China-Aligned Group Ink Dragon Targets Global Governments with Advanced Malware Campaigns
Published on: 2025-12-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: China-Linked Ink Dragon Hacks Governments Using ShadowPad and FINALDRAFT Malware
1. BLUF (Bottom Line Up Front)
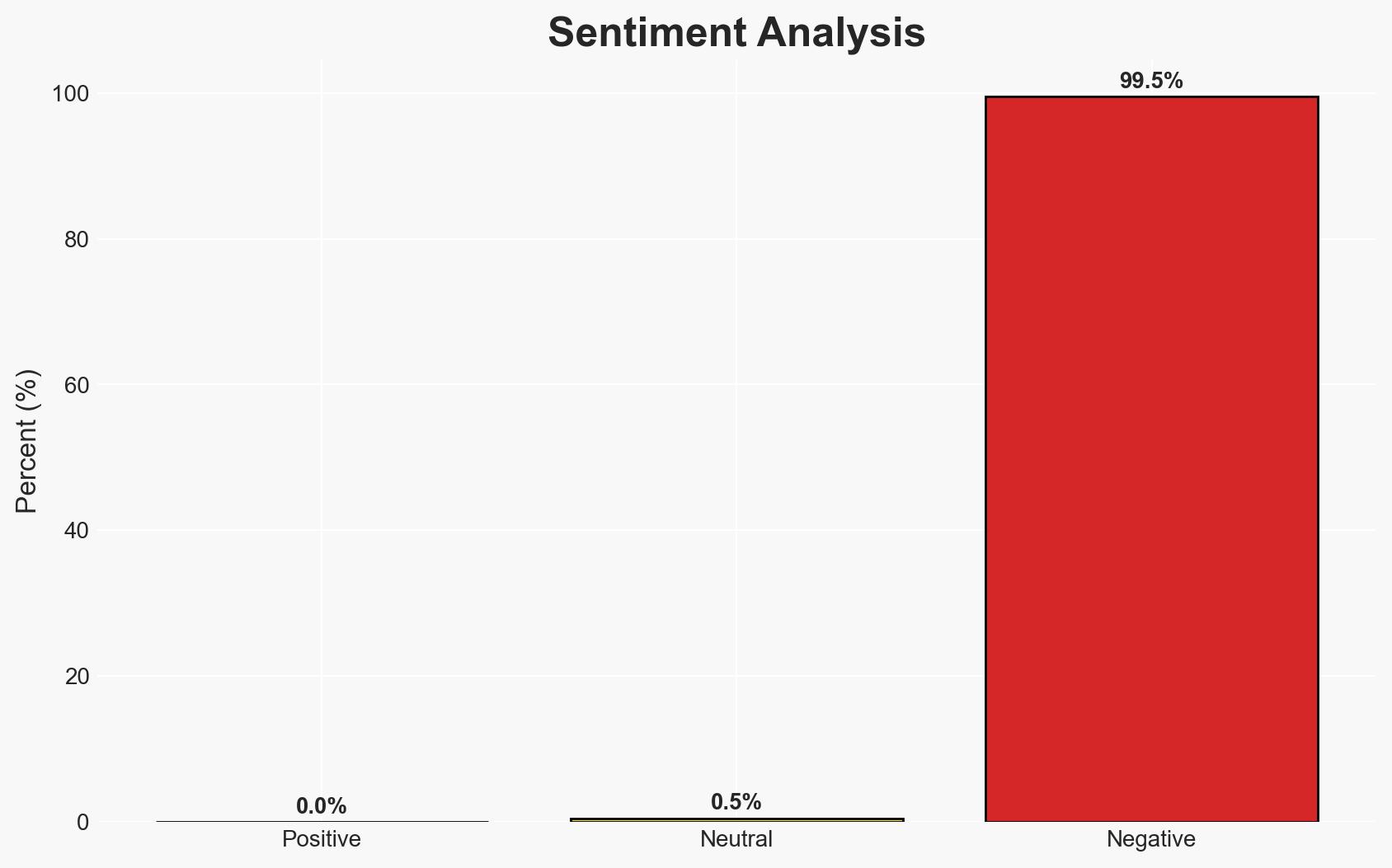
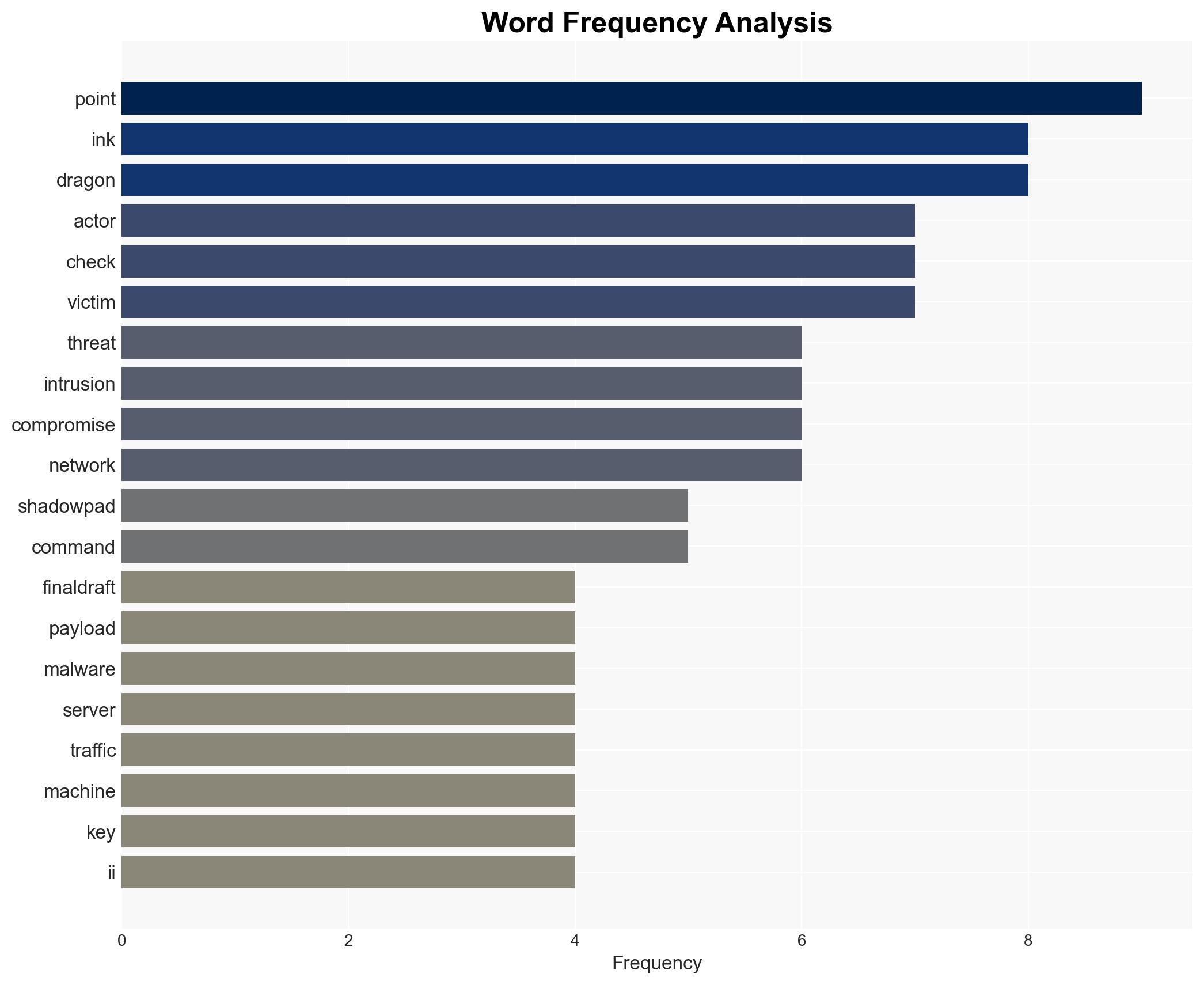
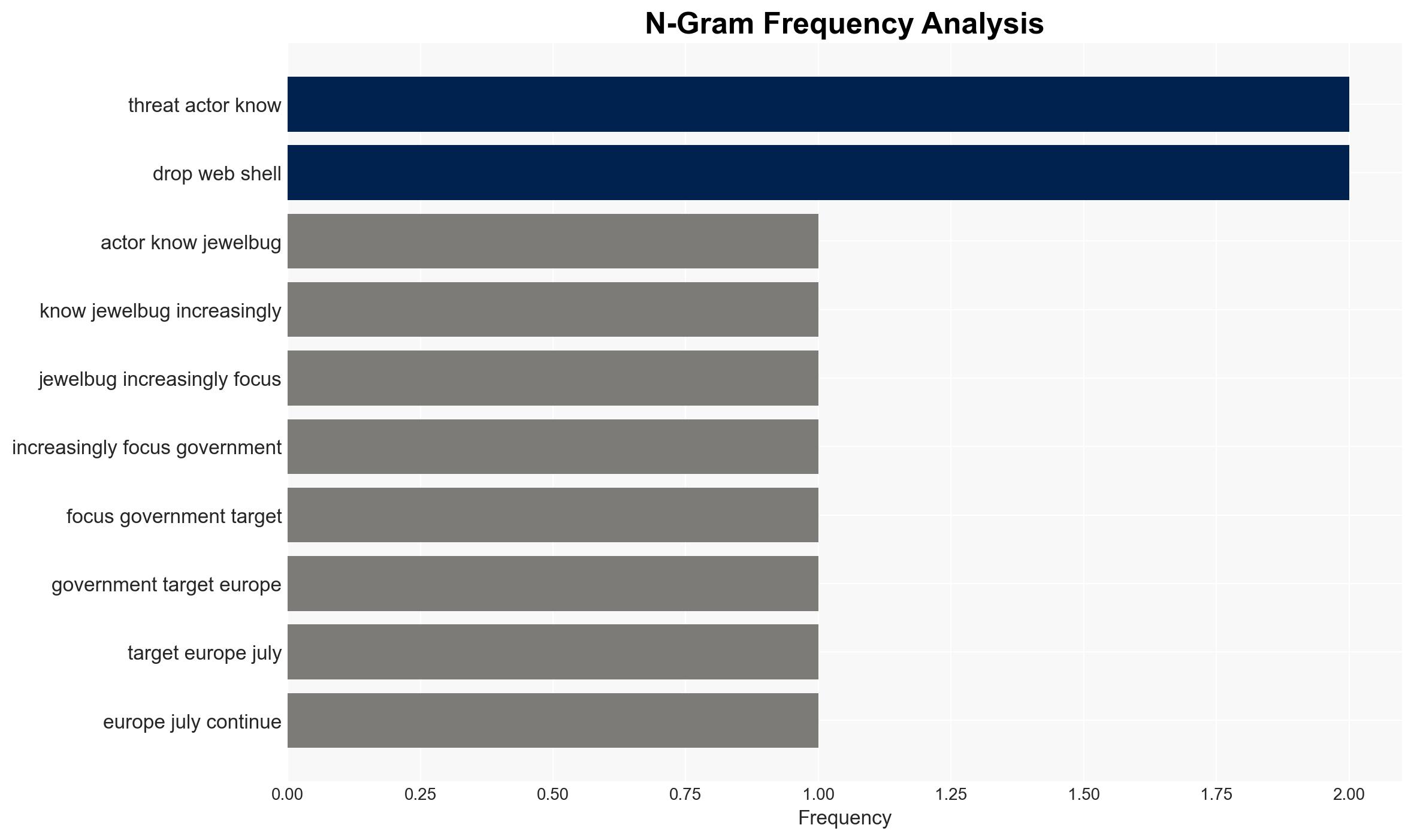
The China-aligned hacking group Ink Dragon, also known as Jewelbug, is actively targeting government and telecommunications entities across Europe, Asia, and Africa using sophisticated malware like ShadowPad and FINALDRAFT. The group’s operations are characterized by stealth and adaptability, posing a significant threat to national security and cyber infrastructure. We assess with moderate confidence that Ink Dragon’s activities are likely to persist and potentially expand in scope.
2. Competing Hypotheses
- Hypothesis A: Ink Dragon is primarily focused on espionage to gather intelligence from government and telecommunications sectors. This is supported by the group’s targeting of government entities and the use of sophisticated malware for data exfiltration. However, there is uncertainty regarding the full scope of their objectives.
- Hypothesis B: Ink Dragon’s activities are a precursor to disruptive cyber operations aimed at destabilizing target nations. While the use of malware like Cobalt Strike suggests potential for disruptive actions, there is limited evidence of such intentions beyond espionage.
