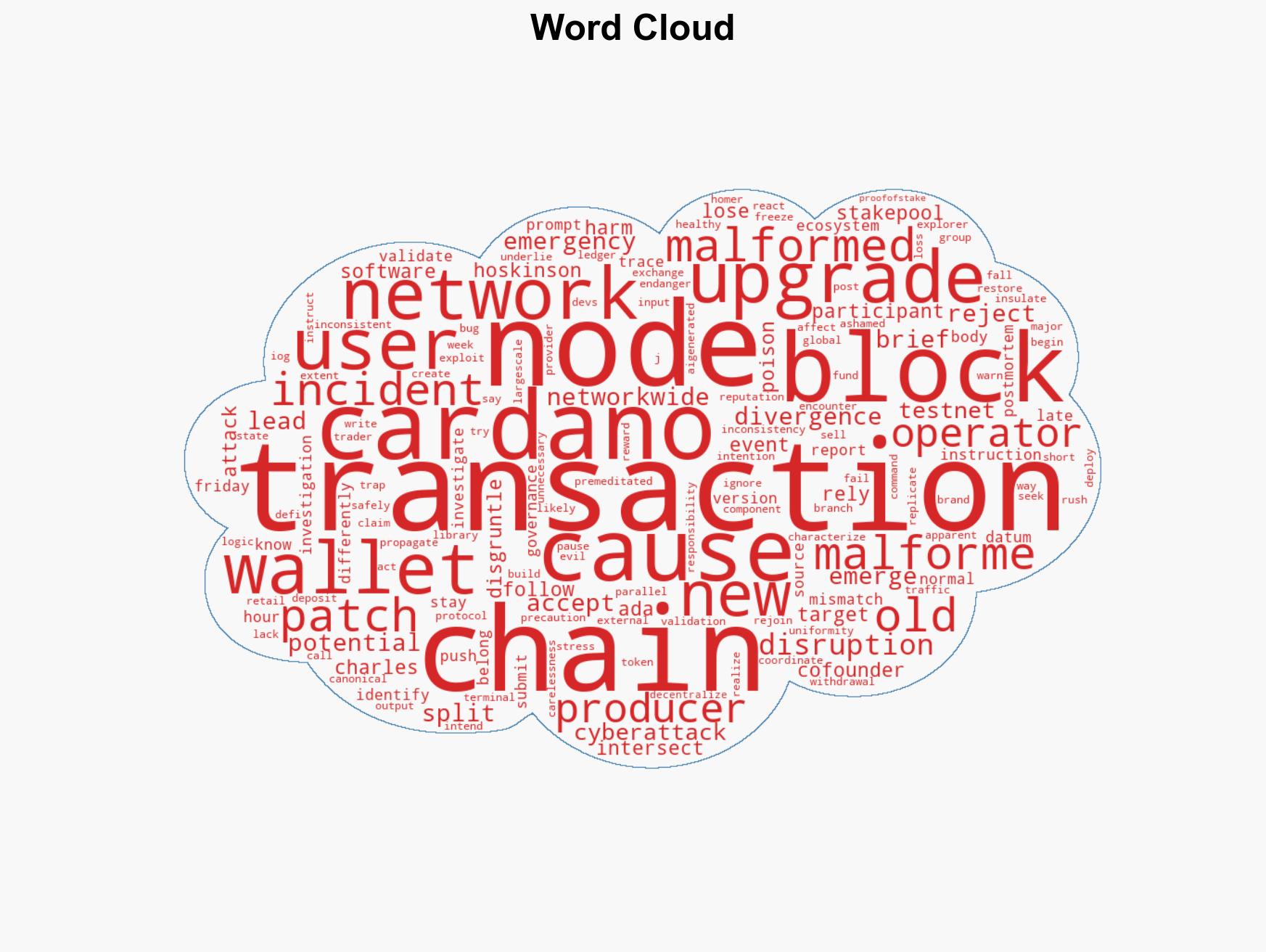
Cardano Faces Temporary Chain Split Due to Exploit of Known Bug, Prompting Emergency Network Upgrade
Published on: 2025-12-04
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Cardano Temporarily Splits Into Two Chains as Attacker Claims to Use Possible AI-Generated Script to Exploit a Known Bug
1. BLUF (Bottom Line Up Front)
The Cardano blockchain experienced a temporary split due to a malformed transaction, potentially caused by a disgruntled former testnet participant using AI-generated scripts. This incident highlights vulnerabilities in blockchain validation processes and could have long-term reputational impacts on Cardano. The most likely hypothesis is that this was an opportunistic attack rather than a coordinated effort, with moderate confidence in this assessment.
2. Competing Hypotheses
- Hypothesis A: The incident was a targeted attack by a disgruntled stake-pool operator using AI-generated scripts to exploit a known bug. Supporting evidence includes the identification of a former testnet participant’s wallet and the claim of responsibility by an individual. However, the lack of financial gain or broader coordination contradicts this hypothesis.
- Hypothesis B: The incident was an accidental disruption caused by an individual experimenting with network vulnerabilities without malicious intent. This is supported by the individual’s claim of carelessness and lack of financial motive. Contradicting evidence includes the deliberate nature of exploiting a known bug.
- Assessment: Hypothesis B is currently better supported due to the individual’s admission of carelessness and lack of intent to cause harm. However, further investigation into the individual’s background and potential motives could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The attacker acted alone; the AI-generated script was not widely distributed; the incident was not financially motivated; the network can be fully restored without further incidents.
- Information Gaps: Details on the AI-generated script’s origin and distribution; comprehensive background on the attacker; full scope of the network’s vulnerabilities.
- Bias & Deception Risks: Potential bias in attributing the attack to a disgruntled operator without full evidence; risk of deception in the attacker’s public statements.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of blockchain security protocols and influence regulatory approaches to cryptocurrency networks. It may also prompt other networks to reassess their vulnerability to similar exploits.
- Political / Geopolitical: Increased regulatory interest in blockchain security; potential for international cooperation on cybersecurity standards.
- Security / Counter-Terrorism: Highlighted need for enhanced monitoring of blockchain networks for malicious activities.
- Cyber / Information Space: Potential for increased cyberattacks on blockchain networks exploiting similar vulnerabilities.
- Economic / Social: Short-term loss of confidence in Cardano and potential impact on its market value; broader implications for investor trust in cryptocurrencies.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a thorough forensic investigation of the incident; enhance monitoring of blockchain transactions; issue security patches and updates.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms; invest in AI-driven security solutions; engage with regulators to establish security standards.
- Scenario Outlook: Best: Full network restoration and improved security measures; Worst: Recurrence of similar incidents leading to regulatory crackdowns; Most-Likely: Gradual restoration of network confidence with ongoing security enhancements.
6. Key Individuals and Entities
- Charles Hoskinson, Cardano co-founder
- Intersect, Cardano ecosystem governance body
- Input Output Global (IOG), Cardano’s parent company
- Homer J., self-identified attacker
7. Thematic Tags
Cybersecurity, blockchain security, cyberattack, cryptocurrency, AI-generated scripts, network vulnerability, Cardano, regulatory implications
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us