Brightspeed probes alleged data breach as hackers offer stolen customer records for sale
Published on: 2026-01-06
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Brightspeed investigates breach as crims post stolen data for sale
1. BLUF (Bottom Line Up Front)
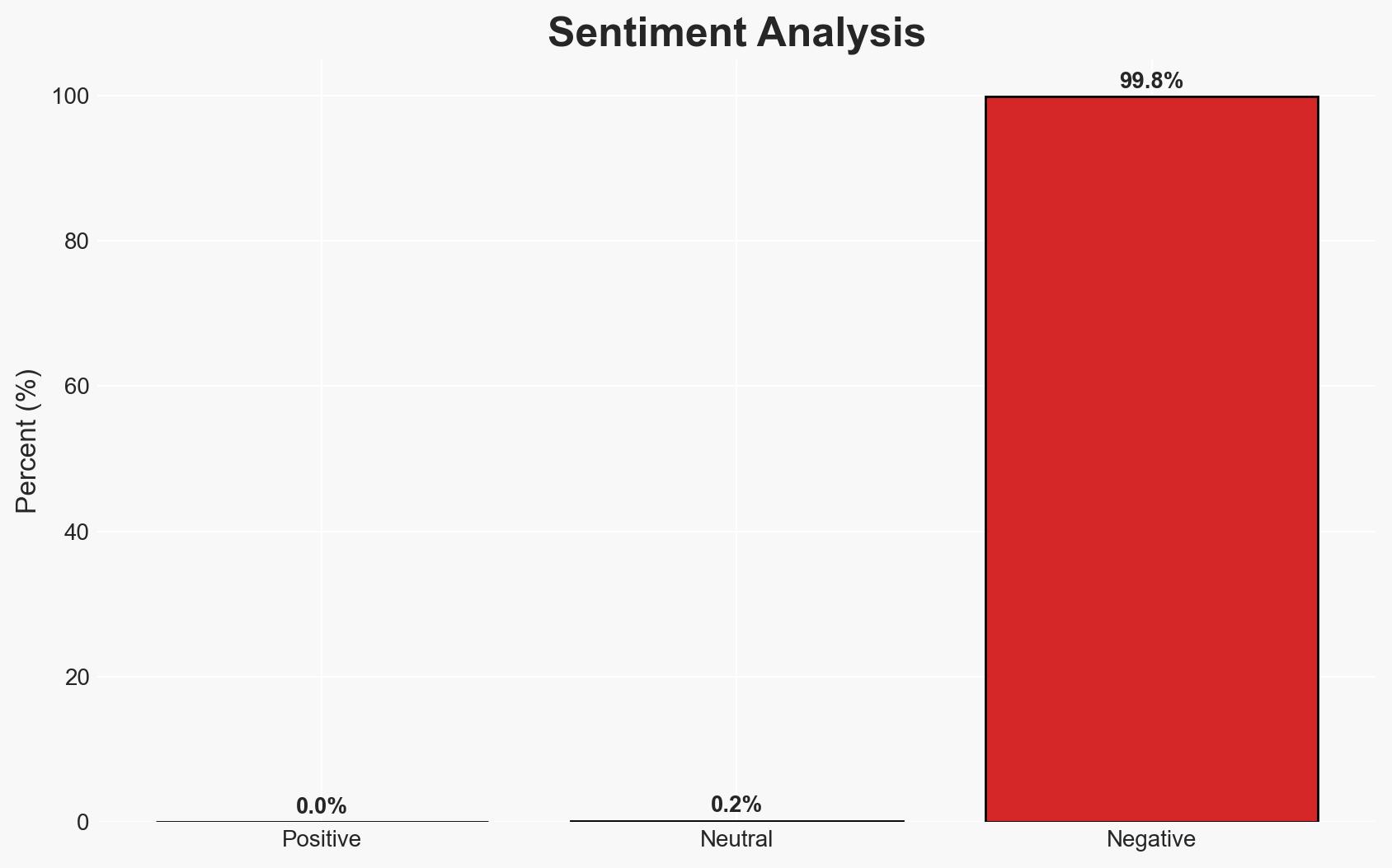
Brightspeed is investigating claims by the Crimson Collective that they have stolen over a million customer records and are selling them for three bitcoin. This incident potentially affects Brightspeed’s customers, employees, and its operational integrity. The most likely hypothesis is that the breach occurred as described, but the extent and impact remain uncertain. Overall confidence in this assessment is moderate due to limited verification of claims.
2. Competing Hypotheses
- Hypothesis A: The Crimson Collective successfully breached Brightspeed’s systems, exfiltrating customer data as claimed. This is supported by the group’s history of similar activities and the publication of sample data. However, the method of access and the full scope of data compromised remain unclear.
- Hypothesis B: The claims by Crimson Collective are exaggerated or fabricated to extort Brightspeed. This is supported by the lack of independent verification of the breach and the group’s potential motive to inflate their capabilities for financial gain.
- Assessment: Hypothesis A is currently better supported due to the group’s previous successful breaches and the release of sample data. Indicators that could shift this judgment include independent verification of the breach or evidence of false claims by the group.
3. Key Assumptions and Red Flags
- Assumptions: Brightspeed’s network security measures were insufficient to prevent the breach; Crimson Collective possesses the technical capability to execute such attacks; the data samples released are genuine.
- Information Gaps: Verification of the breach’s extent and method; confirmation of the authenticity of the released data; Brightspeed’s internal security response details.
- Bias & Deception Risks: Potential bias from Crimson Collective to exaggerate claims for financial gain; possible underreporting by Brightspeed to minimize reputational damage.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of Brightspeed’s cybersecurity practices and potential regulatory actions. The breach may embolden other cybercriminal groups to target similar companies.
- Political / Geopolitical: Potential for increased regulatory oversight and international cooperation on cybersecurity standards.
- Security / Counter-Terrorism: Heightened threat environment for ISPs and potential targeting by other cybercriminal groups.
- Cyber / Information Space: Possible increase in cyber extortion attempts and data breaches in the sector.
- Economic / Social: Potential financial losses for Brightspeed and erosion of customer trust, impacting market position and customer retention.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of Brightspeed’s network for further breaches, engage with cybersecurity experts for incident response, and communicate transparently with stakeholders.
- Medium-Term Posture (1–12 months): Develop resilience measures, strengthen partnerships with cybersecurity firms, and invest in advanced threat detection capabilities.
- Scenario Outlook:
- Best: Breach is contained with minimal data exposure, leading to improved security measures.
- Worst: Data is widely disseminated, causing significant financial and reputational damage.
- Most-Likely: Partial data exposure with moderate impact, prompting regulatory and security enhancements.
6. Key Individuals and Entities
- Brightspeed
- Crimson Collective
- Gene Rodriguez Miller (Brightspeed spokesperson)
- ShinyHunters-linked Scattered Lapsus$ Hunters
7. Thematic Tags
cybersecurity, data breach, cyber extortion, ISP security, cybercrime, information security, regulatory implications
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us