Call-On-Doc faces potential data breach impacting over 1 million patient records, remains silent on incident
Published on: 2026-01-24
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Call-On-Doc allegedly had a breach affecting more than 1 million patients They’ve yet to comment
1. BLUF (Bottom Line Up Front)
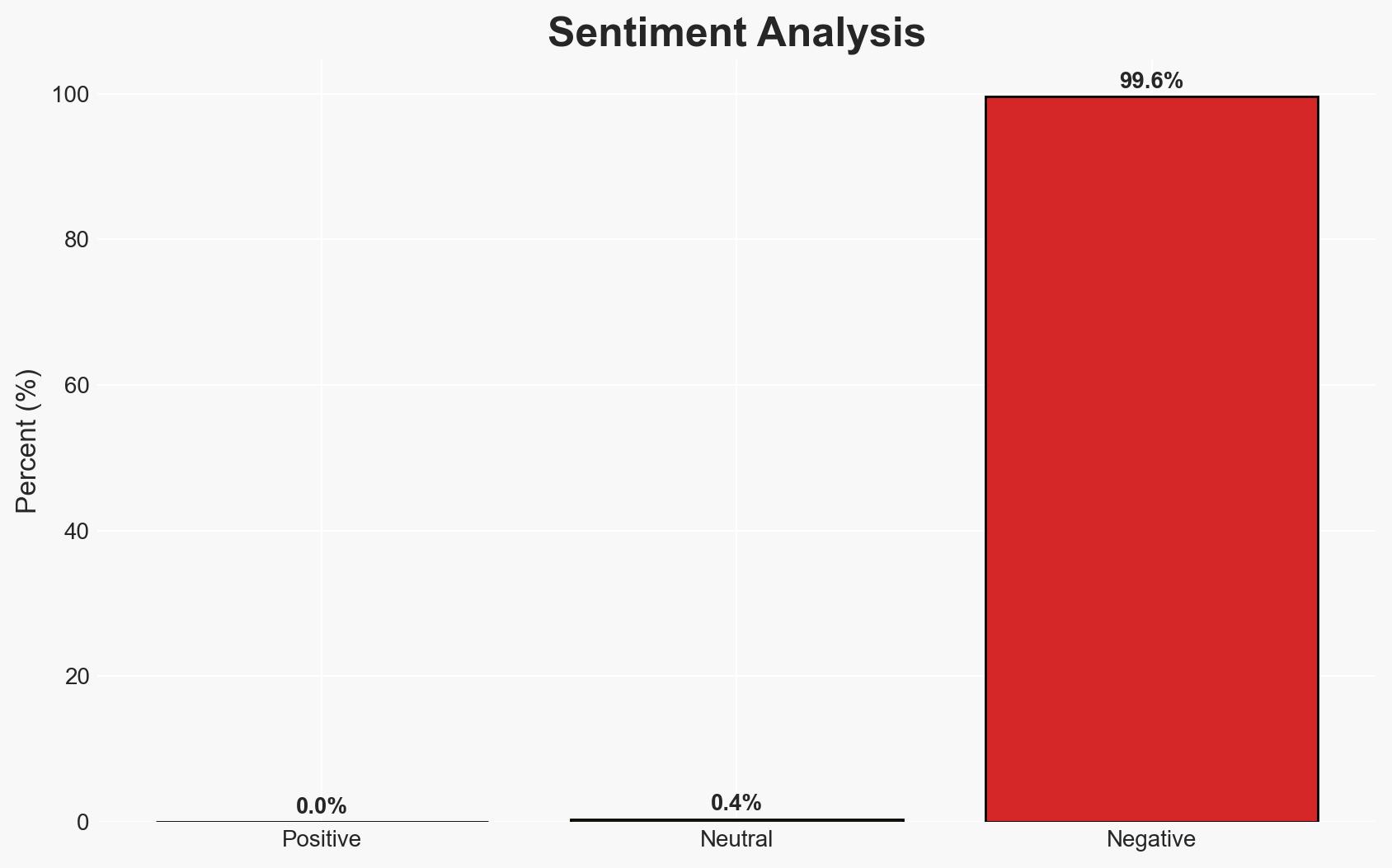
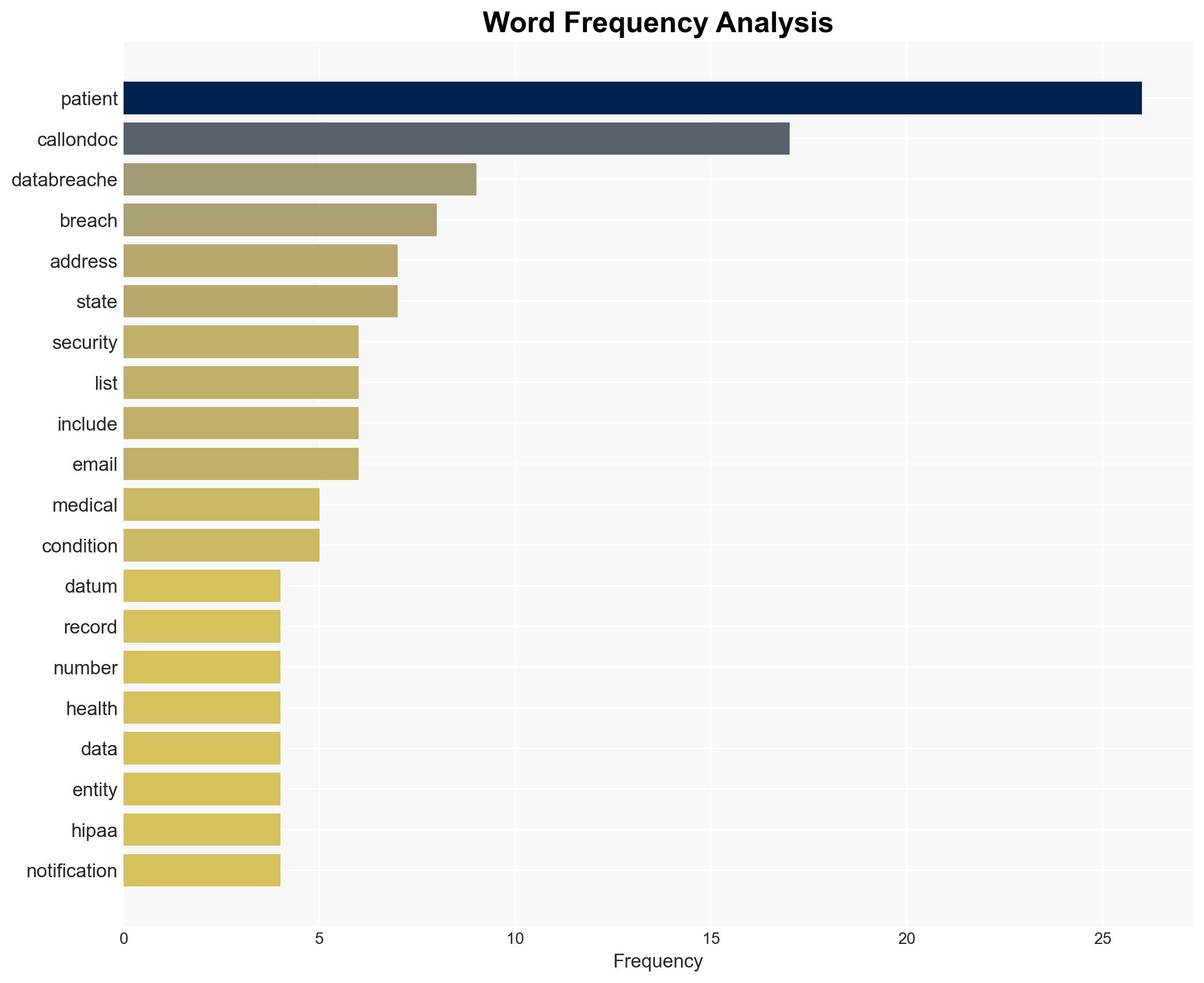
A significant data breach reportedly affecting over 1 million patients of Call-On-Doc, a telehealth provider, has been alleged on a hacking forum. The breach potentially exposes sensitive patient information, including medical conditions and contact details. The most likely hypothesis is that the breach occurred due to inadequate security measures, contradicting the company’s claims of “state-of-the-art” data security. This assessment is made with moderate confidence due to the lack of direct confirmation from Call-On-Doc.
2. Competing Hypotheses
- Hypothesis A: The breach occurred due to inadequate security measures at Call-On-Doc, as suggested by the lack of encryption and failure to detect the breach in progress. Supporting evidence includes the threat actor’s claims and the screenshots of patient data. Key uncertainties include the actual security measures in place and the company’s response.
- Hypothesis B: The breach claim is exaggerated or fabricated by the threat actor to inflate the value of the data on the hacking forum. Contradicting evidence includes the absence of a public statement from Call-On-Doc and the potential for deception in the hacking community.
- Assessment: Hypothesis A is currently better supported due to the detailed nature of the data presented and the lack of immediate denial from Call-On-Doc. Indicators that could shift this judgment include a formal statement from Call-On-Doc or independent verification of the data’s authenticity.
3. Key Assumptions and Red Flags
- Assumptions: Call-On-Doc’s security measures are insufficient; the data breach claim is genuine; the threat actor has access to the data they claim.
- Information Gaps: Confirmation of the breach from Call-On-Doc; details on the security measures in place; independent verification of the data’s authenticity.
