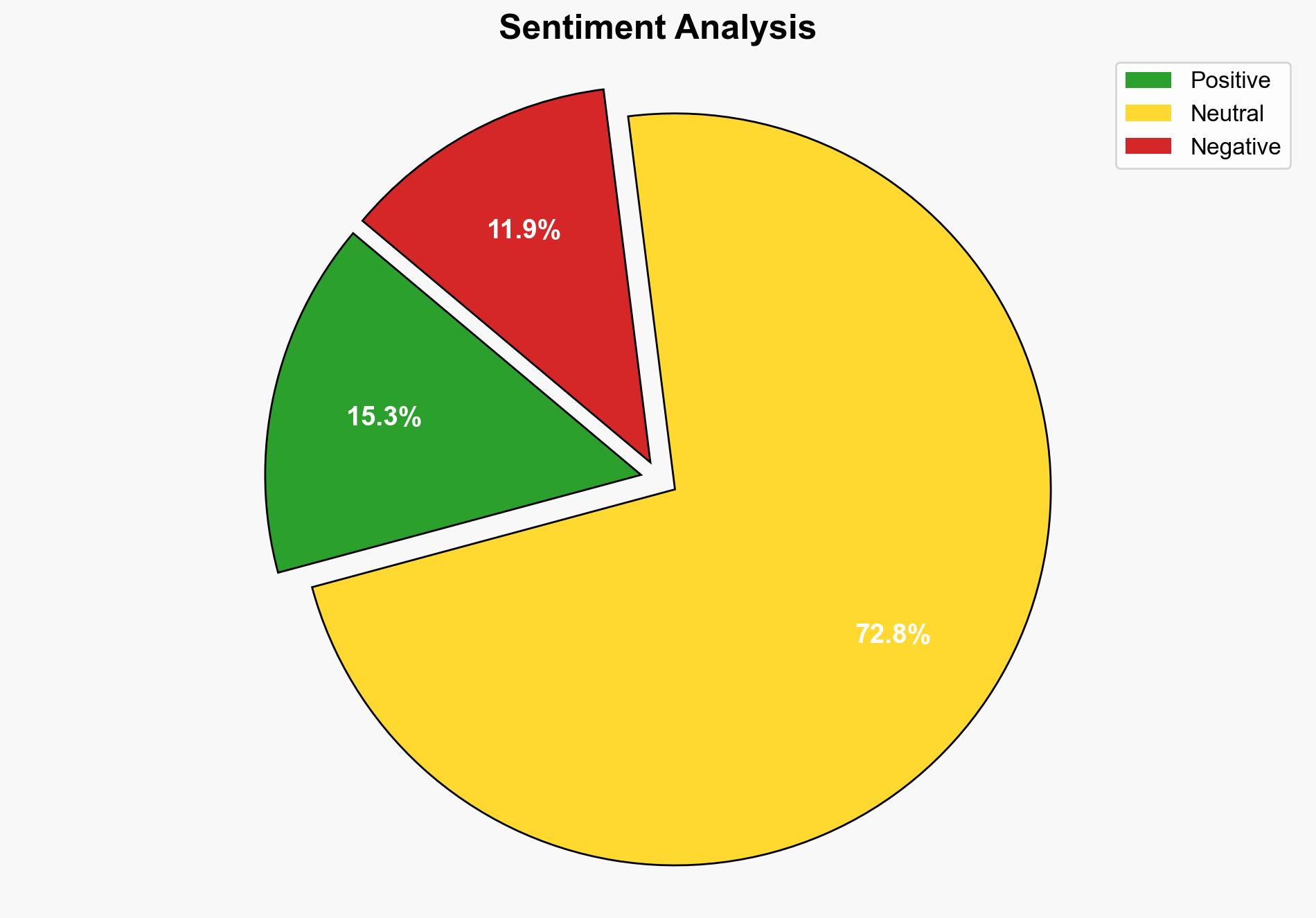
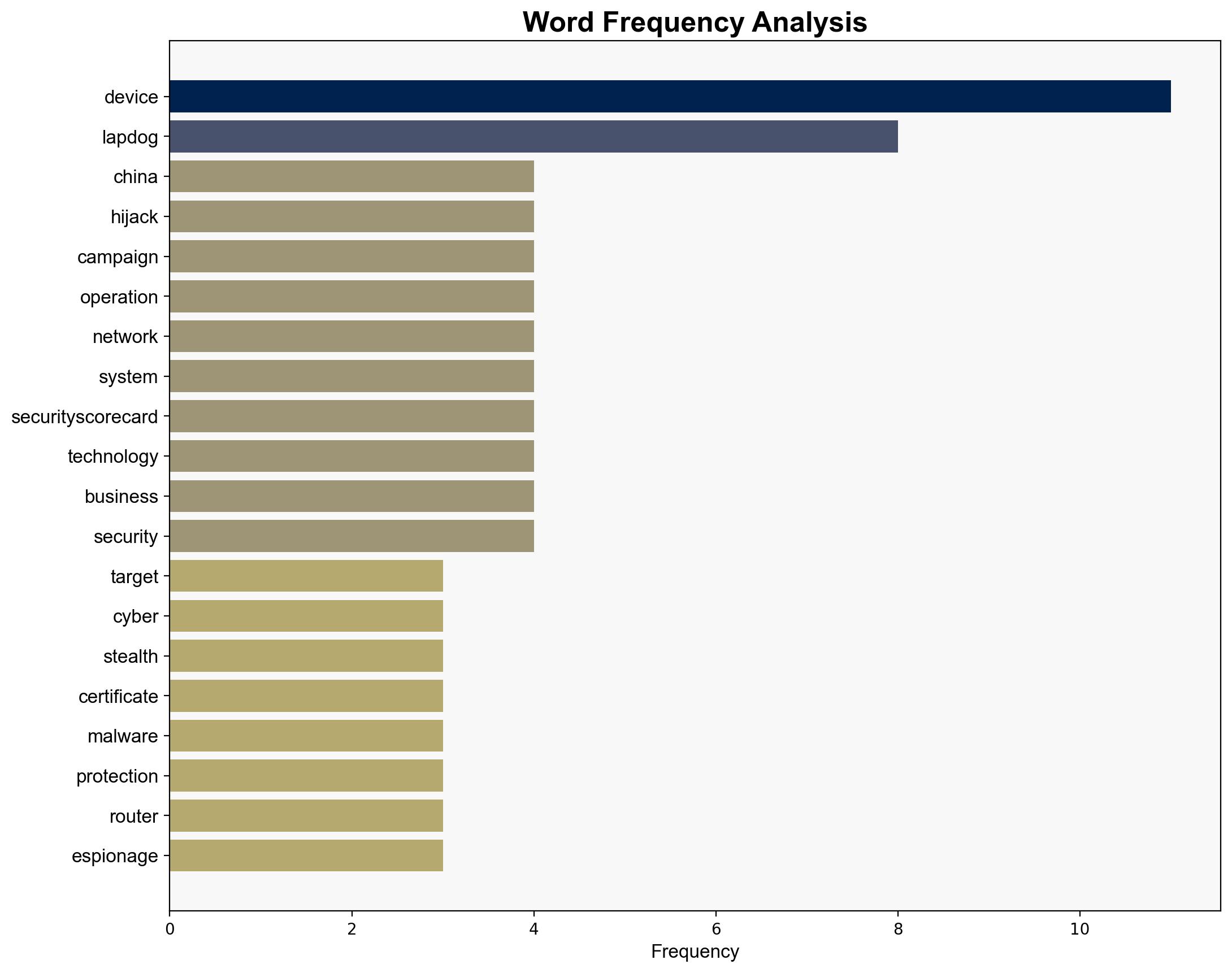
China-backed LapDogs hackers hijacked hundreds of devices in an outlandish intel campaign aimed at US and Asian targets – TechRadar
Published on: 2025-06-29
Intelligence Report: China-backed LapDogs hackers hijacked hundreds of devices in an outlandish intel campaign aimed at US and Asian targets – TechRadar
1. BLUF (Bottom Line Up Front)
The LapDogs cyber espionage campaign, attributed to China-aligned threat actors, has compromised hundreds of devices across the United States and Asia. Utilizing sophisticated techniques such as fake LAPD certificates and custom backdoors, these actors have infiltrated SOHO routers and IoT devices to conduct persistent surveillance. Immediate action is required to enhance network security and review supply chain vulnerabilities.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
The LapDogs operation demonstrates a strategic shift towards leveraging low-visibility devices for persistent access, indicating a need for improved resilience strategies.
Indicators Development
Detection of anomalies such as unusual network traffic patterns and unauthorized certificate usage is crucial for early threat identification.
Bayesian Scenario Modeling
Probabilistic assessments suggest a high likelihood of continued and expanded operations targeting critical infrastructure.
Network Influence Mapping
The campaign’s infrastructure suggests a coordinated effort to maximize influence and impact across targeted regions.
Narrative Pattern Analysis
The use of legitimate-looking certificates indicates a sophisticated approach to disguise malicious activities, complicating threat assessment.
3. Implications and Strategic Risks
The LapDogs campaign poses significant risks to national security and economic stability. The ability to infiltrate and control network devices could lead to data breaches, intellectual property theft, and potential disruption of critical services. The campaign’s sophistication highlights vulnerabilities in decentralized device management and firmware updates.
4. Recommendations and Outlook
- Enhance endpoint protection systems and implement proactive monitoring for unusual certificate usage and network traffic.
- Conduct thorough reviews of supply chain security, focusing on firmware updates and device management protocols.
- Scenario-based projections:
- Best case: Rapid identification and mitigation of vulnerabilities prevent further breaches.
- Worst case: Expanded operations lead to significant data breaches and service disruptions.
- Most likely: Continued low-level infiltration with periodic escalations targeting specific sectors.
5. Key Individuals and Entities
Ryan Sherstobitoff
6. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus