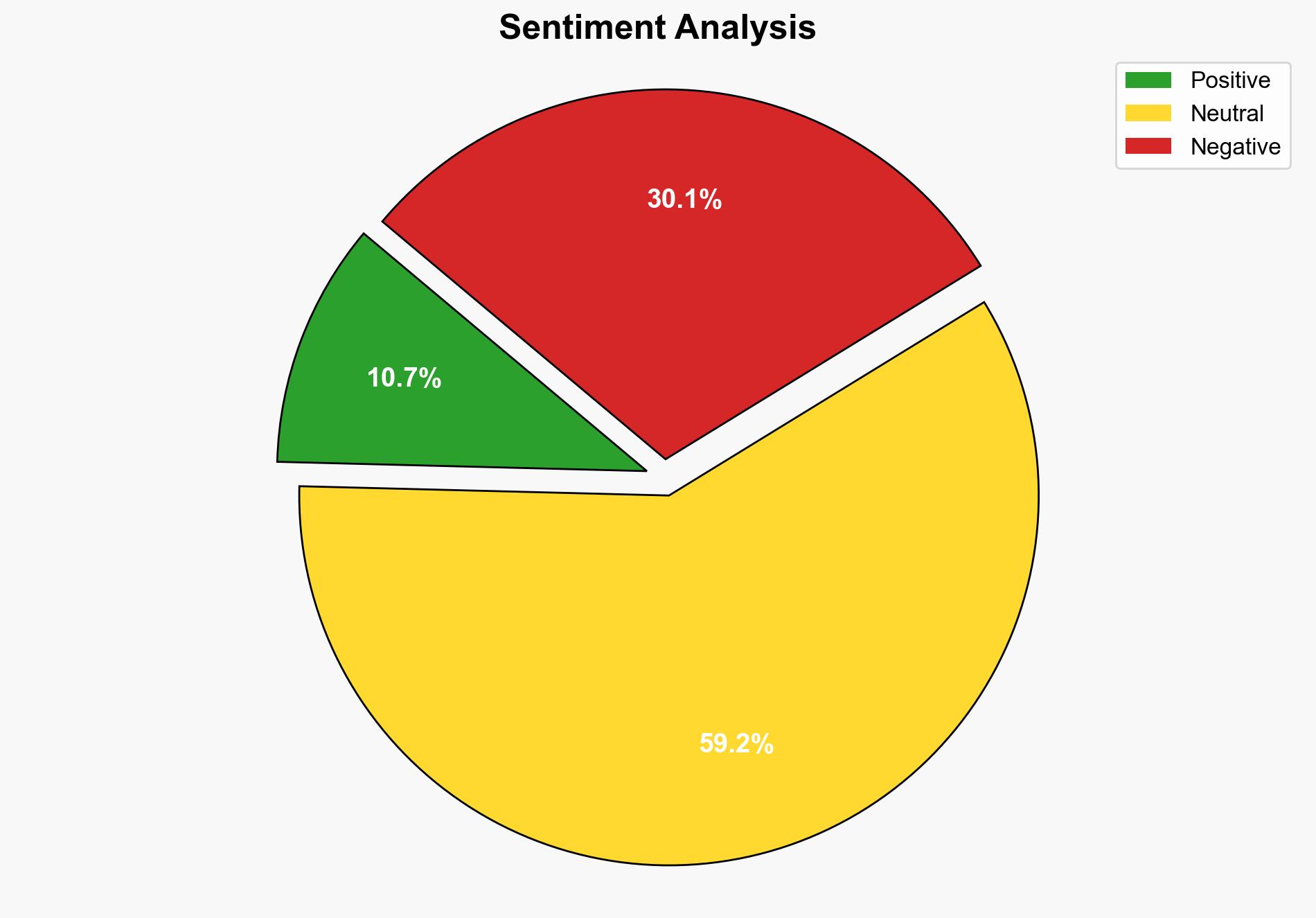
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that the recent Microsoft security updates are a proactive measure to mitigate known vulnerabilities that could be exploited by cyber attackers. The strategic recommendation is to ensure all systems are updated promptly to prevent potential breaches. Confidence level: High.
2. Competing Hypotheses
1. **Hypothesis A**: Microsoft’s security updates are a routine and proactive measure to address vulnerabilities and enhance system security, reducing the risk of exploitation.
2. **Hypothesis B**: The updates are a reactive response to specific, credible threats that have been identified, indicating a higher immediate risk of exploitation.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported. The routine nature of Patch Tuesday and the broad scope of vulnerabilities addressed suggest a systematic approach rather than a response to specific threats.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that Microsoft has identified these vulnerabilities independently and that they are not responding to external pressure or specific incidents.
– **Red Flags**: Sparse details on the vulnerabilities may indicate an attempt to downplay the severity or scope of potential threats. The lack of specific threat intelligence raises questions about the immediacy of the risk.
– **Blind Spots**: The report does not address whether similar vulnerabilities exist in other software platforms, which could indicate a broader systemic issue.
4. Implications and Strategic Risks
The updates highlight the persistent risk of cyber threats, particularly those targeting critical infrastructure and high-performance computing environments. Failure to update systems could lead to significant data breaches, financial loss, and reputational damage. The potential for these vulnerabilities to be exploited by state or non-state actors poses a national security threat.
5. Recommendations and Outlook
- **Immediate Action**: Ensure all systems are updated with the latest patches to mitigate vulnerabilities.
- **Monitoring**: Establish continuous monitoring for any signs of exploitation or emerging threats.
- **Scenario Projections**:
– **Best Case**: All systems are updated without incident, and vulnerabilities are effectively mitigated.
– **Worst Case**: Unpatched systems are exploited, leading to widespread data breaches and operational disruptions.
– **Most Likely**: Organizations with robust update protocols will remain secure, while those with delayed updates may face targeted attacks.
6. Key Individuals and Entities
– Microsoft Corporation
– Users of Windows and Office products
– Cybersecurity teams within affected organizations
7. Thematic Tags
national security threats, cybersecurity, software vulnerabilities, Microsoft, Patch Tuesday