Bondi Beach attack underscores persistent influence of Islamic State ideology in Asia despite territorial los…
Published on: 2025-12-28
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
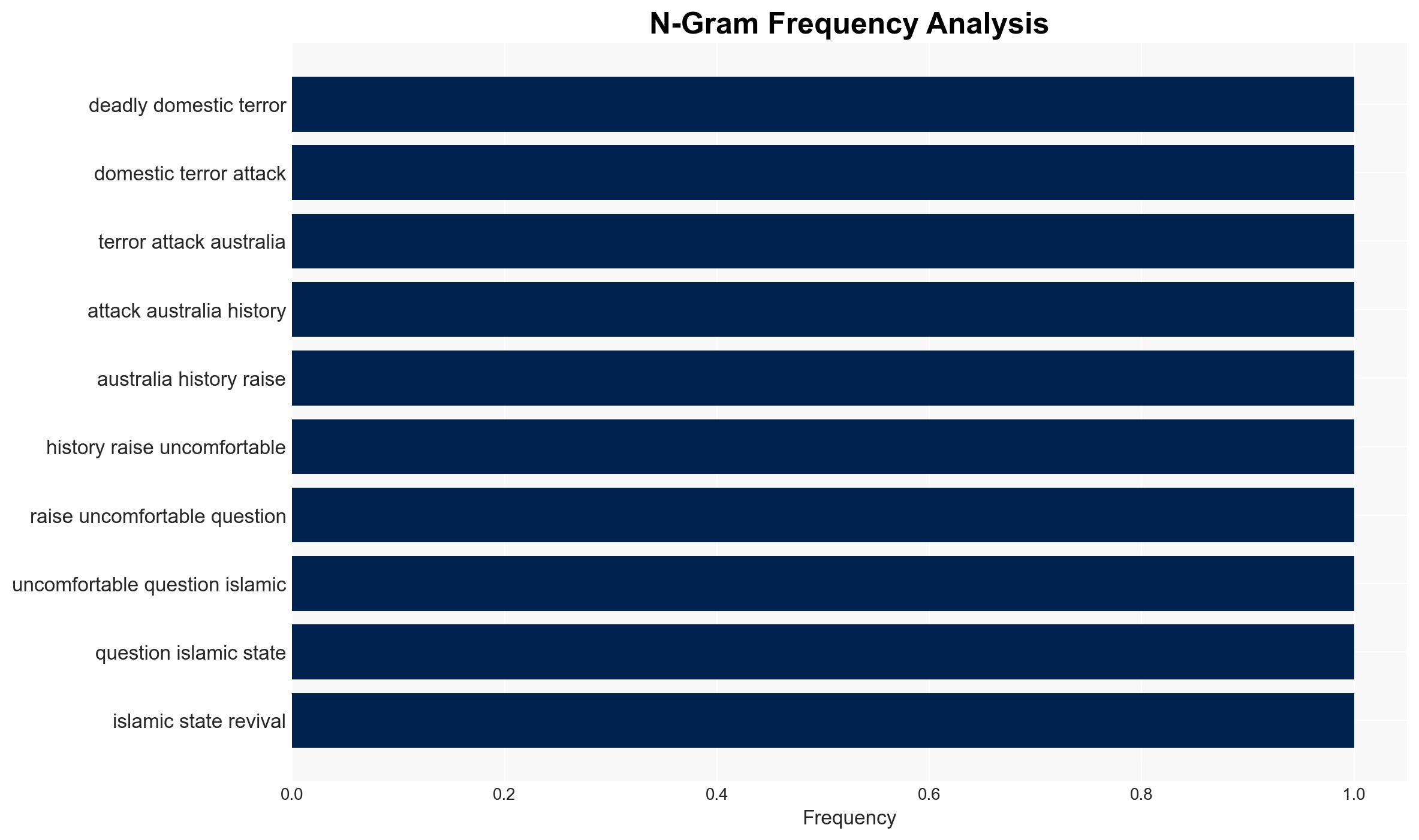
Intelligence Report: Bondi attack No Islamic State isnt back in Asia but its influence sure has endured across the region
1. BLUF (Bottom Line Up Front)
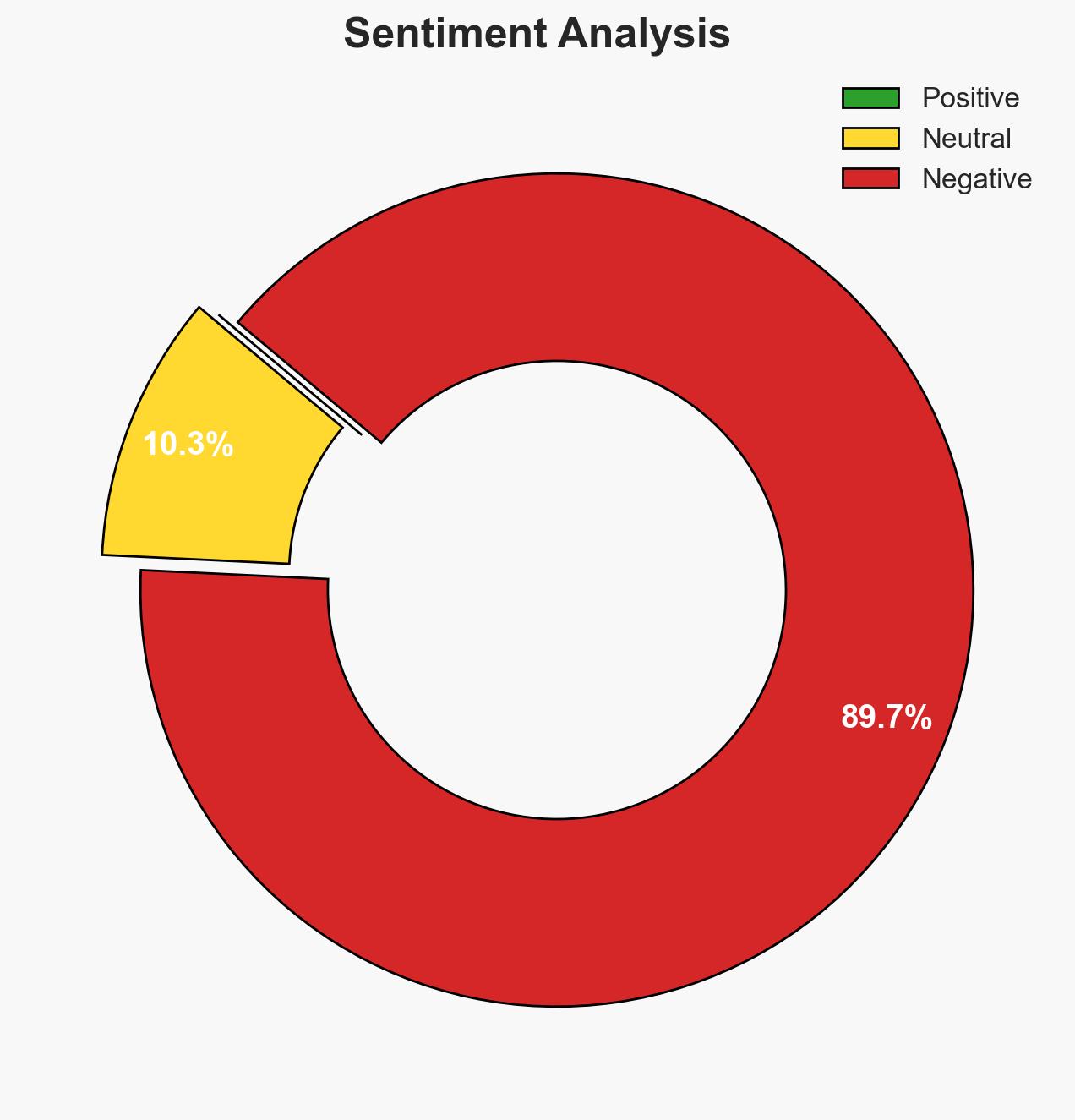
The recent attack in Bondi, Australia, underscores the enduring influence of Islamic State (IS) ideology in Asia despite the group’s territorial defeat. The attack, executed by individuals radicalized through IS propaganda, highlights the persistent threat of IS-inspired terrorism. The most likely hypothesis is that IS continues to wield significant influence through online propaganda, rather than direct operational control. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: IS is experiencing a revival in Asia, with increased operational capabilities and direct involvement in attacks. Supporting evidence includes the recent attack patterns and travel of perpetrators to IS-influenced regions. Contradicting evidence includes the lack of direct claims of responsibility and limited evidence of operational training.
- Hypothesis B: IS influence persists primarily through propaganda and ideological inspiration, rather than direct operational control. Supporting evidence includes the absence of formal claims of responsibility and the focus on online radicalization. Contradicting evidence is the potential for informal support networks in IS-aligned regions.
- Assessment: Hypothesis B is currently better supported due to the lack of direct IS operational involvement and the emphasis on ideological influence through propaganda. Key indicators that could shift this judgment include evidence of direct IS command and control or formal claims of responsibility for attacks.
3. Key Assumptions and Red Flags
- Assumptions: IS lacks significant territorial control in Asia; IS propaganda remains a potent radicalization tool; local groups may align with IS ideology without direct coordination.
- Information Gaps: Details on the extent of the duo’s interactions with IS-aligned groups in the Philippines; the role of online networks in facilitating radicalization.
- Bias & Deception Risks: Potential over-reliance on open-source reporting; risk of misattributing attacks to IS without clear evidence of direct involvement.
4. Implications and Strategic Risks
The persistence of IS ideology poses ongoing challenges for regional security and counter-terrorism efforts. The adaptation of IS tactics to focus on propaganda may lead to increased lone-wolf attacks inspired by online content.
- Political / Geopolitical: Potential strain on regional cooperation in counter-terrorism efforts; increased scrutiny on nations with IS-aligned groups.
