Black Hat Investigation Attempted Exploitation of Registration Server – Cisco.com
Published on: 2025-09-03
Intelligence Report: Black Hat Investigation Attempted Exploitation of Registration Server – Cisco.com
1. BLUF (Bottom Line Up Front)
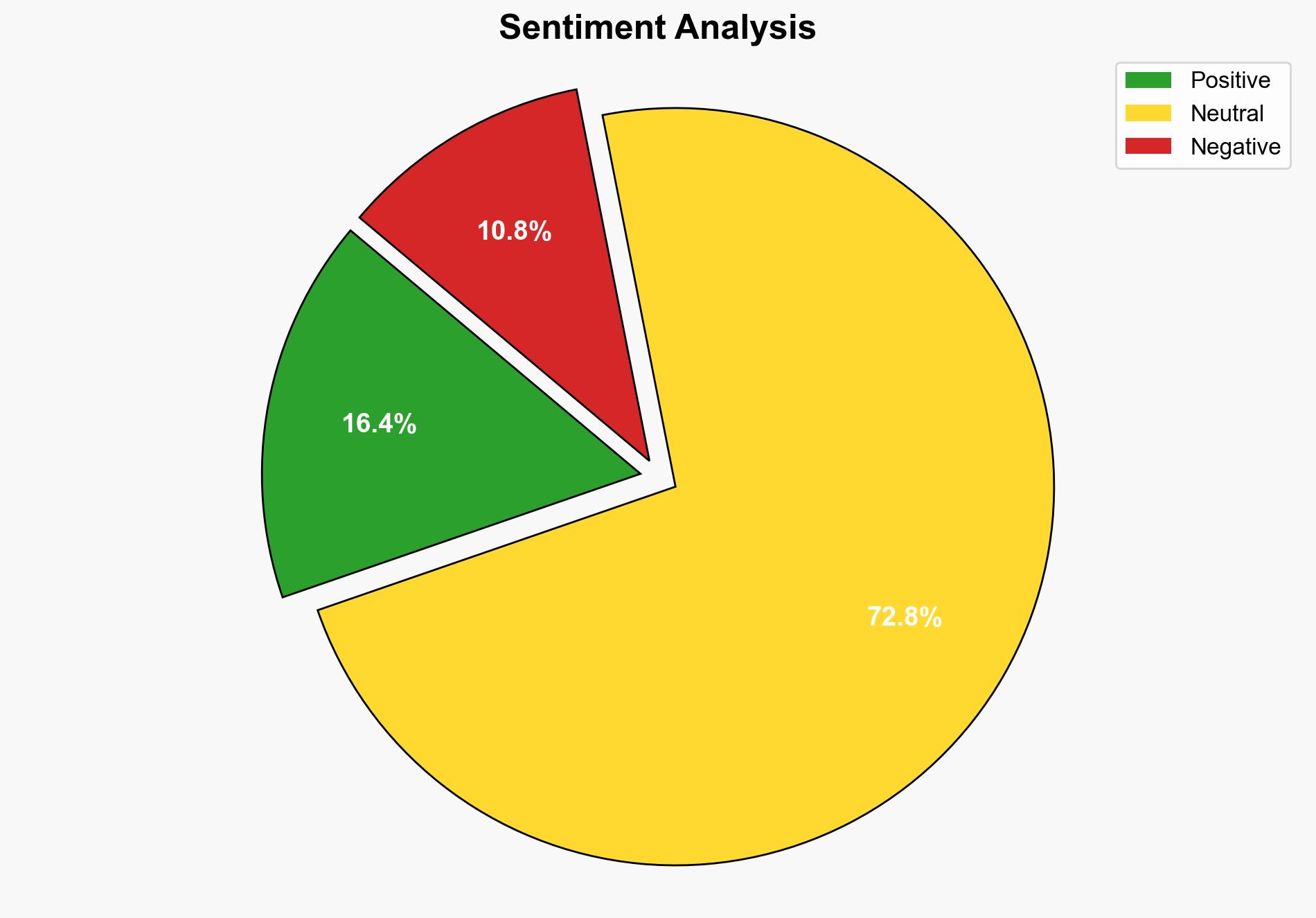
The most supported hypothesis is that the attempted exploitation of the Cisco.com registration server was a targeted attack leveraging known vulnerabilities in SAP NetWeaver. The confidence level is moderate due to the presence of corroborating technical indicators and the context of the Black Hat conference. Recommended actions include enhancing network monitoring and implementing specific countermeasures against identified vulnerabilities.
2. Competing Hypotheses
1. **Targeted Attack Hypothesis**: The exploitation attempt was a deliberate attack using known vulnerabilities in SAP NetWeaver, possibly by a sophisticated actor exploiting the conference environment’s unique challenges.
2. **Opportunistic Scanning Hypothesis**: The activity was part of routine scanning and probing by cybercriminals or researchers, taking advantage of the high-profile nature of the Black Hat conference to test various systems indiscriminately.
Using the Analysis of Competing Hypotheses (ACH) 2.0, the Targeted Attack Hypothesis is better supported due to the specific use of the Zgrab tool, known for penetration testing, and the alignment with known vulnerabilities (CVE) in SAP NetWeaver.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the presence of the Zgrab tool indicates malicious intent rather than benign research. The hypothesis also assumes the attackers had prior knowledge of the SAP NetWeaver vulnerability.
– **Red Flags**: The lack of direct attribution to a specific actor raises questions about the true intent and capability of the attackers. The possibility of false flag operations or misinterpretation of benign research activities remains.
– **Missing Data**: Detailed logs of the attacker’s activities and motivations are unavailable, limiting the ability to fully assess intent.
4. Implications and Strategic Risks
The incident highlights the vulnerability of public-facing applications during high-profile events, increasing the risk of data breaches and reputational damage. If the Targeted Attack Hypothesis is correct, it suggests a heightened threat environment requiring increased vigilance. A failure to address these vulnerabilities could lead to further exploitation attempts, potentially impacting other critical systems.
5. Recommendations and Outlook
- Enhance network monitoring and deploy advanced threat detection tools to identify and mitigate similar threats in real-time.
- Conduct a thorough vulnerability assessment of all public-facing applications, particularly those using SAP NetWeaver.
- Implement a robust incident response plan tailored to the unique challenges of conference environments.
- Scenario Projections:
- Best Case: Strengthened defenses deter future attacks, and no further incidents occur.
- Worst Case: Unaddressed vulnerabilities lead to successful breaches and data exfiltration.
- Most Likely: Continued attempts are made, but enhanced defenses prevent successful exploitation.
6. Key Individuals and Entities
No specific individuals are identified in the intelligence. The focus remains on the entities involved, such as Cisco, SAP NetWeaver, and the Black Hat conference.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus