BreachForums Database Leak Exposes Cybercriminal Identities and User Data
Published on: 2026-01-12
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: BreachForums Database Leak Turns the Tables on Threat Actors
1. BLUF (Bottom Line Up Front)
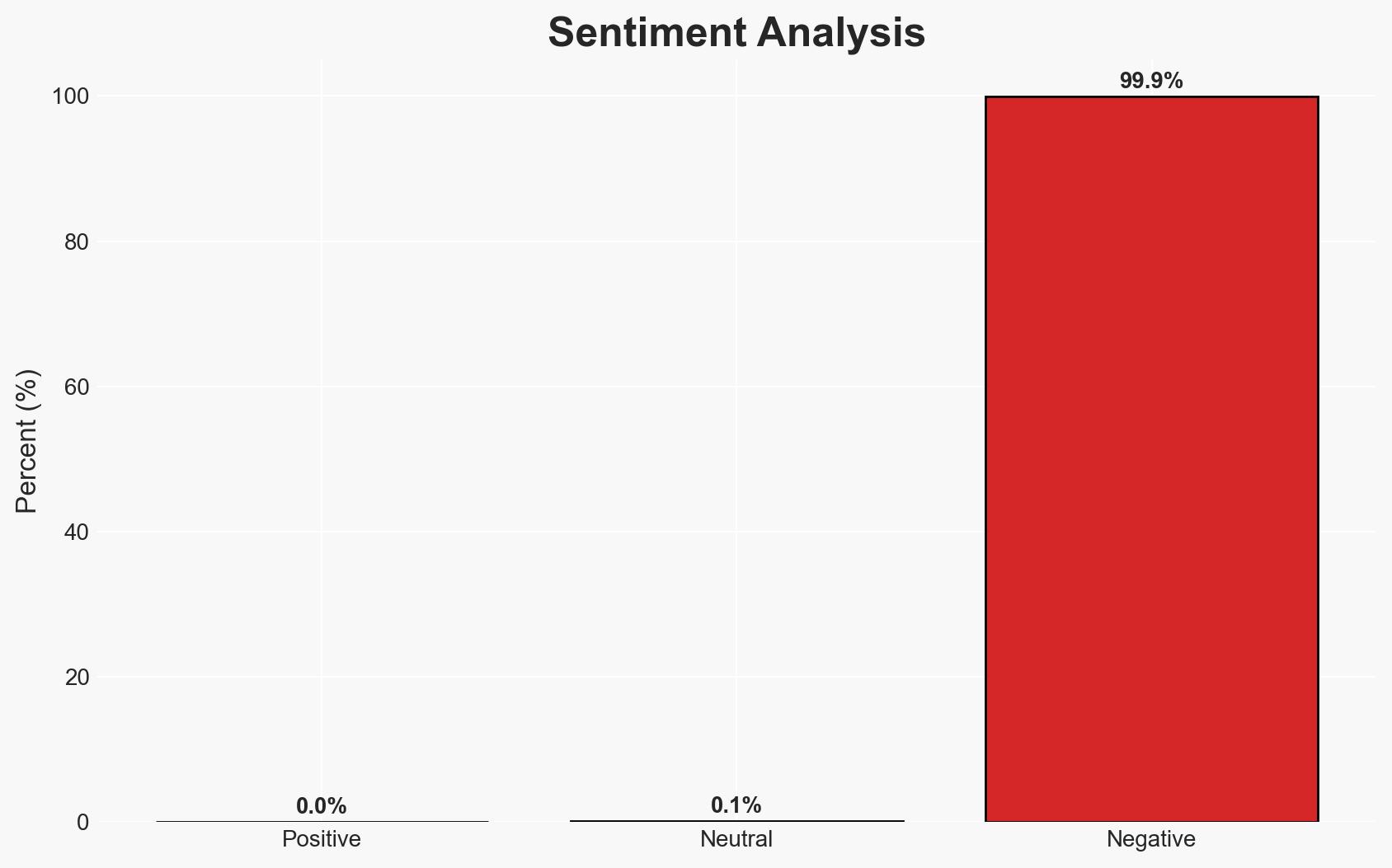
The recent leak of the BreachForums database potentially exposes the identities of cybercriminals using the platform, impacting both the threat actors and law enforcement efforts. The most likely hypothesis is that the leak was executed by a former insider with personal motivations. This development could significantly alter the threat landscape, with moderate confidence in the assessment due to uncertainties about the data’s authenticity and the leaker’s intentions.
2. Competing Hypotheses
- Hypothesis A: The database leak was orchestrated by a former insider of BreachForums, possibly “James,” motivated by personal grievances. This is supported by the manifesto and the naming of specific individuals. However, the authenticity of the data and the leaker’s true identity remain uncertain.
- Hypothesis B: The leak is a deliberate misinformation campaign by external actors aiming to destabilize BreachForums and sow distrust among its users. The presence of altered and non-existent information in the database supports this, but the insider knowledge reflected in the manifesto contradicts it.