- Security / Counter-Terrorism: Heightened threat of IS-inspired attacks; need for enhanced monitoring of online radicalization channels.
- Cyber / Information Space: IS’s use of digital platforms for propaganda and recruitment remains a critical threat vector.
- Economic / Social: Potential impact on tourism and public safety perceptions; risk of social polarization due to increased fear of terrorism.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of online extremist content; increase intelligence sharing on IS-aligned activities in the region.
- Medium-Term Posture (1–12 months): Strengthen regional counter-terrorism partnerships; invest in community resilience programs to counter radicalization.
- Scenario Outlook:
- Best: Successful disruption of IS propaganda networks reduces attack frequency.
- Worst: Increased frequency of IS-inspired attacks due to effective propaganda dissemination.
- Most-Likely: Continued sporadic IS-inspired attacks with limited direct IS involvement.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
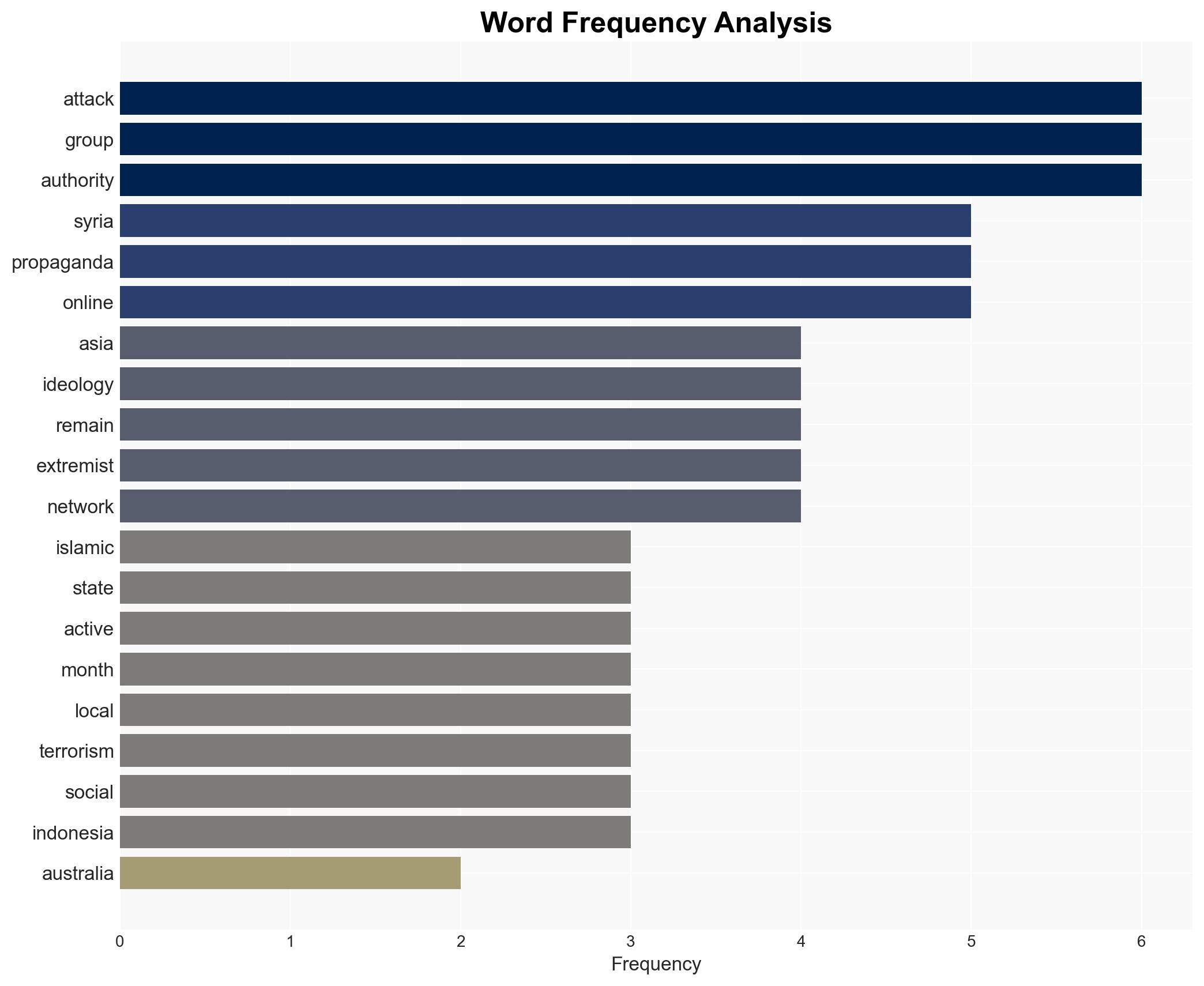
national security threats, counter-terrorism, Islamic State, radicalization, online propaganda, regional security, lone-wolf attacks, Southeast Asia
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Expose and correct potential biases in assessments through red-teaming and structured challenge.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map influence relationships to assess actor impact.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us