CERT-FR advises disabling Wi-Fi on mobile devices to mitigate cybersecurity risks and vulnerabilities
Published on: 2025-12-15
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: CERT-FR recommends completely deactivate Wi-Fi whenever its not in use
1. BLUF (Bottom Line Up Front)
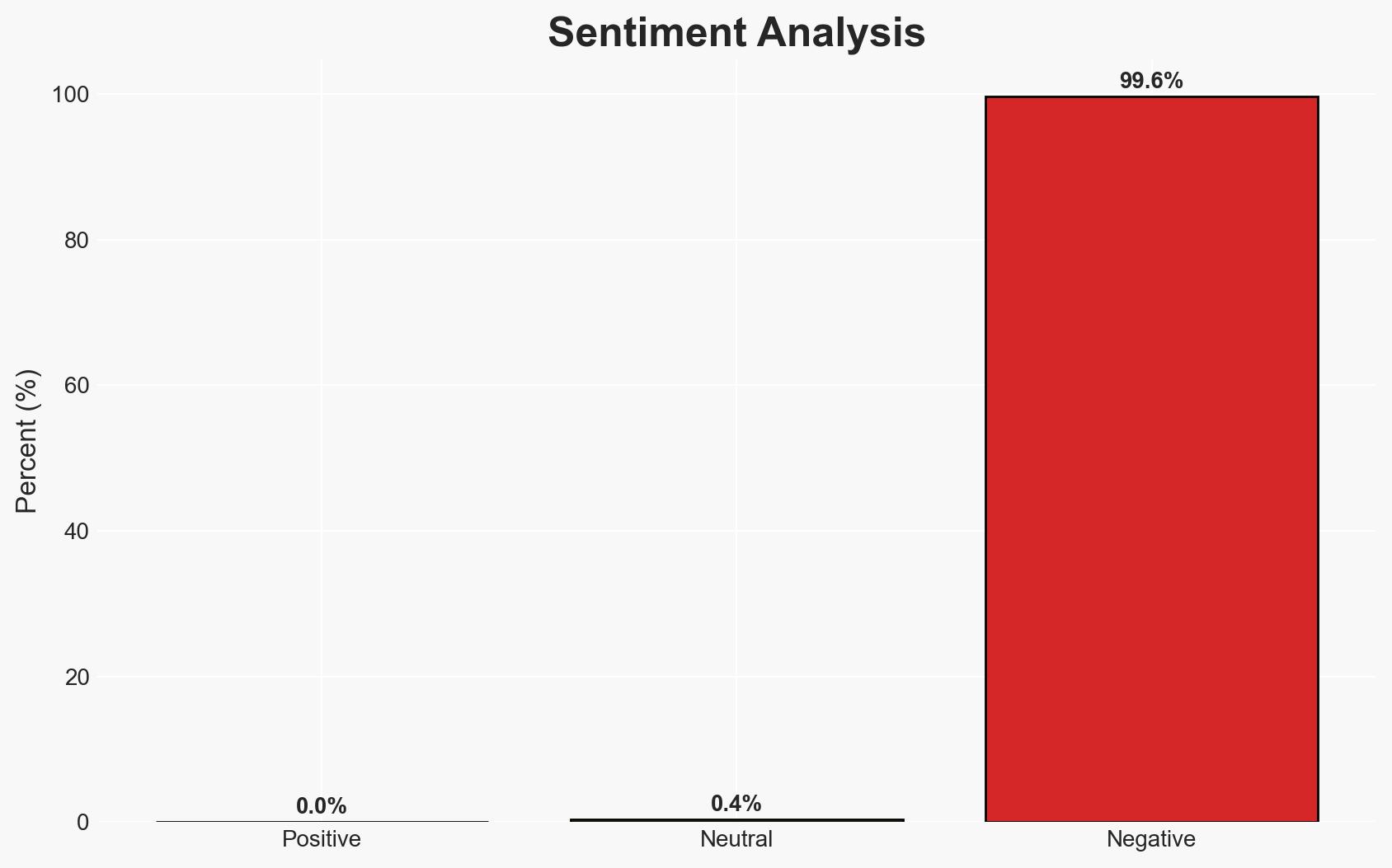
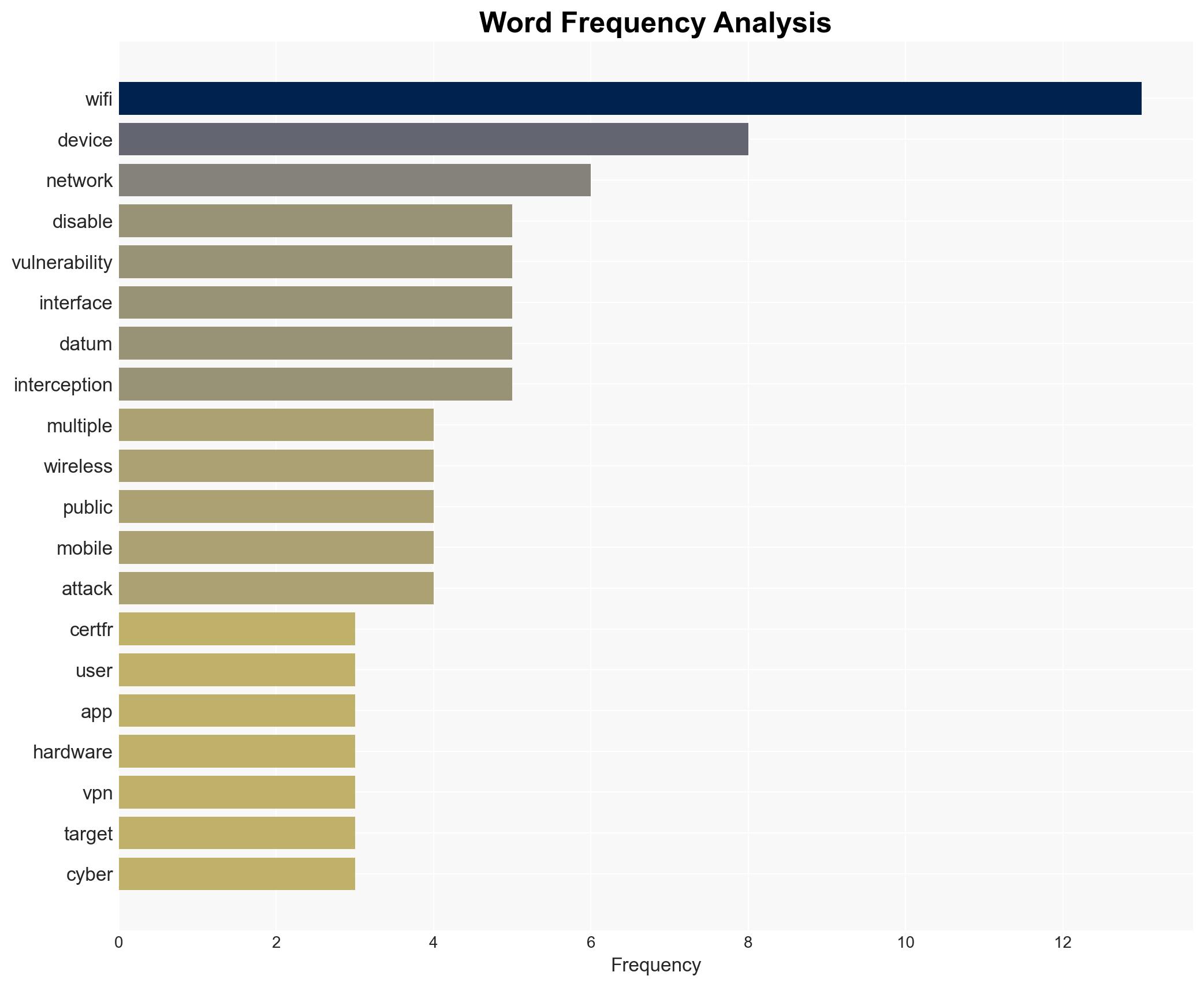
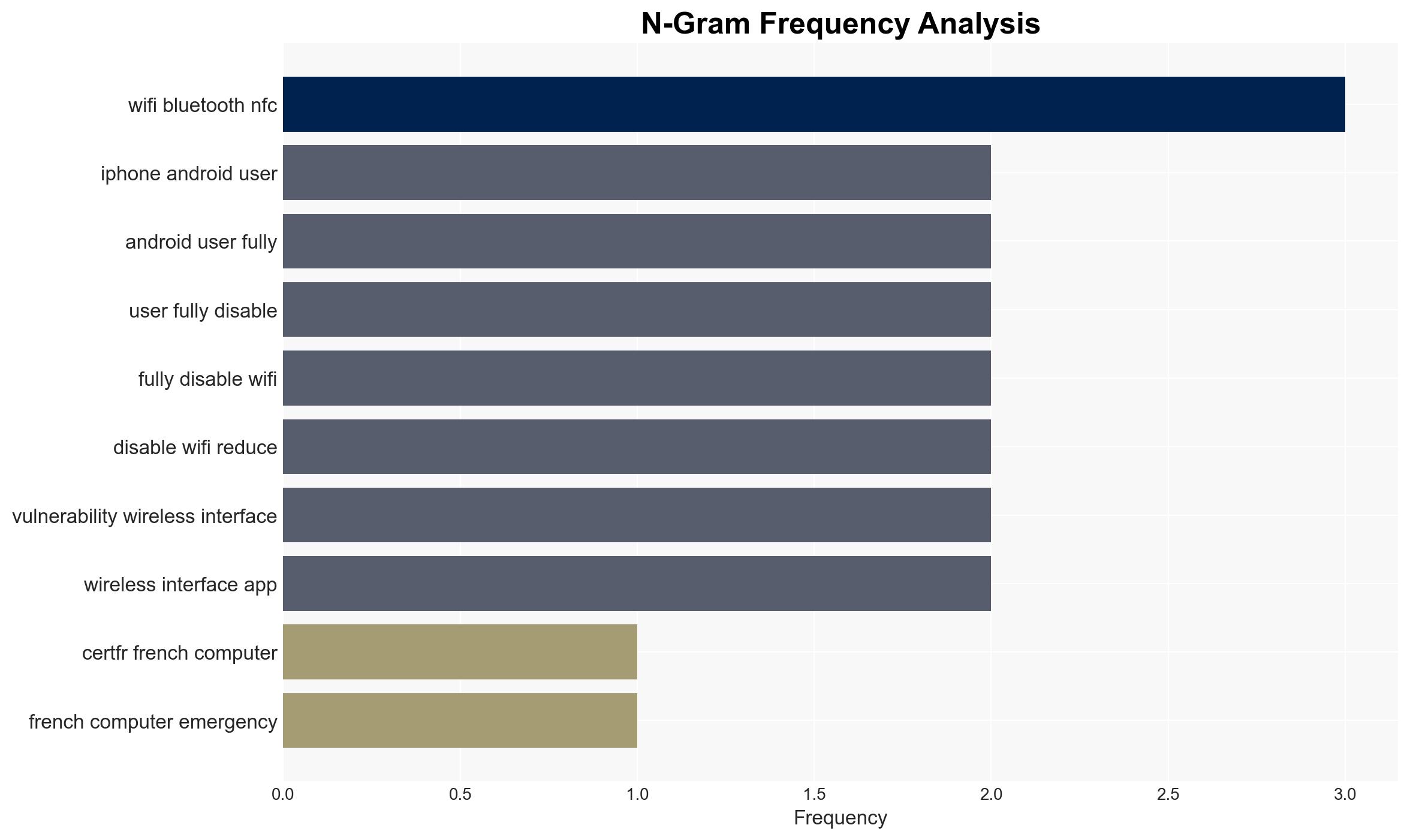
The CERT-FR advises disabling Wi-Fi on smartphones to mitigate vulnerabilities exploited by state-sponsored and private sector offensive actors. This recommendation targets iPhone and Android users, emphasizing the significant attack surface of mobile devices. The assessment is made with moderate confidence, given the broad acknowledgment of these vulnerabilities but limited specific incident data.
2. Competing Hypotheses
- Hypothesis A: CERT-FR’s recommendation is based on credible intelligence of increased exploitation of Wi-Fi vulnerabilities by malicious actors. Supporting evidence includes the report’s emphasis on known vulnerabilities and past incidents of exploitation. However, the lack of specific recent incidents or threat actor attribution introduces uncertainty.
- Hypothesis B: The recommendation is a precautionary measure rather than a response to a specific threat increase. This is supported by the general nature of the advice and the absence of new, detailed threat intelligence in the report. Contradicting evidence is the report’s focus on state-sponsored and PSOA activities, implying a heightened threat landscape.
- Assessment: Hypothesis A is currently better supported due to the detailed enumeration of vulnerabilities and the historical context of exploitation by sophisticated actors. Indicators that could shift this judgment include new intelligence on specific threat actor campaigns or a significant incident involving Wi-Fi vulnerabilities.
3. Key Assumptions and Red Flags
- Assumptions: Mobile device vulnerabilities are actively being exploited; CERT-FR’s recommendations are based on current threat assessments; Disabling Wi-Fi significantly reduces exposure to threats.
- Information Gaps: Specific recent incidents or campaigns exploiting Wi-Fi vulnerabilities; Detailed threat actor attribution; Data on the effectiveness of the recommended mitigations.
- Bias & Deception Risks: Potential bias in threat assessment due to reliance on historical data; Lack of transparency in CERT-FR’s intelligence sources; Possible overestimation of threat to justify precautionary measures.
4. Implications and Strategic Risks
The recommendation to deactivate Wi-Fi could influence user behavior and device security practices, potentially reducing exposure to cyber threats. However, it may also lead to increased public concern over mobile security.
- Political / Geopolitical: Heightened awareness of mobile security may lead to increased regulatory scrutiny and international cooperation on cyber threats.
- Security / Counter-Terrorism: Enhanced security measures could complicate threat actor operations, potentially leading to shifts in tactics or target selection.
- Cyber / Information Space: Increased focus on mobile vulnerabilities may drive innovation in security solutions and exploit development.
- Economic / Social: Potential economic impact on businesses reliant on mobile connectivity and public Wi-Fi services; Social implications include increased user anxiety and demand for secure alternatives.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor for specific threat actor campaigns targeting mobile vulnerabilities; Disseminate CERT-FR’s recommendations to relevant stakeholders; Encourage public awareness initiatives on mobile security.
- Medium-Term Posture (1–12 months): Develop partnerships with mobile OS developers and telecom providers to enhance security measures; Invest in research on emerging mobile threats and mitigation strategies.
- Scenario Outlook:
- Best: Increased security awareness leads to reduced exploitation of mobile vulnerabilities.
- Worst: Threat actors adapt quickly, exploiting other vulnerabilities or increasing sophistication of attacks.
- Most-Likely: Gradual improvement in mobile security practices with ongoing challenges from evolving threats.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, mobile vulnerabilities, state-sponsored actors, public safety, information security, CERT-FR, mobile devices
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us