- Assessment: Hypothesis A is currently better supported due to the detailed insider knowledge and personal tone of the manifesto. Key indicators that could shift this judgment include verified cross-referencing of the leaked data with known threat actors and further insights into the leaker’s identity and motivations.
3. Key Assumptions and Red Flags
- Assumptions: The data in the leak is partially authentic; the leaker has insider knowledge; BreachForums users will react to the leak.
- Information Gaps: The full extent of the data’s authenticity and the leaker’s identity and motivations are unknown.
- Bias & Deception Risks: Potential bias from Resecurity’s interpretation of the data; possible deception by the leaker to manipulate perceptions of BreachForums’ security.
4. Implications and Strategic Risks
This leak could lead to increased law enforcement scrutiny and potential arrests, altering the operational environment for cybercriminals. It may also prompt a shift in how dark web forums operate, with increased security measures or fragmentation.
- Political / Geopolitical: Increased international cooperation on cybercrime could be catalyzed by this leak.
- Security / Counter-Terrorism: Potential disruption of cybercriminal networks and operations.
- Cyber / Information Space: Enhanced security measures on similar platforms; potential for misinformation campaigns.
- Economic / Social: Minimal direct economic impact; potential social impact on the perception of dark web security.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor BreachForums and similar platforms for changes in user behavior; verify the authenticity of leaked data.
- Medium-Term Posture (1–12 months): Strengthen partnerships with cybersecurity firms for data analysis; develop capabilities to counter misinformation.
- Scenario Outlook:
- Best: Law enforcement uses the data to dismantle criminal networks.
- Worst: The leak is a misinformation campaign, leading to distrust in legitimate cybersecurity efforts.
- Most-Likely: Partial disruption of BreachForums with increased security measures implemented by similar platforms.
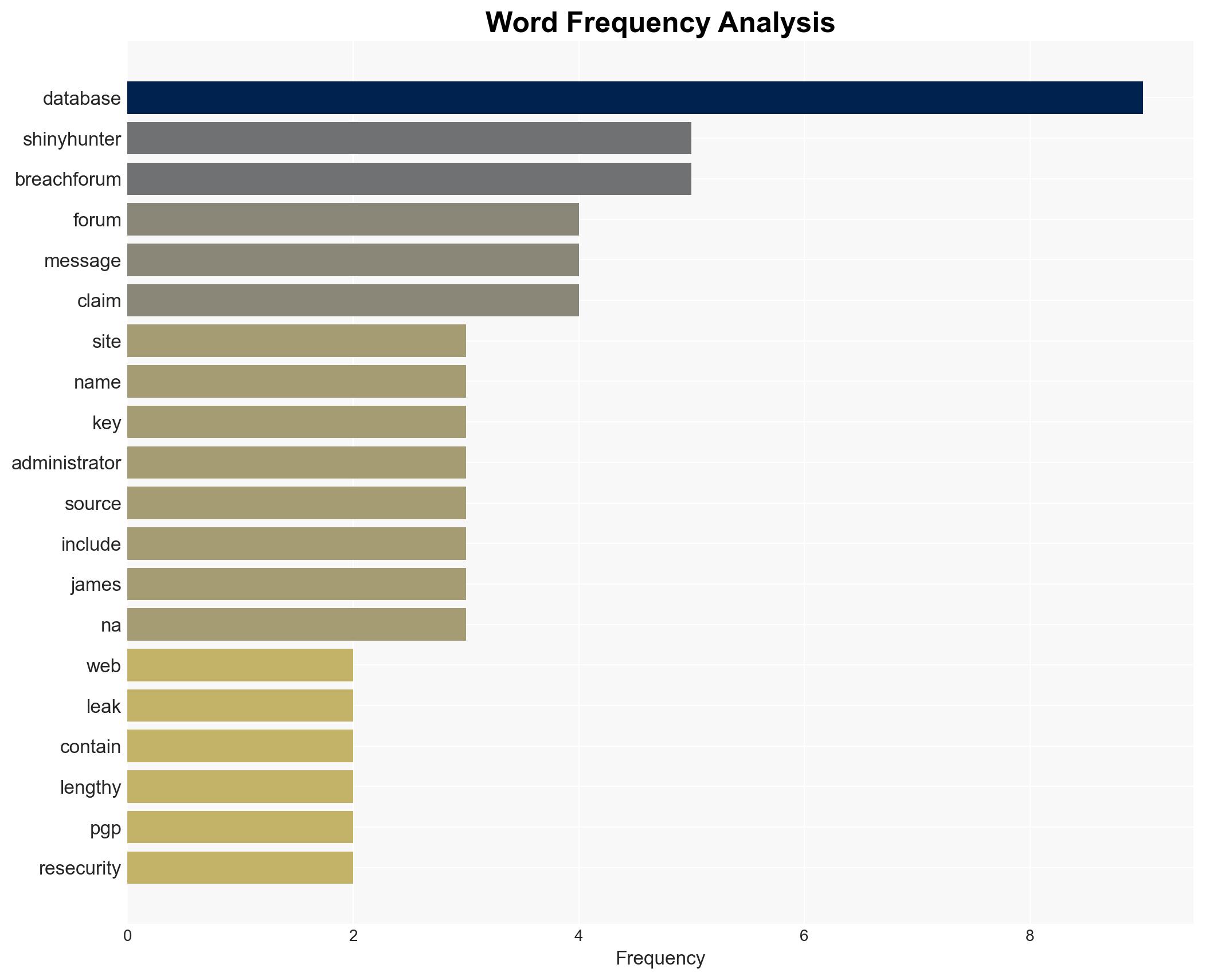
6. Key Individuals and Entities
- James (Mathis) – Alleged leaker
- ShinyHunters – Hacking collective
- BreachForums – Dark web forum
- Resecurity – Security firm analyzing the leak
- N/A – Current administrator of BreachForums
7. Thematic Tags
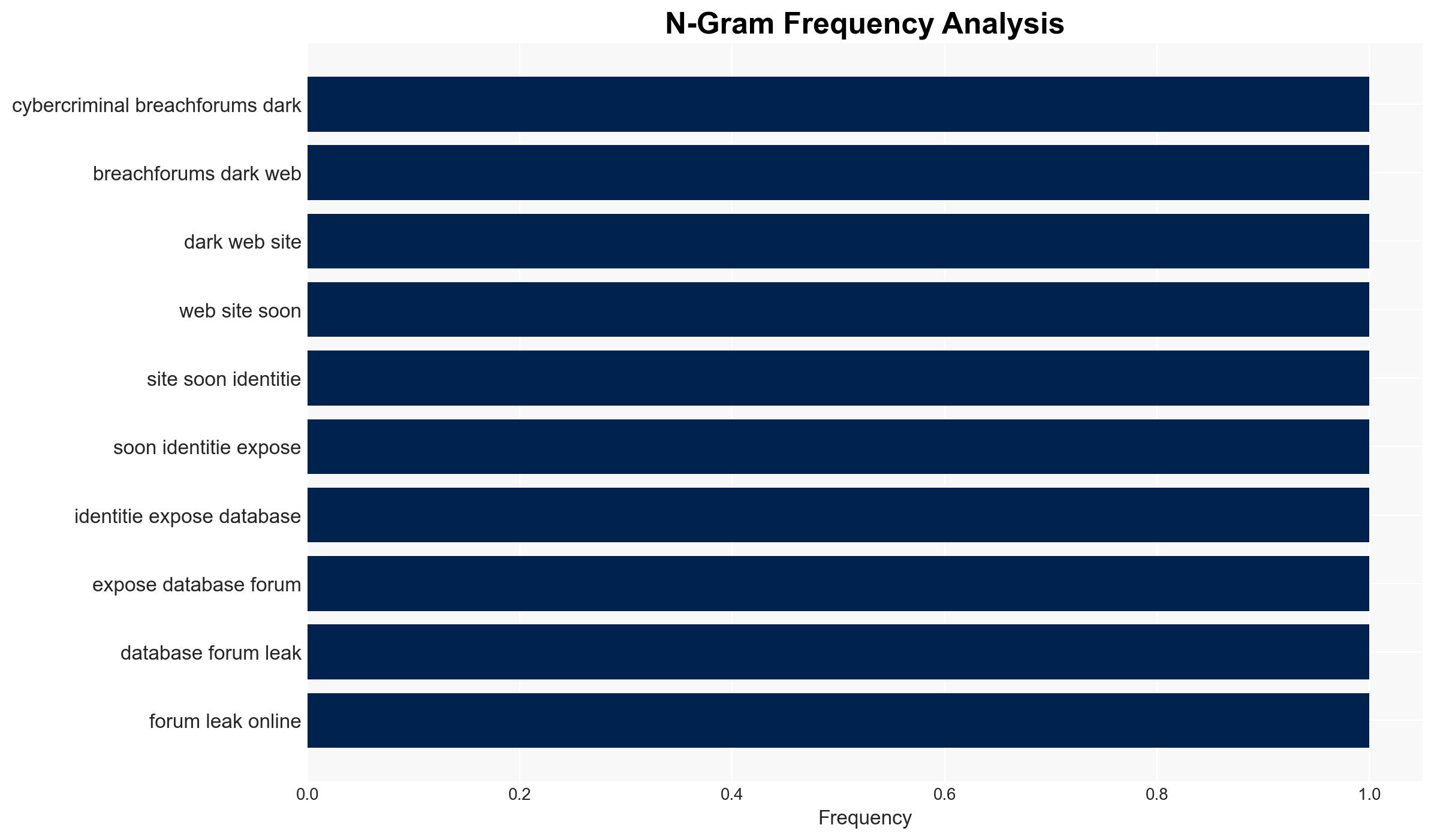
cybersecurity, dark web, data breach, cybercrime, misinformation, law enforcement, insider threat
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us