Bragar Eagel & Squire Investigates Rockrose Development LLC Following Major Data Breach Incident
Published on: 2026-01-27
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: ROCKROSE DEVELOPMENT ALERT Bragar Eagel Squire PC is Investigating the Rockrose Development LLC Data Breach
1. BLUF (Bottom Line Up Front)
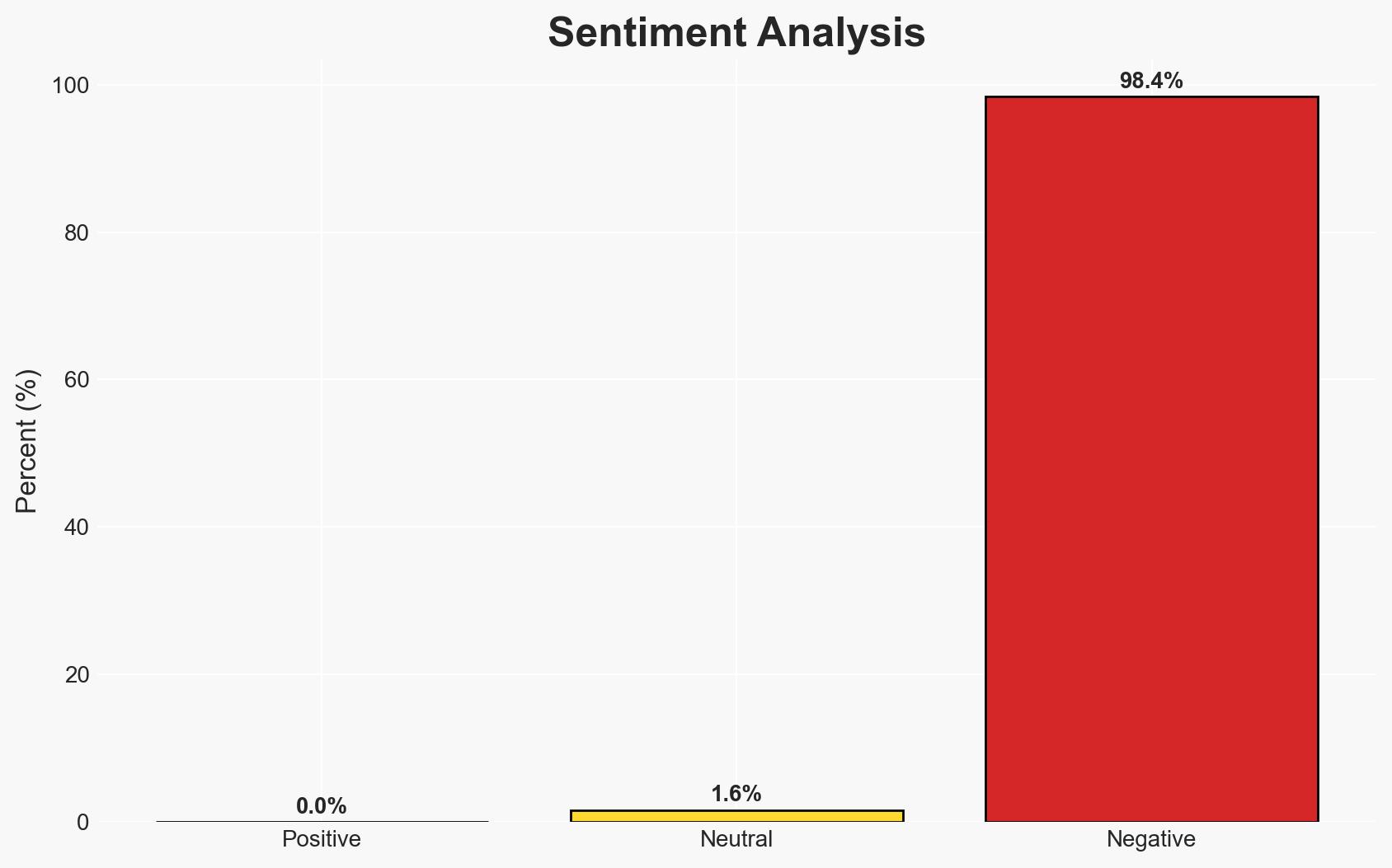
The Rockrose Development LLC data breach has exposed sensitive personal and financial information of numerous individuals, potentially leading to significant legal and financial repercussions. The investigation is ongoing, with Bragar Eagel & Squire, P.C. actively pursuing claims on behalf of affected parties. The most likely hypothesis is that the breach resulted from a targeted cyber attack, with moderate confidence due to limited available details on the attack vector and threat actors.
2. Competing Hypotheses
- Hypothesis A: The data breach was the result of a targeted cyber attack by a sophisticated threat actor. Supporting evidence includes the unauthorized access to a wide range of sensitive data. Key uncertainties involve the identity and motivations of the attackers.
- Hypothesis B: The breach was due to internal negligence or a failure in Rockrose’s cybersecurity protocols. This is supported by the lack of immediate detection and the need for third-party cybersecurity assistance. However, there is no direct evidence of internal failure at this stage.
- Assessment: Hypothesis A is currently better supported due to the nature and scope of the data accessed, which suggests a deliberate and skilled intrusion. Indicators such as the discovery of specific malware or attribution to known threat groups could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Rockrose’s cybersecurity measures were in place but insufficient; the breach was detected promptly after it occurred; the data compromised is accurate as reported.
- Information Gaps: Specific details on the attack vector, identity of the attackers, and the full extent of the data compromised are missing.