- Assessment: Hypothesis A is currently better supported due to the consistent pattern of targeting government and telecommunications sectors for intelligence collection. Indicators such as increased attacks on critical infrastructure could shift this judgment towards Hypothesis B.
3. Key Assumptions and Red Flags
- Assumptions: Ink Dragon is state-sponsored; the group’s primary goal is intelligence gathering; malware deployment is tailored to specific targets.
- Information Gaps: Lack of detailed attribution to specific Chinese state entities; limited insight into the group’s internal decision-making processes.
- Bias & Deception Risks: Potential confirmation bias in attributing activities to China; risk of misattribution due to sophisticated obfuscation techniques used by the group.
4. Implications and Strategic Risks
Ink Dragon’s activities could exacerbate tensions between China and affected regions, potentially leading to retaliatory cyber measures or diplomatic conflicts. The group’s operations may also inspire similar tactics by other state or non-state actors.
- Political / Geopolitical: Increased geopolitical friction and potential for diplomatic fallout between China and targeted nations.
- Security / Counter-Terrorism: Heightened threat landscape for government and critical infrastructure sectors, necessitating enhanced cybersecurity measures.
- Cyber / Information Space: Potential for increased cyber espionage and information warfare activities, complicating attribution and response efforts.
- Economic / Social: Potential economic disruptions due to compromised telecommunications and IT service providers, impacting public trust and stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of government and telecommunications networks for indicators of compromise; share threat intelligence with allied nations.
- Medium-Term Posture (1–12 months): Develop resilience measures, including improved cyber defenses and incident response capabilities; foster international partnerships for collective cybersecurity efforts.
- Scenario Outlook:
- Best: Effective countermeasures reduce Ink Dragon’s operational impact, leading to decreased activity.
- Worst: Escalation of cyber operations results in significant disruptions and geopolitical tensions.
- Most-Likely: Continued espionage activities with periodic escalations, necessitating ongoing vigilance and adaptation.
6. Key Individuals and Entities
- Check Point Research
- Eli Smadja, Check Point Software
- Elastic Security Labs
- Palo Alto Networks Unit 42
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, national security, China, malware, telecommunications, government
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us