Bondi Beach tragedy underscores Hanukkah’s legacy of resistance against oppression and identity preservation
Published on: 2025-12-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Bondi Beach brings back the true meaning of Hanukkah resistance
1. BLUF (Bottom Line Up Front)
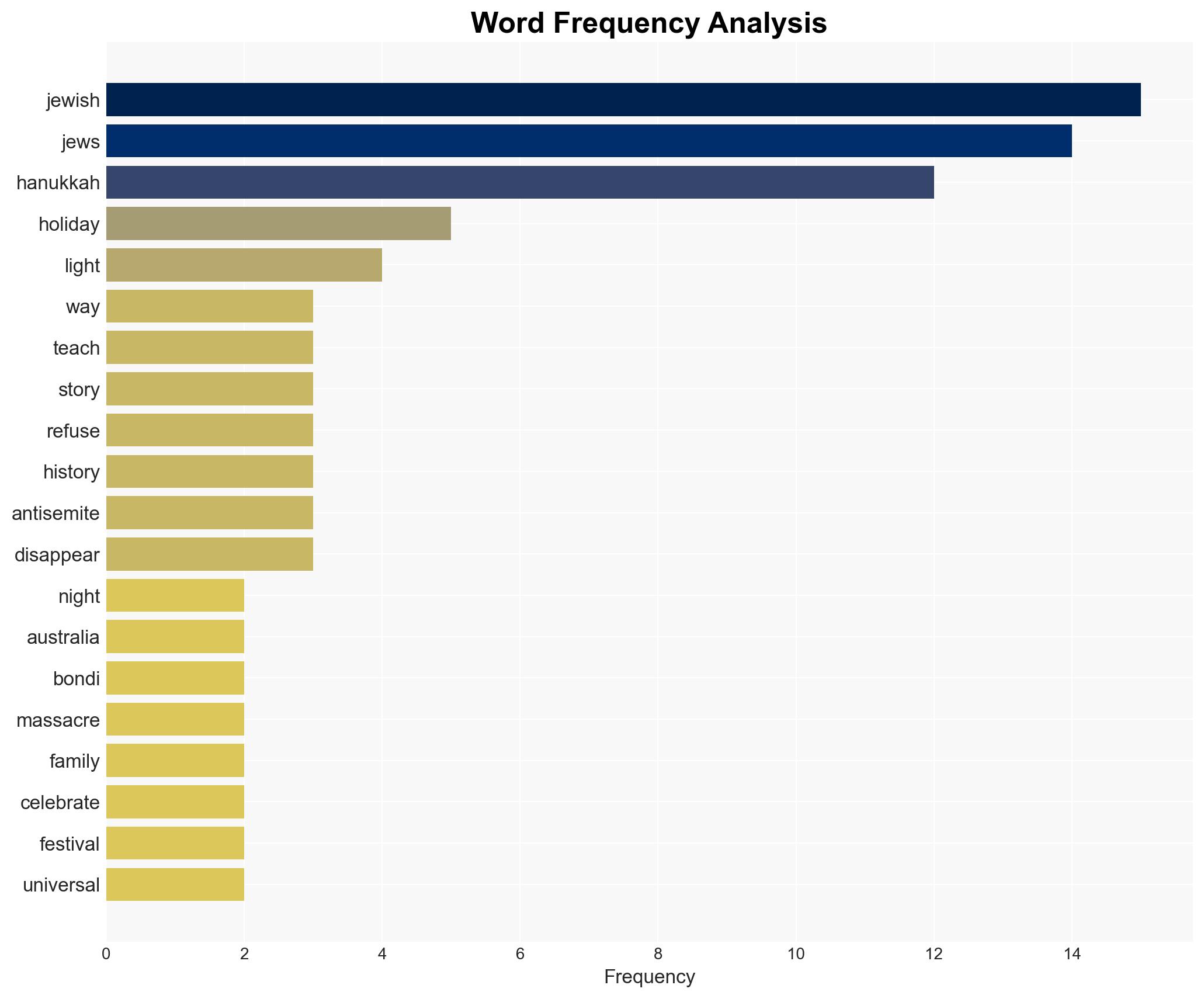
The attack on Bondi Beach during Hanukkah underscores a significant threat to Jewish communities, highlighting the persistence of antisemitic violence. The most likely hypothesis is that the attack was ideologically motivated, targeting Jewish identity and practices. This incident affects Jewish communities globally and raises concerns about the adequacy of current security measures. Overall confidence in this judgment is moderate, given the lack of detailed information on the attackers’ motivations.
2. Competing Hypotheses
- Hypothesis A: The attack was ideologically motivated, specifically targeting Jewish identity and religious practices. This is supported by the timing of the attack during Hanukkah and the historical context of antisemitic violence. However, the specific motivations of the attackers remain unclear, creating uncertainty.
- Hypothesis B: The attack was opportunistic, with the attackers exploiting the event for maximum impact without specific ideological motivations. This hypothesis is less supported due to the symbolic timing and location of the attack, which suggests a targeted approach.
- Assessment: Hypothesis A is currently better supported due to the symbolic nature of the attack and historical patterns of antisemitic violence. Indicators that could shift this judgment include evidence of the attackers’ affiliations or statements clarifying their motives.
3. Key Assumptions and Red Flags
- Assumptions: The attack was premeditated; the attackers had specific ideological motivations; Jewish communities are primary targets of similar future attacks.
- Information Gaps: Detailed profiles of the attackers; evidence of any organizational backing; specific communications or manifestos from the attackers.
- Bias & Deception Risks: Potential bias in interpreting the attack as solely antisemitic without considering other motives; risk of over-reliance on historical patterns without current evidence.
4. Implications and Strategic Risks
This development could exacerbate tensions in multicultural societies and lead to increased security measures around Jewish events. It may also influence policy discussions on counter-terrorism and community protection.
- Political / Geopolitical: Potential for increased diplomatic tensions if international actors are perceived as influencing or supporting antisemitic actions.
- Security / Counter-Terrorism: Heightened threat environment for Jewish communities; potential for copycat attacks.
- Cyber / Information Space: Possible exploitation of the event in online propaganda by extremist groups to recruit or radicalize individuals.
- Economic / Social: Increased security costs for Jewish organizations; potential social fragmentation if communities feel inadequately protected.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance security at Jewish events; increase intelligence sharing among law enforcement agencies; monitor extremist online forums for related activity.
- Medium-Term Posture (1–12 months): Develop community resilience programs; strengthen partnerships with Jewish organizations; enhance counter-terrorism capabilities.
- Scenario Outlook:
- Best: Increased security measures prevent further attacks, fostering a sense of safety.
- Worst: Escalation of antisemitic violence leading to significant social unrest.
- Most-Likely: Continued sporadic threats necessitating ongoing vigilance and security enhancements.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
Counter-Terrorism, antisemitism, religious violence, community security, ideological extremism, multicultural tensions, security policy
Structured Analytic Techniques Applied
- ACH 2.0: Reconstruct likely threat actor intentions via hypothesis testing and structured refutation.
- Indicators Development: Track radicalization signals and propaganda patterns to anticipate operational planning.
- Narrative Pattern Analysis: Analyze spread/adaptation of ideological narratives for recruitment/incitement signals.
Explore more:
Counter-Terrorism Briefs ·
Daily Summary ·
Support us