- Bias & Deception Risks: Potential bias from the hacking forum’s commercial interests; deception by the threat actor to inflate data value; cognitive bias in assuming breach validity without confirmation.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of telehealth providers’ data security practices and regulatory actions. It may also impact patient trust in telehealth services.
- Political / Geopolitical: Potential for increased regulatory oversight and policy changes regarding telehealth data security.
- Security / Counter-Terrorism: No direct implications, but highlights vulnerabilities in healthcare data security that could be exploited.
- Cyber / Information Space: Increased risk of cyber-attacks on telehealth providers; potential for misinformation if the breach details are manipulated.
- Economic / Social: Potential financial impact on Call-On-Doc; erosion of patient trust in telehealth services could affect market dynamics.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor for an official response from Call-On-Doc; engage with cybersecurity experts to assess the breach’s scope; enhance monitoring of hacking forums for further developments.
- Medium-Term Posture (1–12 months): Strengthen partnerships with cybersecurity firms; develop resilience measures for telehealth data protection; advocate for clearer regulatory guidelines.
- Scenario Outlook:
- Best: Call-On-Doc confirms breach is false, restoring trust (trigger: official statement).
- Worst: Breach confirmed, leading to regulatory penalties and loss of patient trust (trigger: independent verification).
- Most-Likely: Breach confirmed, prompting regulatory review and security enhancements (trigger: Call-On-Doc acknowledgment).
6. Key Individuals and Entities
- Call-On-Doc, Inc.
- Federal Trade Commission (FTC)
- Unidentified threat actor (hacking forum)
- Patients of Call-On-Doc (potentially affected)
7. Thematic Tags
cybersecurity, data breach, telehealth, patient privacy, regulatory compliance, information security, healthcare
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us