BONDI WILL USE ‘NATIONAL SECURITY’ CLAIMS TO SCRUB FILES – Kenklippenstein.com
Published on: 2025-11-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report:
1. BLUF (Bottom Line Up Front)
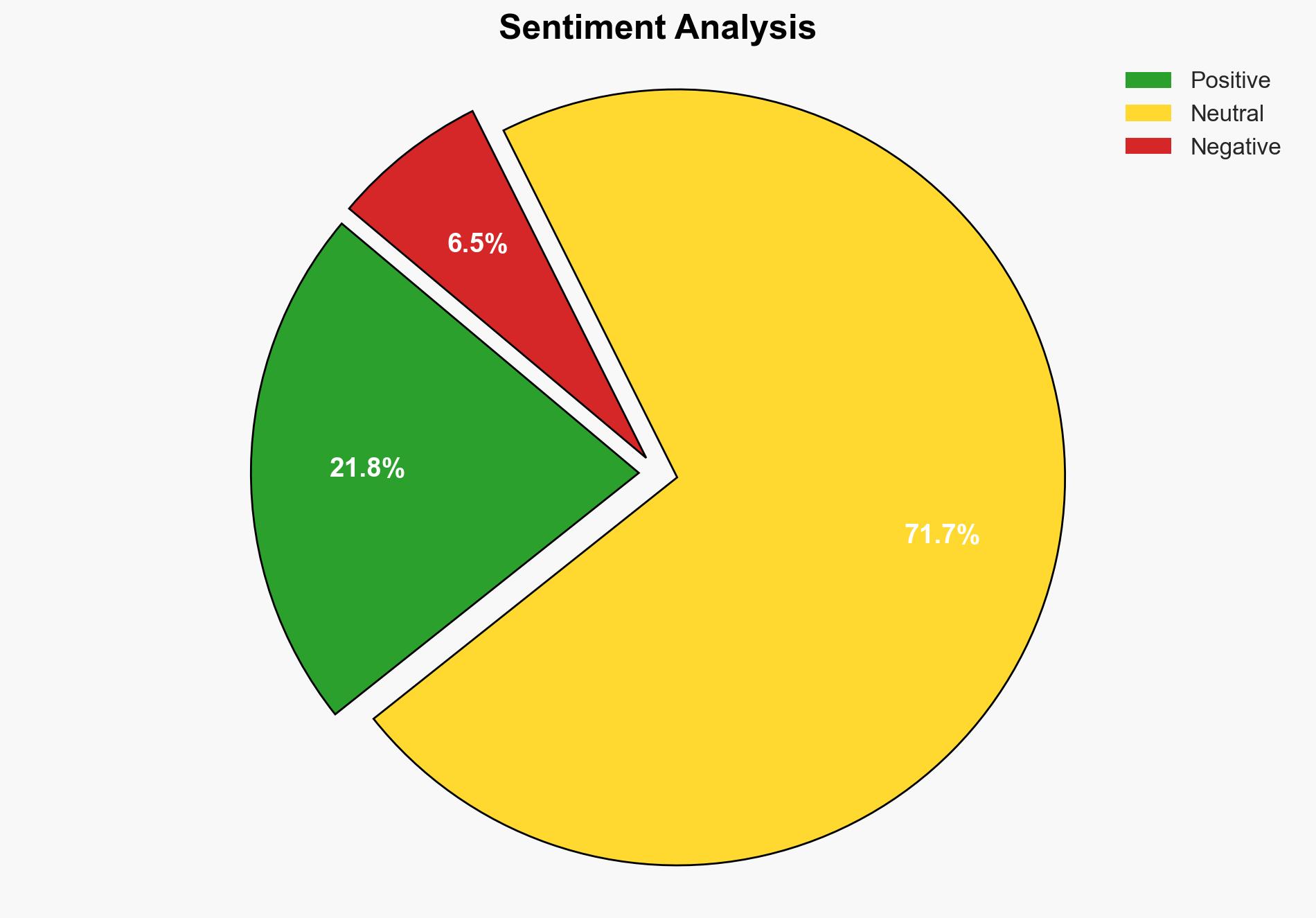
With a moderate confidence level, the most supported hypothesis is that the invocation of “national security” to restrict the release of Epstein-related files is primarily a protective measure for certain individuals and institutions rather than a genuine national security concern. Recommended action includes advocating for a transparent review process by an independent body to assess the legitimacy of national security claims.
2. Competing Hypotheses
Hypothesis 1: The use of “national security” to block the release of Epstein files is a legitimate concern to protect intelligence methods and sources.
Hypothesis 2: The “national security” claim is a pretext to protect influential individuals and institutions from reputational harm and legal consequences.
