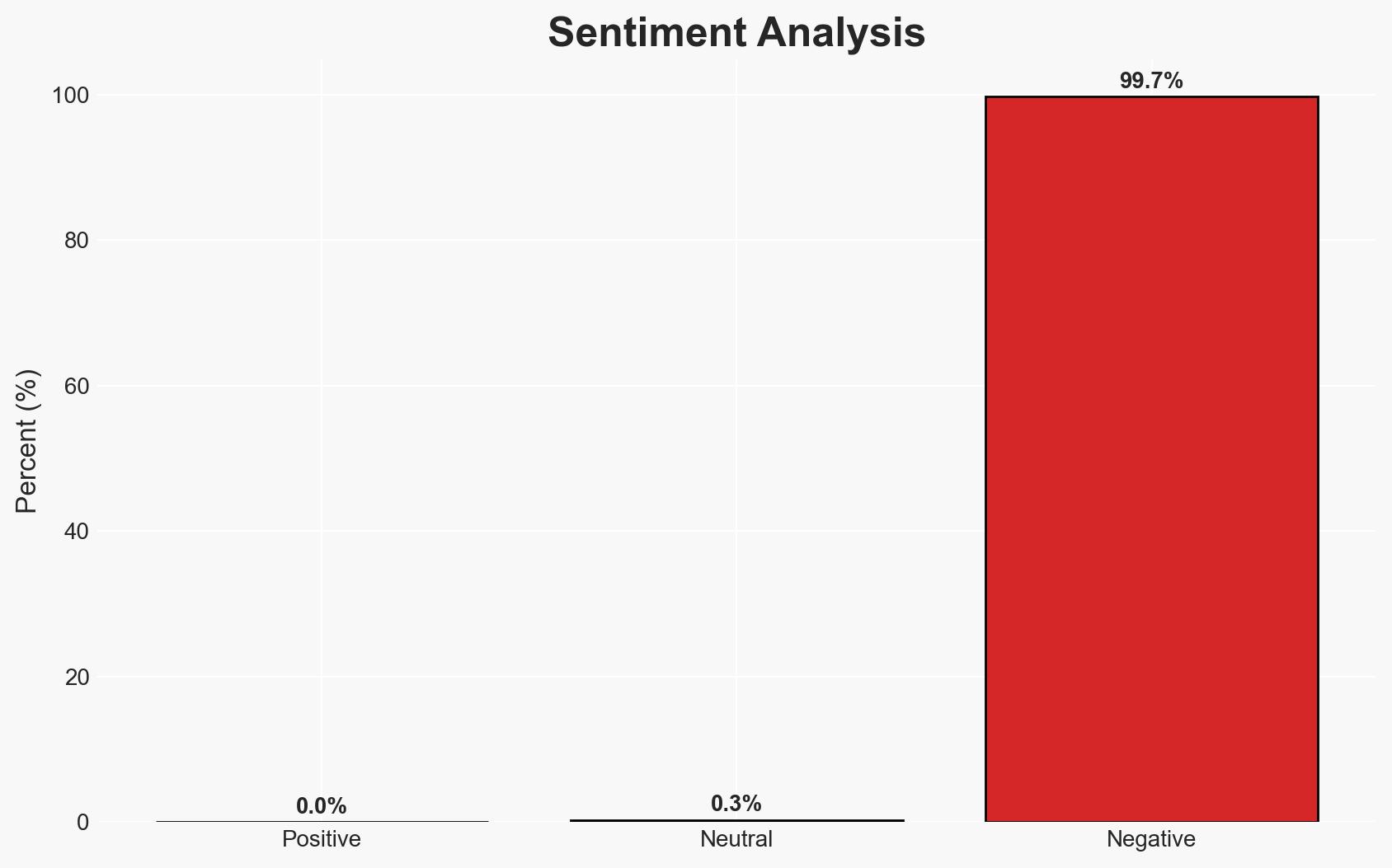
China-linked actors exploit critical zero-day vulnerability in Cisco email security systems
Published on: 2025-12-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Cisco email security products actively targeted in zero-day campaign
1. BLUF (Bottom Line Up Front)
A China-linked threat actor is exploiting a critical zero-day vulnerability in Cisco Secure Email appliances, posing a significant cyber-espionage threat. The campaign involves deploying sophisticated backdoors and tunneling tools, indicating a high level of persistence and capability. The most likely hypothesis is that the campaign is primarily aimed at espionage against strategic targets. Overall confidence in this assessment is moderate, given the attribution to known threat groups and the technical evidence provided.
2. Competing Hypotheses
- Hypothesis A: The campaign is a state-sponsored cyber-espionage operation by China-linked actors, aimed at gathering intelligence from strategic targets. This is supported by the use of sophisticated tools and the involvement of known groups APT41 and UNC5174. However, the exact targets and objectives remain unclear.
- Hypothesis B: The campaign could be a financially motivated operation masquerading as state-sponsored activity, using the attribution to China-linked groups as a false flag. This is less supported due to the technical sophistication and persistence mechanisms observed, which are more characteristic of espionage operations.
- Assessment: Hypothesis A is currently better supported due to the alignment of tactics, techniques, and procedures (TTPs) with known state-sponsored groups. Key indicators that could shift this judgment include evidence of financial gain or changes in targeting patterns.
3. Key Assumptions and Red Flags
- Assumptions: The attribution to China-linked actors is accurate; the primary objective is intelligence gathering; the tools used are exclusive to state-sponsored operations.
- Information Gaps: Specific targets and the full scope of the campaign; potential involvement of other threat actors; detailed impact assessments on affected organizations.
- Bias & Deception Risks: Potential confirmation bias in attributing the attack to known groups; risk of misattribution due to sophisticated false flag operations.
4. Implications and Strategic Risks
This development could exacerbate tensions between the U.S. and China, especially in the cyber domain, and prompt increased scrutiny and defensive measures from affected sectors.
- Political / Geopolitical: Potential diplomatic fallout and increased cyber defense collaboration among U.S. allies.
- Security / Counter-Terrorism: Heightened alert levels and resource allocation to counter cyber threats, possibly diverting attention from other security areas.
- Cyber / Information Space: Increased focus on securing email and communication infrastructures; potential for retaliatory cyber operations.
- Economic / Social: Possible disruptions in sectors reliant on Cisco products, leading to economic impacts and trust issues in technology supply chains.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Agencies should apply Cisco’s recommended fixes, monitor for signs of compromise, and enhance network segmentation and access controls.
- Medium-Term Posture (1–12 months): Develop partnerships for threat intelligence sharing, invest in cybersecurity training, and conduct regular security audits.
- Scenario Outlook:
- Best Case: Rapid patching and mitigation efforts prevent further exploitation, with minimal impact.
- Worst Case: Widespread exploitation leads to significant data breaches and geopolitical tensions.
- Most-Likely: Continued exploitation with gradual containment as patches are applied and defenses are strengthened.
6. Key Individuals and Entities
- APT41 (China-linked threat group)
- UNC5174 (China-linked threat group)
- Cisco (Technology company)
- CISA (U.S. Cybersecurity and Infrastructure Security Agency)
7. Thematic Tags
cybersecurity, cyber-espionage, zero-day vulnerability, state-sponsored threats, China-linked actors, Cisco, network security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us