- Bias & Deception Risks: Potential bias in reporting by Bragar Eagel & Squire, P.C. due to their vested interest in litigation outcomes; no clear indicators of deception from Rockrose at this time.
4. Implications and Strategic Risks
The breach could lead to increased regulatory scrutiny and financial liabilities for Rockrose, impacting its operational stability. It may also serve as a catalyst for broader cybersecurity reforms within the industry.
- Political / Geopolitical: Minimal direct geopolitical impact, but potential for increased regulatory actions in data protection.
- Security / Counter-Terrorism: No immediate counter-terrorism implications, but highlights vulnerabilities in corporate cybersecurity.
- Cyber / Information Space: Potential for increased cyber threat activity targeting similar entities; may influence future cybersecurity policy and investment.
- Economic / Social: Possible financial losses for affected individuals and reputational damage to Rockrose, affecting consumer trust and market position.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor for further disclosures from Rockrose and Bragar Eagel & Squire; enhance cybersecurity measures and incident response protocols.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms; invest in employee training and advanced threat detection technologies.
- Scenario Outlook:
- Best: Breach contained with minimal impact, leading to improved cybersecurity practices.
- Worst: Further breaches occur, resulting in significant financial and reputational damage.
- Most-Likely: Legal proceedings lead to settlements, with moderate impact on Rockrose’s operations and reputation.
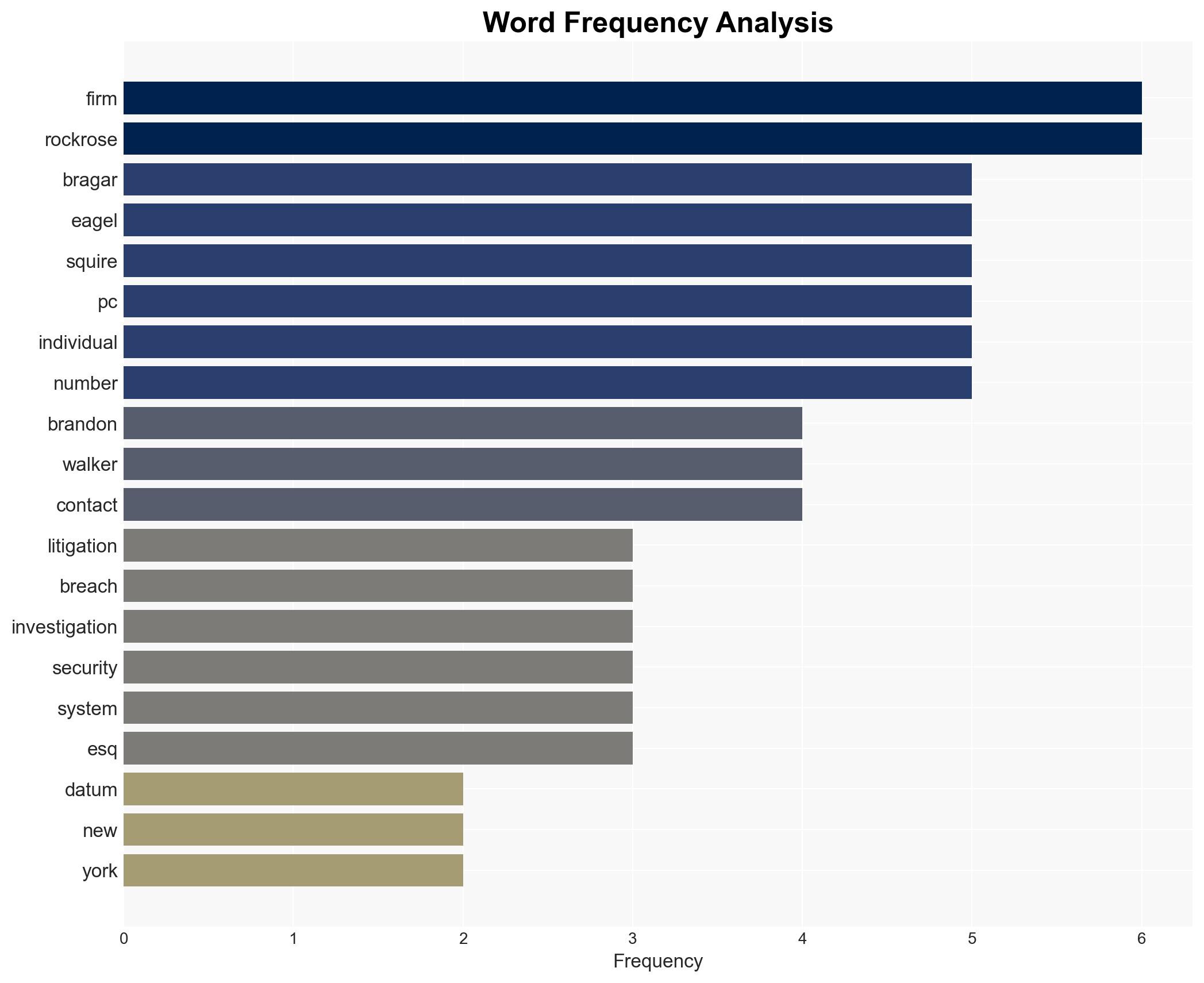
6. Key Individuals and Entities
- Bragar Eagel & Squire, P.C.
- Brandon Walker, Esq.
- Casey DeReus, Esq.
- Rockrose Development LLC
7. Thematic Tags
cybersecurity, data breach, legal action, personal data protection, corporate security, cyber threat, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us