Hypothesis 2 is more likely given the context and historical precedence of using national security as a shield for sensitive information that could cause political embarrassment. The lack of specific evidence indicating genuine national security threats supports this hypothesis.
3. Key Assumptions and Red Flags
Assumptions: The assumption that all national security claims are made in good faith is questionable given past abuses. The belief that the files contain sensitive intelligence methods is not substantiated by available evidence.
Red Flags: The timing of the national security claim coincides with increased public and congressional pressure for transparency, suggesting potential ulterior motives. The involvement of high-profile individuals in the case raises the risk of bias in decision-making.
4. Implications and Strategic Risks
The primary risk is the erosion of public trust in government transparency and accountability, which could lead to increased political polarization and civil unrest. There is also a risk of international diplomatic tensions if foreign dignitaries are implicated and protected under the guise of national security.
5. Recommendations and Outlook
- Advocate for an independent review panel to assess the legitimacy of national security claims related to the Epstein files.
- Encourage legislative measures to tighten the criteria for invoking national security in transparency-related matters.
- Best-case scenario: Transparent release of files with minimal redactions, restoring public trust.
- Worst-case scenario: Continued obfuscation leads to widespread public disillusionment and potential civil unrest.
- Most-likely scenario: Partial release with significant redactions, leading to ongoing public skepticism.
6. Key Individuals and Entities
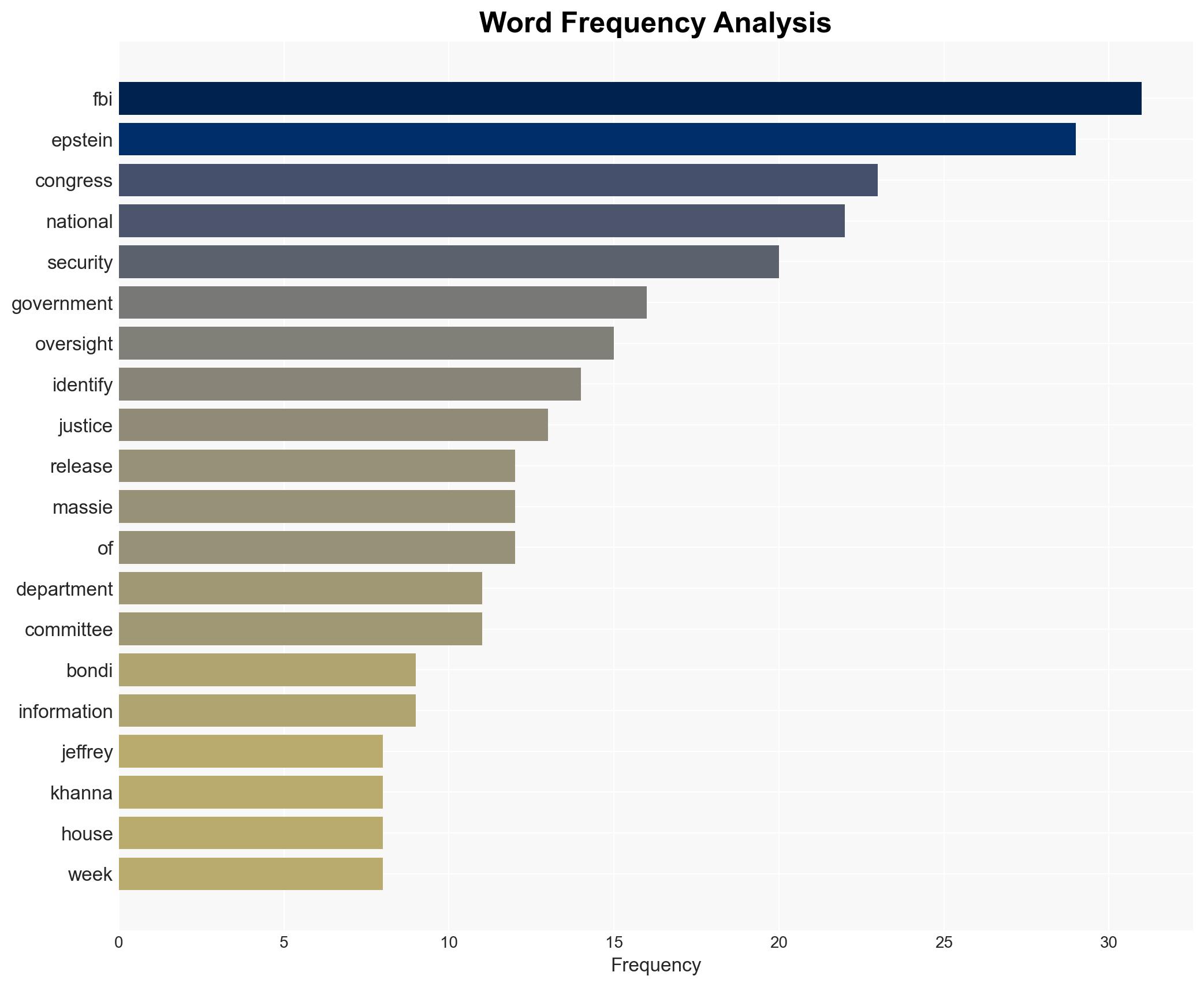
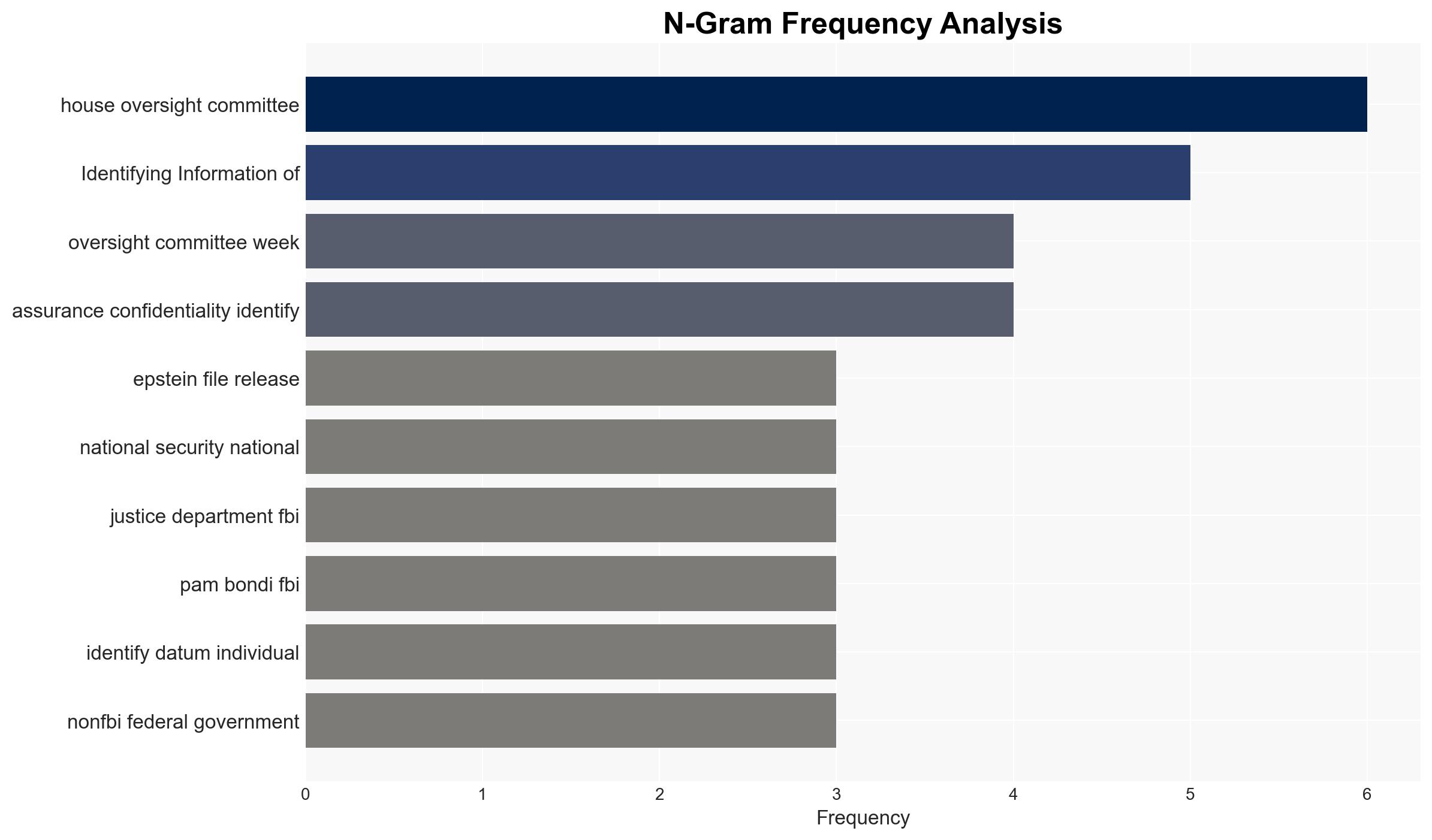
Pam Bondi, Kash Patel, Ro Khanna, Thomas Massie, Michael Tracey, Dan Novack
7. Thematic Tags
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Expose and correct potential biases in assessments through red-teaming and structured challenge.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map relationships between state and non-state actors for impact estimation.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us