Bridgestone Confirms Cyberattack Disrupting North American Plants – HackRead
Published on: 2025-09-05
Intelligence Report: Bridgestone Confirms Cyberattack Disrupting North American Plants – HackRead
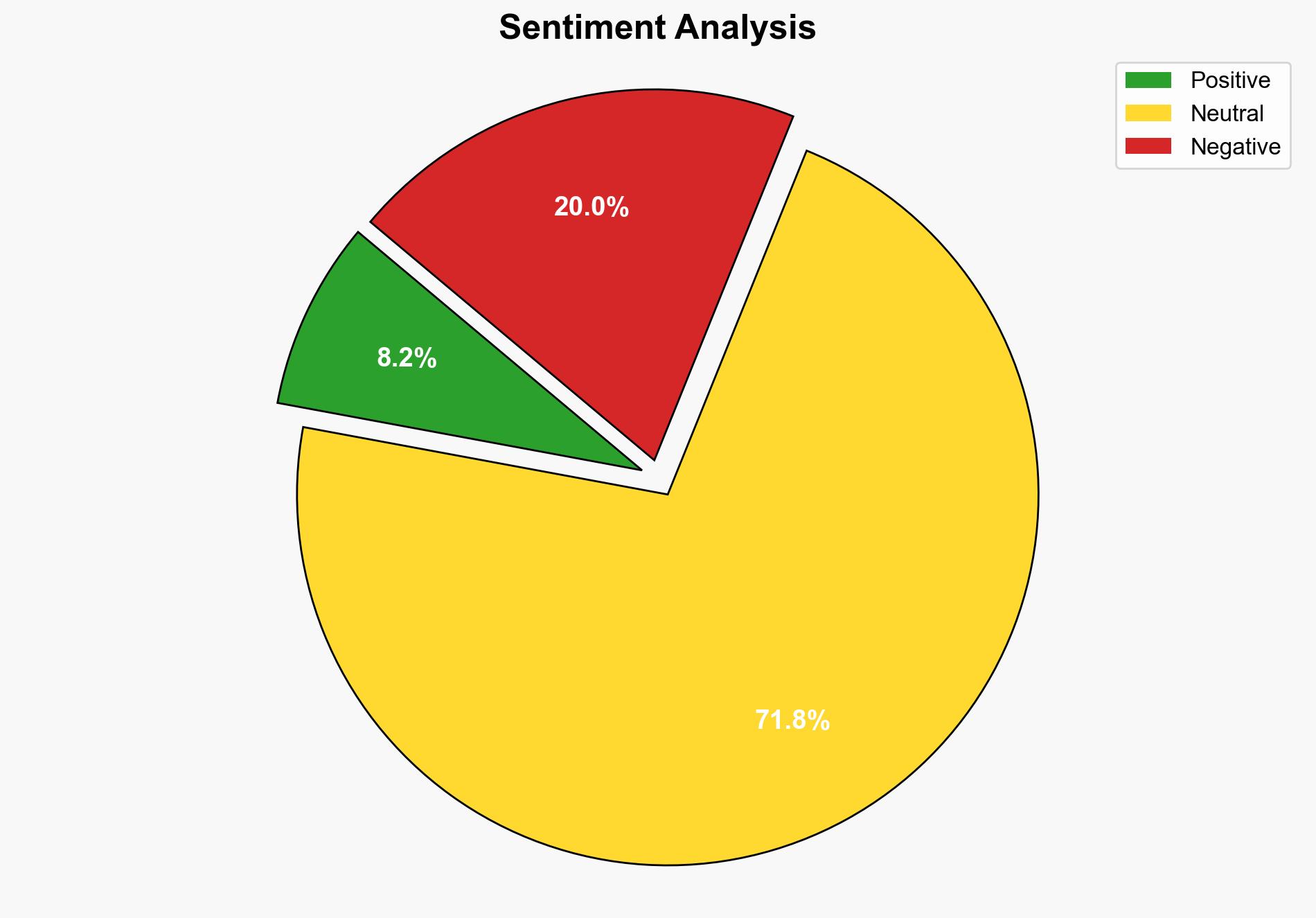
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that the cyberattack on Bridgestone’s North American plants was conducted by a sophisticated hacking group, potentially Scatter Lapsus Hunter, aiming to disrupt operations and possibly extort the company. Confidence level is moderate due to the lack of direct attribution. Recommended action includes enhancing cybersecurity measures and conducting a thorough forensic analysis to prevent future incidents.
2. Competing Hypotheses
1. **Hypothesis A**: The cyberattack was orchestrated by Scatter Lapsus Hunter, a known hacking group, to disrupt Bridgestone’s operations and potentially extort the company.
2. **Hypothesis B**: The cyberattack was a random, opportunistic attack by an unaffiliated hacker or group, exploiting vulnerabilities without a specific target in mind.
Using ACH 2.0, Hypothesis A is better supported due to the recent activity of Scatter Lapsus Hunter and their history of targeting major companies. Hypothesis B lacks specific indicators linking it to opportunistic behavior.
3. Key Assumptions and Red Flags
– **Assumptions**: It is assumed that the attack’s timing and method align with Scatter Lapsus Hunter’s known tactics. There is also an assumption that Bridgestone’s cybersecurity measures were inadequate.
– **Red Flags**: The lack of confirmed attribution and the possibility of other groups using Scatter Lapsus Hunter’s name to mislead investigators.
– **Blind Spots**: Potential internal vulnerabilities or insider threats within Bridgestone that have not been disclosed.
4. Implications and Strategic Risks
The attack highlights vulnerabilities in the manufacturing sector’s cybersecurity, potentially encouraging further attacks. There is a risk of supply chain disruptions affecting Bridgestone’s operations and broader economic impacts. Geopolitically, this could strain trade relations if linked to state-sponsored actors. Psychologically, it may erode trust in Bridgestone’s ability to protect its data and operations.
5. Recommendations and Outlook
- Enhance cybersecurity infrastructure and conduct regular penetration testing.
- Implement a comprehensive incident response plan and employee training to mitigate social engineering risks.
- Best-case scenario: Strengthened defenses deter future attacks. Worst-case scenario: Continued attacks lead to significant operational and financial losses. Most likely scenario: Bridgestone improves security but faces ongoing threats.
6. Key Individuals and Entities
– Pierre Luc Bellerose (Joliette Mayor)
– Scatter Lapsus Hunter (Hacking Group)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus