China-affiliated APT UNC3886 conducts cyber espionage against Singapore’s telecom industry
Published on: 2026-02-10
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: China-linked APT UNC3886 targets Singapore telcos
1. BLUF (Bottom Line Up Front)
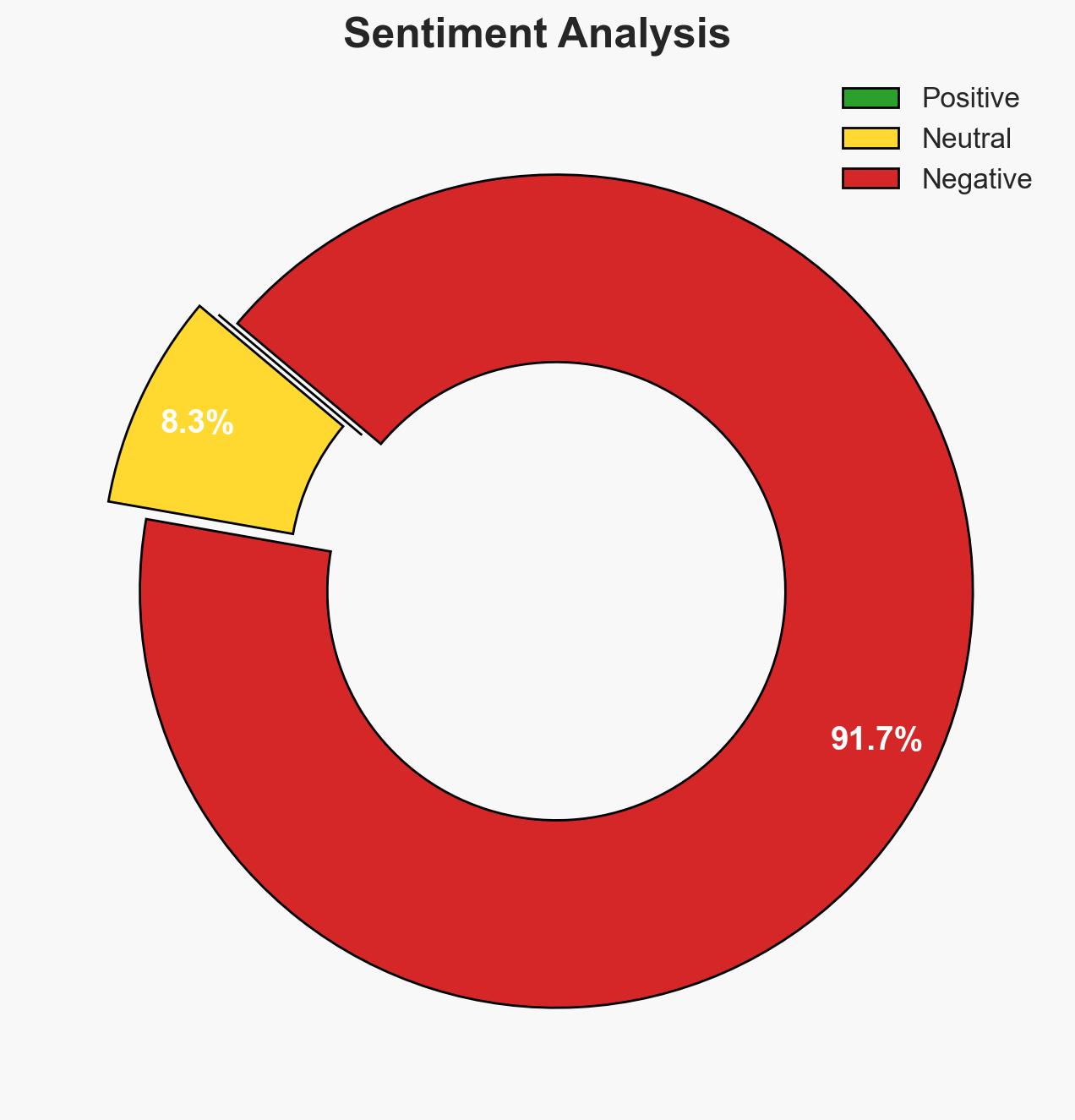
China-linked APT group UNC3886 has conducted a sophisticated cyber espionage campaign targeting Singapore’s telecommunications sector, exploiting zero-day vulnerabilities to gain unauthorized access. The operation, detected by Singapore’s Cyber Security Agency, involved all four major telcos and aimed at critical infrastructure. The campaign has been contained without significant service disruption. Overall confidence in this assessment is moderate, given the ongoing investigation and potential for further developments.
2. Competing Hypotheses
- Hypothesis A: UNC3886 targeted Singapore’s telcos to gather intelligence on critical infrastructure and communications, consistent with their known focus on telecommunications and defense sectors. This is supported by the use of zero-day exploits and advanced persistence techniques. Key uncertainties include the full extent of data exfiltration and potential undisclosed objectives.
- Hypothesis B: The attacks were a broader attempt by China-linked actors to disrupt regional telecommunications capabilities, potentially as a prelude to geopolitical maneuvering. This is less supported due to the lack of significant service disruption and the focus on stealth and data exfiltration rather than operational disruption.
- Assessment: Hypothesis A is currently better supported, as the evidence aligns with UNC3886’s historical patterns of espionage rather than overt disruption. Indicators such as increased regional tensions or further cyber activities could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: UNC3886’s primary objective was intelligence gathering; Singapore’s cyber defenses can mitigate further breaches; the group will continue targeting similar sectors in the region.
- Information Gaps: The exact volume and nature of the data exfiltrated; potential undisclosed vulnerabilities exploited; the extent of UNC3886’s network within the region.
- Bias & Deception Risks: Attribution bias towards China-linked groups; potential underestimation of UNC3886’s capabilities or objectives; reliance on open-source reporting may omit classified insights.
4. Implications and Strategic Risks
This development could lead to increased cyber defense measures in Singapore and potentially provoke diplomatic responses. It may also influence regional cybersecurity collaboration and policy adjustments.
- Political / Geopolitical: Potential strain on China-Singapore relations; increased regional cybersecurity cooperation.
- Security / Counter-Terrorism: Heightened alertness and resource allocation to cyber defense; potential for similar attacks in neighboring countries.
- Cyber / Information Space: Increased focus on zero-day exploit detection and mitigation; potential for retaliatory cyber operations.
- Economic / Social: Minimal immediate economic impact; potential long-term investment in cybersecurity infrastructure.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of telecommunications networks; conduct thorough forensic analysis to identify and mitigate vulnerabilities; engage in diplomatic channels to address potential geopolitical implications.
- Medium-Term Posture (1–12 months): Strengthen regional cybersecurity partnerships; invest in advanced threat detection technologies; develop comprehensive incident response strategies.
- Scenario Outlook:
- Best: Strengthened cybersecurity posture prevents further breaches, leading to increased regional stability.
- Worst: Escalation of cyber activities leads to significant geopolitical tensions and economic impact.
- Most-Likely: Continued low-level cyber espionage activities with gradual improvements in defensive measures.
6. Key Individuals and Entities
- UNC3886 – China-linked APT group
- Cyber Security Agency of Singapore (CSA)
- Infocomm Media Development Authority (IMDA)
- M1, SIMBA Telecom, Singtel, StarHub – Singapore telcos
- Mr. K Shanmugam – Coordinating Minister for National Security, Singapore
7. Thematic Tags
cybersecurity, cyber-espionage, telecommunications, zero-day exploits, China-linked APT, Singapore cybersecurity, critical infrastructure protection, regional security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us